04/01/21 | Cyber
2020: a year of hacking
Cyberspace is the most complex thing man has ever built: on the one hand, it represents the union of thousands of networks that make it difficult even to have a photograph ...
1349
Read

28/12/20 | Cyber
IMD WORLD DIGITAL COMPETITIVENESS RANKING 2020: Italy in 42nd place
Still an achievement to forget! This time it is a Swiss organization saying it, the International Institute for Management Development, IMD for short. IMD, born ...
1208
Read

21/12/20 | Cyber
Sunburst: a Pearl Harbor Cyber?
In a few years, when the current terrible pandemic is finally under control, 2020 will not be remembered only for the explosion of the COVID-19 infection and its ...
1794
Read

14/12/20 | Cyber
FireEye hacked, by whom?
The US company FireEye, cyber security giant, recently reported having been the victim of hackers, probably supported by a state. Let's remember ...
894
Read

14/12/20 | Cyber
Little Red Riding Hood and Climbing Beyond the Cloud (How to Become a Hacker)
"Once upon a time there was the real world ..." In a hundred years with this premise we will tell a story to make our great-great grandchildren go to bed. We will start by talking about a dessert ...
1310
Read

07/12/20 | Cyber
Quantum Supremacy to China?
We have long been talking about the evolution of quantum technology applied to computers and cryptographic algorithms. Three years ago we spoke in a ...
1876
Read

30/11/20 | Cyber
Cloud and Confidential Computing ...
For years, cybersecurity experts from private companies and public organizations have been faced with the innovative thrust of new services, generically identified ...
659
Read

23/11/20 | Cyber
Microsoft Pluton, for a safer world
A few days ago Microsoft presented its latest novelty to the world: Microsoft Pluton. Announced in collaboration with leading Silicon processor manufacturers ...
1451
Read

16/11/20 | Cyber
Cyber: has Russia attacked Norway?
Cyberspace is increasingly a territory of conflict, it is now possible to realize this every day, it is no longer talked about ...
1180
Read

09/11/20 | Cyber
Project Ares: cyber and gamification
Research in the cyber field is increasingly pushed and touches all aspects of the fifth domain. Training is one of ...
801
Read

02/11/20 | Cyber
American elections: Trump's website hacked
We are in time of American elections, in a few days it will be known who will lead the first world power and, of ...
504
Read

26/10/20 | Cyber
The TIDoS Framework
For Kaly Linux lovers, Metasploit is the framework used to perform Penetration Testing activities ... In the ...
336
Read

19/10/20 | Cyber
Botnets: one of the biggest threats in cyberspace
Cybersecurity is a shared responsibility, which affects us all. We must start from this assumption of ...
2131
Read

12/10/20 | Cyber
Cyber US-Russia truce ... what if it goes through operations against Trickbot?
According to the Washington Post, the US Cyber Command in recent days has been engaged in an operation ...
865
Read

05/10/20 | Cyber
Microsoft - the importance of security and privacy in the time of Covid
“Microsoft's goal is to democratize access to technology so that everyone can benefit from it, ...
282
Read
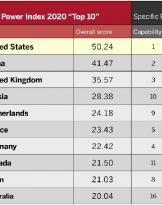
28/09/20 | Cyber
The United States first in the world in the cyber field
This, in summary, is what is stated in the National Cyber Power Index (NCPI) 2020 of the Belfer Center for Science and ...
2162
Read

14/09/20 | Cyber
The Chief Information Security Officer, what skills?
For many cybersecurity professionals the ultimate career goal is to take on the role of ...
697
Read

07/09/20 | Cyber
INTEL launches the new generation of Tiger Lake processors
On September XNUMX, Intel announced the release on the market of the new generation of processors, the eleventh, ...
1280
Read

31/08/20 | Cyber
How to compete in Cyberspace: the new approach
On 25 August 2020, on Foreign Affairs, a very interesting article was published, signed Nakasone and Sulmeyer ....
709
Read

10/08/20 | Cyber
Trickbot: the most widespread trojan in COVID 19 campaigns
Trickbot malware belongs to the family of spyware Trojans, mainly used against industry targets ...
848
Read