02/01/19 | Cyber
Global Cybersecurity Index 2017: Italy at 31 ° place ... downhill?
Every year the International Telecommunication Union, a UN agency specialized in ICT, takes the trouble to measure the level of IT security in the member countries. For...
675
Read

26/12/18 | Cyber
Cyber-weapons: for US Defense are weapons of mass destruction?
According to the well-informed Mark Pomerlau, the US DoD wants to explore the relationships between cyber and weapons of mass destruction. In an article that appeared a few days ...
1493
Read
15/12/18 | Cyber
Saipem under cyber attack
Let's start with the facts: Monday 10 December 2018, the Saipem (Italian Society of Perforations and Assembling), an Italian company present around the world with about 32.000 ...
1790
Read

12/12/18 | Cyber
Cyber: Undersecretary Tofalo, strengthen Armed Forces capacity to protect the country system in the cybernetic domain
"My mission is to strengthen the capabilities of our Armed Forces in guaranteeing the protection of the country system in the cybernetic domain and, consequently, in rendering them ...
336
Read

08/12/18 | Cyber
Launched CLIP OS, the French Open Operating System
The 5 and 6 December, in Paris, took place the fourth edition of the "Paris Open Source Summit", continues unceasingly in France the change in the computer world and the ...
1128
Read

30/11/18 | Cyber
Marriott international: stolen data from 500 millions of customers
The Marriott international, an American multinational, this morning admitted that it was hit by a hacker attack that compromised 500's millions of customers ...
481
Read

20/11/18 | Cyber
Italy under attack
Italy has long been the target of hackers, yet, until yesterday it seemed that nobody was interested. But this time it's different. Already for some days ...
4456
Read

12/11/18 | Cyber
IBM and NVIDIA Tesla supply the Sierra Super computer to the Lawrence Livermore National Laboratory
The world of American defense is rich in research institutes, among which, of primary importance, we can mention the Lawrence Livermore National Laboratory, Research Institute ...
1017
Read

05/11/18 | Cyber
Information War: Microsoft's role between the US and India
A few days ago, on DNAIndia.com, a newspaper published in Mumbai in English, the news that the ...
653
Read

29/10/18 | Cyber
What to do if Linux is also insecure?
Among the few certainties that I have always had about operating systems I can certainly mention "Linux is better than ...
4485
Read

22/10/18 | Cyber
Clusit 2018 Report: in Italy the situation is serious
Also this year the "Clusit Report" was issued, drawn up by the "Italian Association for Security ...
767
Read

15/10/18 | Cyber
Are US weapons systems vulnerable to cyber attacks? So it seems according to ...
If you just read the news on cyber space (and related attacks) you are led to think that these problems ...
2119
Read

08/10/18 | Cyber
Press and GDPR: the importance of the security of paper documents
The entry into force of the General Data Protection Regulation (GDPR) last 25 May, has finally ...
1629
Read

09/09/18 | Cyber
6 September 2007: Orchard operation
In the 2007 in Italy there was just talk of cyber. Someone dared to write their thesis trying to ...
1850
Read
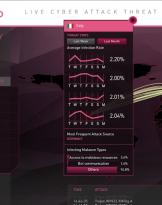
04/09/18 | Cyber
Live Cyber Attack Threat Map
Check Point Software Technologies Ltd. is one of the largest Israeli computer companies. Founded in 1993 by ...
2649
Read
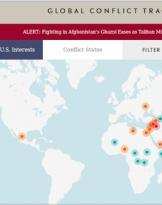
03/09/18 | Cyber
Global Conflict Tracker: a quick guide on wars and American interests
It may happen that you need real-time information on a conflict or on the interests of a state, ...
1810
Read

29/08/18 | Cyber
Talos intelligence map
One of the open tools that can be used to explore the cyber dimension is Talos. I talked about ...
1923
Read

24/08/18 | Cyber
Investing in the Israeli cyber? Let's take a look at startups ...
In today's world, that characterized by the invasive and almost oppressive presence of the fifth dimension (the ...
874
Read

20/08/18 | Cyber
Kaspersky cyber-threat real time map
Kaspersky is a Russian computer security company, at the center of several controversies in recent times as ...
2953
Read
01/08/18 | Cyber
Undersecretary Tofalo visits the C4 Defense Command and the Interforces Command for Cybernetic Operations
The Undersecretary of State for Defense Angelo Tofalo today visited the C4 Defense Command, established on May 20 ...
967
Read