19/04/24 | Cyber
Biden establishes the figure of CAIO (Chief Artificial Intelligence Officer)
Last March 28, Memorandum M-24-10 was issued, the subject of which is: "Advancing Governance, Innovation, and Risk Management for Agency Use of Artificial Intelligence". The...
665
Read

11/04/24 | Cyber
The XSS threat and the role of the WAF
Among the cyber attacks that exploit script injection methodologies, Cross Site Scripting (XSS) is certainly one of the most famous and in this short article I will try to...
308
Read

05/04/24 | Cyber
How to trick defenses to do a SQL attack with JSON
As we have seen previously, SQLi are still fearsome despite their age. If anyone has missed the basic information on SQLi I advise them to take a look at...
277
Read

02/04/24 | Cyber
What's happening in the Linux community: xz backdoor, trust attack!
Just three days ago, on March 29, 2024, a new attack was discovered: it affected open source software that is part of the main Linux packages, XZ...
1565
Read

02/04/24 | Cyber
The risks of online exposure: the role of Open-Source Intelligence
The current world is increasingly oriented towards the digitalisation of assets, such as currencies, physical and intellectual properties, smart contracts and, more generally, data. The...
851
Read

25/03/24 | Cyber
“John The Ripper”
John The Ripper, not to be confused with "Jack the Ripper" (Jack the Ripper, so to speak) is an Open Source tool for auditing (controlling) password security and...
939
Read

19/03/24 | Cyber
AI and Cyber: what programming skills are needed?
As banal as it may seem, programming was born in response to the request to have machines perform tasks: humans needed a simple interface to...
541
Read

13/03/24 | Cyber
Security Summit 2024 is coming!
The main event of the cybersecurity panorama in Italy will be held in Milan between 19 and 21 March: the Security Summit. Organized over three days of conferences,...
170
Read

11/03/24 | Cyber
SQL Injection: always current despite its age
A few weeks ago I published an article entitled: "SQL Injection attack: what is it?", thinking...
955
Read

06/03/24 | Cyber
Cyber and Artificial Intelligence in military applications
“The Russian-Ukrainian war, the Israeli conflict against Hamas” stated the Undersecretary of State for Defense...
237
Read

04/03/24 | Cyber
Cloudflare hacked: why and by whom?
News of the Cloudflare hack came out at the beginning of February. In the titles of the magazines we read...
1724
Read
26/02/24 | Cyber
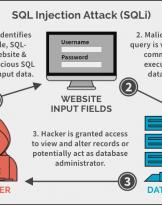
SQL Injection Attack: What is it?
How many times have you heard about SQL Injection and promised yourself to understand what it is, without then having...
886
Read

19/02/24 | Cyber
What is meant by Digital Forensics
In today's world we hear more and more often about cyber incidents, hackers and APT groups. In this context...
425
Read

12/02/24 | Cyber
The importance of data integrity
What is File Integrity Monitoring? What tools are used nowadays? Two questions that require...
294
Read

08/02/24 | Cyber
What is a Web Application Firewall
A Web Application Firewall, WAF for friends, is a security application that protects...
653
Read

25/01/24 | Cyber
How the AI Act will regulate Artificial Intelligence in the EU and what impact it will have
“When the results are announced, Lee Sedol's eyes well up with tears. AlphaGo, an intelligence...
999
Read

26/12/23 | Cyber
Happy Cyber 2024
Last days of December, 2023 ends and usually it's time to take stock of the year that is coming to an end but I'm going...
643
Read

15/12/23 | Cyber
Eng. Davide Ariu (Pluribus One): "We need excellent software engineers"
As usual, we continue the series of interviews with Italian companies operating in the world of cyber and more...
887
Read

08/12/23 | Cyber
The FSB has been engaged in cyber attacks against the UK for years
The UK has accused the FSB of a long-running cyber hacking campaign. The British government accused the Russians of...
1286
Read

01/12/23 | Cyber
National and Technological Security: reflections on the French ban on using WhatsApp
The French government's recent initiative to ban the use of WhatsApp and other foreign messaging apps by...
2255
Read