20/01/20 | Cyber
Ransomware: a bit of history. The dark side of cryptology
For some time now we have been hearing about ransomware: one of the most well-known attacks, perhaps because it consists in putting your hands directly in the wallet of those who fall victim to it ...
1363
Read

13/01/20 | Cyber
USA - Iran, a new hybrid war with an uncertain future
“There is a silent war. The weapons are invisible, the deployments fluid and difficult to identify. It might seem like a novel spy story and yet events like ...
931
Read
06/01/20 | Cyber
USA vs Iran: conventional or cyber conflict?
What is happening in the world these days you can read it in all the newspapers. Without claiming, of course, to be able to read "the truth" about what happens (but then there is a "...
1121
Read

30/12/19 | Cyber
2019 Date Breach Calendar
End of the year. Moments of reflection and also of detachment, albeit brief, from everyday life. Skiing in the beautiful mountains of Val Badia, I find myself remembering the songs of ...
1415
Read
23/12/19 | Cyber
Phishing and Fake News, from your e-mail to governments: when the vulnerability is between keyboard and computer ...
You will have received at least once e-mails in which some figure, an official of an unspecified bank in a random country, asked you for a few thousand ...
519
Read

16/12/19 | Cyber
European cyber security challenge: Italy second in the standings
Interview with Emilio Coppa, Giovanni Lagorio and Mario Polino, coaches of the Italian cyber defender team "TEAM ITALY" made up of students from the training course ...
732
Read

09/12/19 | Cyber
APT 32 hack BMW and Hyundai?
A few days ago the news came that hackers would have hit BMW and Hyundai. The hackers would have infiltrated BMW's corporate network as early as this summer ...
787
Read

02/12/19 | Cyber
Lockheed Martin: some updates on cyber risk analysis
(Sometimes they come back ...) A few months ago we stopped to analyze the cyber risks related to the F-35, this included an analysis of the network (obviously of what it is ...
881
Read

25/11/19 | Cyber
The "shadow warriors" brigade
A few days ago the news about the constitution of the 127th Cyber Battalion of the State Army National Guard ...
2048
Read

18/11/19 | Cyber
The development of the cyber capacity of the Army
The Army Study Center, Center of Thought of reference of the terrestrial military component 1, launches the first ...
940
Read

13/11/19 | Cyber
2019 SECURITY: AI and APT with ONLINE DEFENSE
Today at the Milan-Rho SECURITY fair, see you at the "Cyber Arena" of Pavilion 5, the exhibition area, ...
106
Read

06/11/19 | Cyber
Hacking the hackers! When to fall into the (cyber) canvas is the spider itself ...
In previous articles, cyber-space has often been represented as the far west where the classics are set ...
642
Read

29/10/19 | Cyber
29 October 1969: Arpanet is born, today's Internet
In 1958, US President DD Eisenhower creates the Advanced Research Project Agency, the agency of the ...
1127
Read

28/10/19 | Cyber
Italy: new technologies, training and governance of non-existent risk
Today the computer is in many cases "invisible" at least in the sense of an instrument necessarily constituted by a ...
328
Read

21/10/19 | Cyber
Cyber attack on Iran? The United States says ...
On October 16, Reuters comes out with a sensation article "Exclusive: US carried out secret cyber strike on Iran in ...
1421
Read
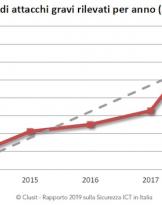
14/10/19 | Cyber
Domestic Security perimeter: companies focus on infrastructure and training
The recent decree law on the cyber security perimeter is the result of new reflections on the evolution of ...
424
Read

07/10/19 | Cyber
HOW-TO: How to build your own "homemade" Firewall
A practical way to save and keep your data safe. In this period when the finances of the companies and ...
12404
Read

02/10/19 | Cyber
Cybertech 2019: many words and many good intentions. But the war has already been going on for years ...
In an important period for digital innovation and growth in Italy and throughout Europe, the Cybertech, as per ...
314
Read

23/09/19 | Cyber
Stories and anecdotes of a computer pioneer
Not quia difficilia sunt non audemus, sed quia non audemus difficilia sunt. (It's not because things are difficult that ...
1140
Read

16/09/19 | Cyber
Cortana, what happens when "le" is asked to try out a mission to the limit?
Cortana, artificial intelligence from Microsoft with a name borrowed from a Halo videogame character ...
1795
Read