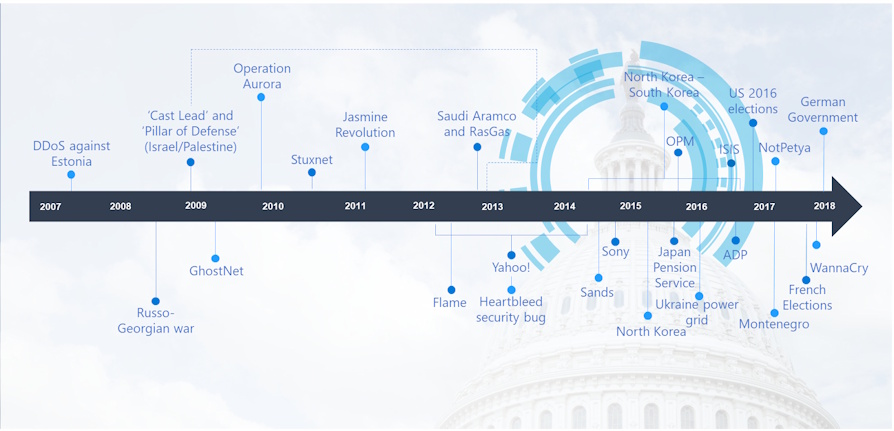
“There is a silent war. The weapons are invisible, the deployments fluid and difficult to identify. It might seem like a novel spy story and yet events like that of the cyber attacks that took place during the last American elections are just some of the most striking episodes of cyber war, a reality halfway between espionage and an act of war. China, North Korea, the United States, Russia, loose dogs, web mercenaries. The scenario is vast and intricate ". This is the description of the book "Cyber War, The upcoming war" by Aldo Giannuli and Alessandro Curioni and it perfectly represents the scenario we are witnessing from 2007 to today.
In this scenario is grafted what we are witnessing in these days between the USA and Iran, that is what we can define a new hybrid conflict that has a clear political matrix. So, following up on what was written a few days ago by Alessandro Rugolo (v.articolo), let's try to investigate, also from a technical point of view, what is happening in these days.
The United States government issued a security warning during the beginning of the year weekend, warning against possible acts of terrorism and cyber attacks that could be carried out by Iran following the killing of General Qassim Suleimani, which took place at Baghdad airport by the U.S. military on Friday January 3. The airstrike that resulted in General Suleimani's death occurred after violent protests and attacks on Iranian embassies by supporters of Iran.
After the killing of General Suleimani, the Iranian leadership and several government-affiliated extremist organizations publicly stated that they intended to take revenge against the United States so much so that the DHS (Department of Homeland Security) said that "Iran and its partners, like Hizballah, they have all the skills to conduct cyber operations against the United States. "
Without a shadow of a doubt, Critical Infrastructures are a primary target and, again according to DHS, possible attack scenarios could include "scouting and planning against infrastructure and cyber targeted attacks against a number of US-based targets."
"Iran has a solid computer program and can carry out cyber attacks against the United States," said DHS. "Iran is capable, at the very least, of carrying out attacks with temporary disruptive effects on critical infrastructure in the United States."
Although United States Secretary for Internal Security Chad F. Wolf said that "there is no specific and credible threat to the country," the alarm raised by the National Terrorism Advisory System (NTAS) also warns that "an attack in the US can occur with little or no warning".
Cyber security companies, such as Crowdstrike and FireEye, believe that future cyber attacks are likely to hit critical US infrastructure, most likely using destructive and data-deleting malware, such as Iranian-sponsored hacker groups they would have done in the past against other targets in the Middle East.
What is perhaps not so well known is the fact that Iranian hacking groups have repeatedly attacked U.S. targets over the past year, although cyber espionage has been the two main reasons (Silent Librarian) and on the other financial grounds through cybercriminal groups (SamSam ransomware group).
Joe Slowik, an ICS malware hunter for Dragos, suggests that the United States should take a proactive approach and prevent some cyber attacks.
"The United States or elements associated with the United States could use this period of Iranian uncertainty to disrupt or destroy the command and control nodes or infrastructure used to control and launch retaliatory cyber attacks, canceling that capability before it can take action," he said. said Slowik in a post on blog published last Saturday.
Downstream of this article, there were no replies from hacker groups referring to the Iranian government although we have seen some low-level cyber attacks that occurred over the past weekend in the form of defacement of some websites.
Among these, the most significant is the official government portal, the Federal Depository Library Program (FDLP). According to an analysis conducted that we describe below, an obsolete installation of Joomla was running on the FDLP portal and it was, most likely, exploiting the vulnerabilities dictated by the lack of update of Joomla itself that the hackers performed the defacement.
In any case, it is fair to point out that these attacks seem to have been carried out by actors not affiliated with the Tehran regime but with a long history of not particularly sophisticated defacement actions dating back to previous years. Attacks appear to be opportunistic and unrelated to planned operations.
For the moment, most of the fallout related to the killing of General Soleimani seems to be limited to the political front. To give an example, the Iranian government announced on Tuesday 7 January that it would no longer respect the limits contained in the Iran-USA 2015 nuclear agreement, from which the US had, however, already withdrawn unilaterally. In addition, the Iraqi parliament also voted to drive US troops out of the country.
Meanwhile, the U.S. Department of State has urged U.S. citizens to leave Iraq immediately as their lives could be in danger and trapped in the midst of conspiracies and terrorist kidnappings. What happened next, with the launch of the Iranian missiles, is, perhaps, only the beginning of something that we would all like to end immediately.
Brief Analysis of the Defacement of FDLP.gov
We are interested, however, in understanding what happened in cybernetic terms and what were the factors that led to the defacement of many American sites. At the time of writing this article, there were already 150. To do so, as anticipated, let's focus on the site http://fdlp.gov/. Allow me, therefore, to start by saying that this defacement is neither a surprise nor, necessarily, does it deserve a great deal of attention but it is an exercise from which you can learn many things about the culture of defacement and from which you can draw interesting ideas for future research.
The defacement is of extreme simplicity. The attackers uploaded two images and obscured the rest of the page. They added the standard bit "lol u get Owned" at the bottom of the page and, once the page on the site was modified, they dedicated themselves to launching automatic defacements towards other sites thanks to SQL Injection techniques.

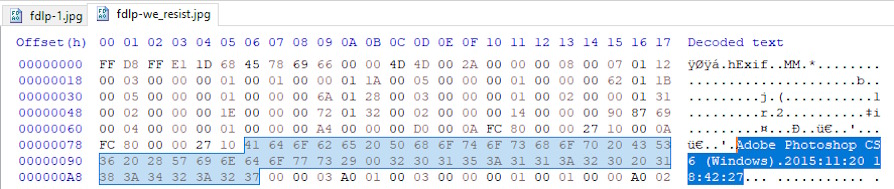
What turned out to be really interesting is the fact that there was EXIF type data in "we_resist.jpg" which indicates that it was created in 2015 with Adobe Photoshop CS6. The image immediately below, the one with Donald Trump (1.jpg), however, did not have this kind of data. Since almost all major image hosting sites and social media sites remove this data, this fact in itself. It represents an interesting anomaly.
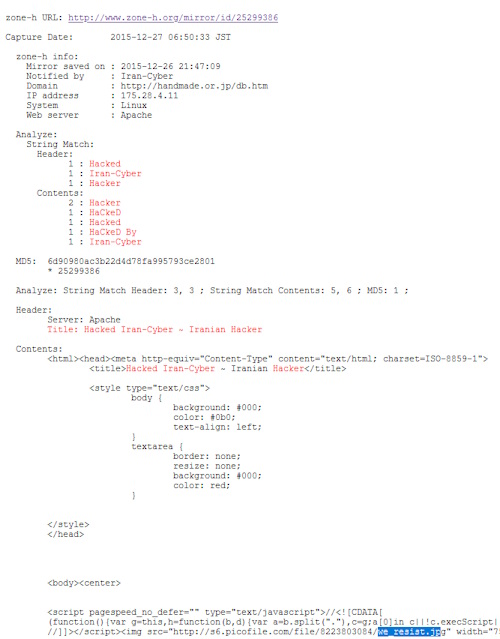
By doing a little research in relation to the name of the image, a "izumino.jp" site emerged. This site focuses on the collection of metadata extremely relevant for defacement activities and, therefore, has allowed us to discover that the name of the image was present in the source code of a previous defacement.
The image was originally uploaded to a Persian language image hosting site where it is still available (http://s6.picofile.com/file/8223803084/we_resist.jpg). The image was used for the first time in 2015 in a violation of the supersexshop.com.br site and subsequently on other sites. These defacements have been reported in a defacement ranking known as Zone-H by "IRAN-CYBER" which contain around 2.447 defacement "notifications" dating back to the end of 2015. It is worth noting that nobody has claimed the FDLP defacement on Zone -H.
Ever since the year it was created in 2008, FDLP.gov has always been a Joomla-based site. The code has been modified over the years with a model change in 2014 and different plug-ins that have been implemented over the years. However, when looking at the latest source code, before the defacement, it appears that many plug-ins, such as MooTools, and external dependencies, such as Bootstrap, have not been updated since 2012.

Now that we've determined that much of the code hasn't been updated since 2012, let's take a look at the plug-ins and various components. Navigating between the two pages we highlight the following:
media / com_rsform
media / com_hikashop
media / mod_rsseventspro_upcoming
modules / mod_djmegamenu
plugins / system / maximenuckmobile
The shocking thing is that one of these strings was made without security criteria and, therefore, with the ability to accept and publish any changes made by any user, without any administrative privilege.
If we take a look at the RSForm what is evident is that this was present since 2014 on the fdlp.gov/collection-tools/claims page and that the current version had vulnerabilities known for over a year and a half as reported by KingSkrupellos.
In short, to finish, unfortunately, the whole world is a country.
Note:
defacing - English term which, like its synonym defacement, has the literal meaning of "scarring, deface", in Italian rarely rendered with deface) in the field of IT security usually has the meaning of illegally changing the home page of a website ( its "face") or modify, replacing them, one or more internal pages. Practice which, conducted by unauthorized persons and unbeknownst to those who manage the site, is illegal in all countries of the world.
A site that has been subject to this type of deface has its main page replaced, often together with all the internal pages, with a screen indicating the action performed by one or more crackers. The reasons for this vandalism can be of various types, from the demonstration of ability to ideological reasons. The techniques used to obtain write access permissions to the site usually exploit the bugs present in the site management software or in the underlying operating systems; the case of the use of social engineering techniques is rarer.
Sources:
https://www.zdnet.com/article/dhs-iran-maintains-a-robust-cyber-program-...
https://www.proofpoint.com/us/threat-insight/post/threat-actor-profile-t...
https://www.justice.gov/opa/pr/two-iranian-men-indicted-deploying-ransom...
https://pylos.co/2020/01/04/assassination-retaliation-and-implications/
https://medium.com/@ Sshell_ / brief-analysis-of-the-DFLP-gov-deface-980caba9c786












