30/07/18 | Cyber
Unit 8200: the elite of cyber warfare and the "engine" of Israeli high technology
What can the famous legend of David and Goliath, also reported in the Bible, have in common with the intelligence unit of the Israel Defense Forces (IDF), known by the name in ...
3588
Read

28/07/18 | Cyber
The COSCO Group under Cyber attack
To be under attack Cyber these days is one of the largest logistics and shipping companies in the world, the China Ocean Shipping Company (COSCO), based in Beijing. So...
1451
Read

23/07/18 | Cyber
Singapore: cyber attack on health information systems
Singapore, a city-state at the center of the economic and financial world, at the top of the ranking published by the World Economic Forum in the Global Information Technology Report of ...
597
Read

16/07/18 | Cyber
Germany also has its fourth armed force
Some will recall that last summer President Trump announced the promotion to Unified Combatant Command of USCYBERCOM, giving the highest recognition ...
2278
Read

04/07/18 | Cyber
After Japan also Romania announces entry into the Cyber Defense Center of Excellence in Tallinn (CCDCOE)
The news was published last June 15 on the CCDCOE website. The official announcement was made during a visit by the Prime Minister of Romania, Mrs. ...
443
Read

30/06/18 | Cyber
Video surveillance for mass events, concrete help to law enforcement agencies
In recent years, Europe has been the scene of news events that have caused numerous victims, hardships and insecurity in the social fabric. Terrorist attacks and other actions ...
733
Read

19/06/18 | Cyber
USA and Thailand: the use of reserve personnel in the Cyber environment
How should the now constant danger arising from the fifth dimension known as cyberspace be faced militarily? Someone has posed the problem for some time and ...
367
Read

13/06/18 | Cyber
"The art of war is to defeat the enemy without having to face him". Unit 61398: Win without firing a shot
At the time when he developed his own theories on "The art of war", Sun Tzu certainly could not have imagined the reality of our days. Today, now, next to ...
2722
Read

06/06/18 | Cyber
Cybersecurity (for insiders): analysis of a threat on Hadoop systems and not only ...
NOTICE TO READERS: THIS ARTICLE IS INTENDED FOR CYBERSECURITY PROFESSIONALS. DO NOT RESTORE PUBLISHED LINKS ...
1691
Read

07/05/18 | Cyber
Cyber and Japan: CCDCOE's entry into the club announced
The news came last January that Japan is preparing to join the cyber club of Tallin as a state ...
750
Read

30/04/18 | Cyber
The Russian Cyber doctrine: 646 decree of the 5 December 2016
The 5 December 2016, with the decree n. 646 signed by the President of the Russian Federation, the Cyber doctrine is renewed ...
1022
Read

27/04/18 | Cyber
The 2018 Locked Shields ended today. the largest and most advanced international Cyber Defense exercise in the world
The 2018 Locked Shields exercise was organized by the NATO Center of Excellence for Cyber Defense (...
575
Read
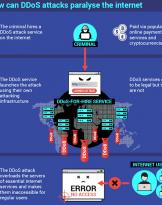
27/04/18 | Cyber
The WebStresser website closed for hacking activities
The WebStresser.org website was deactivated yesterday as a result of a joint operation by the Dutch police, ...
847
Read

26/04/18 | Cyber
Codemotion 2018: when Rome hosts the future ...
Codemotion has been the largest technical conference dedicated to software developers in Italy for years. Held in the ...
259
Read

22/04/18 | Cyber
Fourth industrial revolution: Internet users from all over the world ... you are already united!
Every evolutionary leap in human society is characterized by a discriminating factor that uniquely identifies it ...
1109
Read

17/04/18 | Cyber
Jeff Boleng will handle the software for the F 35 Joint Strike Fighter for the DoD
13 April 2018: a special piece of news comes out in the Washington Business Journal, "The Pentagon has created a new post to ...
450
Read

16/04/18 | Cyber
The deadly cyber-claws of the Russian bear strike both military and civilian targets. Fancy Bear's unstoppable rise to cyberspace
The universe of hacker groups is extremely vast and varied. As mentioned in the previous articles, while those “...
1699
Read
12/04/18 | Cyber
Oracle and R1 Group present: Beyond Bitcoin
In recent months the rapid increase (and partial decline) in value of many crypto-coins has resulted in heated ...
763
Read

10/04/18 | Cyber
Locked Shield 2018 to the starting blocks!
Also this year in Tallin (but indeed throughout Europe) the largest Cyber exercise will be held as usual ...
667
Read

04/04/18 | Cyber
Meltdown: considerations on the impact on classified systems
Meltdown, a term whose meaning is synonymous with "disastrous collapse", or "nuclear catastrophe" has entered ...
886
Read