You will have received at least once e-mails in which some figure, an official of an unspecified bank in a random country, asked you for a few thousand dollars to unlock a practice by which you would have found millionaires from a moment to moment.
These types of emails are commonly marked as spam and they are an example of how attackers try to exploit the greatest vulnerability of a computer system, namely the human being.
This type of attack is called "Phishing”, Or the attempt to exploit the credibility of a name or logo to induce the victim to provide personal or credential information, which is collected by the attacker and exploited or resold.
Il Phishing it is not a proprietary IT technique, think for example of scams against the elderly, where the attacker pretends to be an employee of the company providing a service to be able to enter the house, or to be provided through the deception secret code shown on the bill.
In the IT field, the Phishing it is widely used not only to steal banking or social credentials, but also to propagate malware (this type of technique is called "malspam").
Usually, also because of normal human emotions, we tend not to give weight to Phishing, or we tend to think that "I am so immune to it ... I can recognize it".
Well, the advice is to always be suspicious, and never take these attack attempts lightly, as some can be very elaborate.
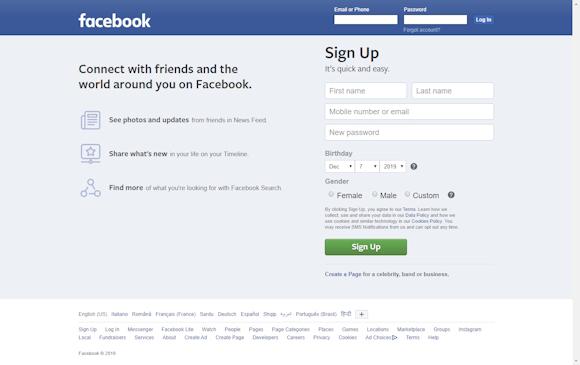
Take, for example, this page (aperture image - links: https://loremitalia.altervista.org/testp/):
This is a "pixel-perfect" copy of the Facebook home page, created specifically for me for this article.
If at this moment I launched a campaign of Phishing targeted to American users of the famous social Network, how many victims could I do?
I also wanted to publish a demonstration (even if it is only a facade, I obviously did not insert any data capture function) to also demonstrate the simplicity of such an attack.
To produce a similar attack it was enough:
- Retrieve the "assets" from the site (about 30 seconds).
- Modify the HTML code to a minimum to make it compatible, visible and "navigable" outside the Platform servers (about 60 seconds).
- Upload it to a hosting (about 15 seconds).
- Change the htaccess (we'll see what it is - about 20 seconds later).
For those who perform attacks like this "for business", inserting a data backup function takes a maximum of 10 minutes.
Practically, going calmly and taking care of the "content", an expert "phisher" can build a successful campaign in a quarter of an hour.
With a similar technique, campaigns can also be created for web applications created with framework modern like Angular, React o View.
THE.htaccessit also does just that.
I framework aforementioned were created to facilitate developers in creating applications that immediately work as multi-platform applications, on different devices, and that immediately support a "responsive" design, that is, they immediately adapt to screens of various formats and sizes.
Given their structure, the applications are executed directly in the browser, thus avoiding onerous work by the servers.
The component that allows the application to work is called "service workers".
The structure of applications created with gods framework it can be very complex and structured in various sub-folders.
Obviously the phisher he cannot always reproduce the service worker perfectly (almost never to tell the truth), so he works to download the "assets" from the site.
The "assets" are CSS and Javascript files (CSS is a language that describes how a site's graphics should be displayed - it can be compared to a "graphic engine" for web pages, while Javascript allows the various components to work, to example i pop-up that appear on the sites to make us accept i cookies).
The set of HTML, CSS and Javascript allows the site to function exactly as it should, so once the phisher has these components, the application structure and the home page to display, it does not have to do anything other than load this "simulated structure" inside a hosting and change the.htaccess.
The file ".htaccess"(the dot in front is not an error), is a configuration file that says ad Apache (a web server) how a folder or an entire PHP application should work.
PHP is a programming language for the web that allows you to create applications that, unlike the framework above, is "server-side", ie all operations are performed by the server and not from browser.
Apache supports PHP applications, and through the ".htaccess" file the phisher he says to Apache where to get the home page.
In this way, however complex the structure of the application, the phisher he can respect it, being able to "reproduce" any page he wants (avoiding any graphic error).
Such an attack is very difficult to avoid if you are not particularly careful, but if you are in front of your computer, you can still check the browser address.
For this demonstration, for example, you can read it https://loremitalia.altervista.org/testp/ which of course is not the Facebook address.
But can we really feel safe simply by checking the link?
In general, the advice is to always pay attention to what data you are entering and where, but it is not always so simple.
It is possible to notice a data theft, since in most cases once the credentials have been entered, the User is redirected to an error page, this is because the rest of the structure of the website and the information the user should access are not (yet) known for which they cannot be reproduced.
In case you don't realize that you have fallen into the trap, the consequences can be serious: usually the goal is the theft of personal or industrial data, the theft of bank details or (via malspam), infect the User's device to make him unknowingly make an "accomplice" of the criminal (a network of this type, formed by "zombie" PC controlled by the attacker remotely, is called "botnet").
Due to the seriousness of these consequences, it is always advisable to carefully observe the link of the page where you are browsing, the sender of the e-mails you receive and any links reported.
Many times, to find out if it is a scam, just click with the right mouse button, click on "copy address" and paste it on the notepad. You will immediately notice if it is an original link or a scam.
If you receive repeated e-mails of this type, you can send a report, through a specific procedure, through the website https://www.commissariatodips.it/
Sometimes it is not enough, and countless software vulnerabilities, or malicious applications, help the bad guys.
To give an example, while on the computer we can install anti-virus, anti-spam and "reputational" software that help us distinguish whether we are browsing on a secure site or not, the matter changes for mobile devices.
Protecting navigation on smartphones is much more difficult, both because there are no well-developed protection suites, and because on the smartphone we are linked to "apps", which guide us towards the service we have requested.
The apps (of any service) are usually heavily tested before their release and generally receive constant updates, but as we well know they “base” their foundations on the operating system of the smartphone, which represents a much larger and more ecosystem prone to vulnerabilities.
To give an example, a vulnerability has recently been disclosed which has been called "StrandHogg”, Which affects all versions of Android.
This particular vulnerability exploits the system of multitasking of the operating system, that is, the system that allows multiple applications to be open simultaneously.
The vulnerability, to be specific, exploits a particular system control Android called "taskAffinity", which allows an application (even malicious), to assume any "identity" in the aforementioned multitask system.
By exploiting this vulnerability it is possible, for a malicious application, to "take the place" (technically a "hijack" is carried out) of the original application.
This allows you to redirect the user to a false screen and thus be able to steal credentials, but also to overcome two-factor authentications (for example, we think of banking apps and the control SMS).
Also in this case, the phisher it can steal our data and it is much more complex for the user to realize what is happening.
It is also true, however, that the malicious application must be installed on the victim's smartphone, therefore it is necessary to pay close attention to what is installed.
Companies like Google and Apple, which manage the largest marketplaces currently on the market, systematically remove multiple malicious apps, but the user must always be extremely careful not to have problems.
Now let's think about what an attack can bring Phishingthis time targeting an entire state.
ATTENTION: THE SCREENSHOT THAT FOLLOWS IS A FALSE, AND IT WAS CREATED PURPOSE AS A DEMONSTRATION.
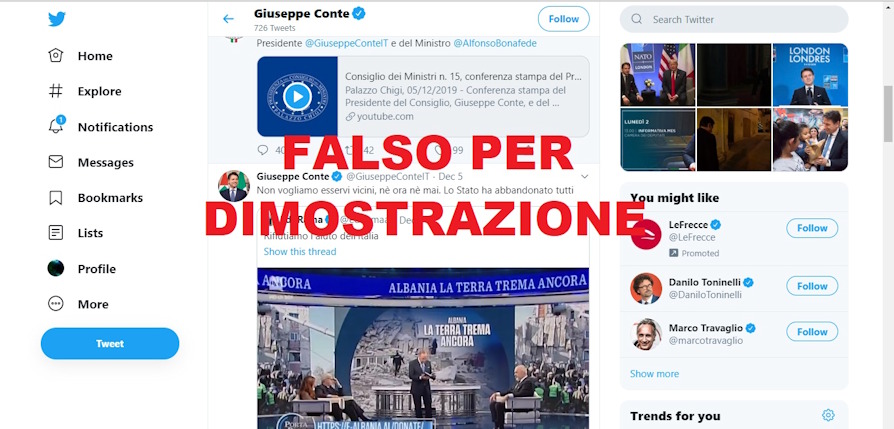
As mentioned earlier this is a fake, and it's just a demonstration created specifically for the article, but let's analyze it in detail:
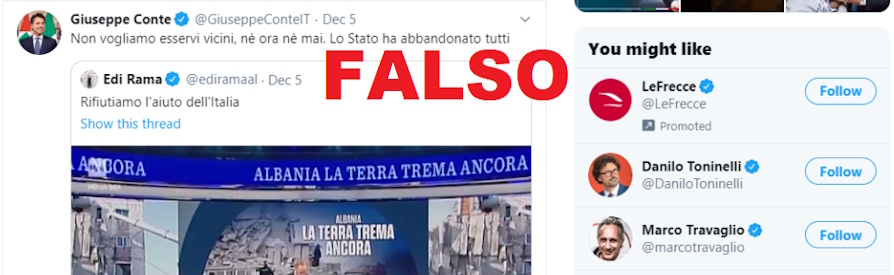
As you can imagine, if this were true tweet, a scandal and a possible breakdown of relations between two countries would result.
But we know it's not real, it's just a demonstration, but why do it?
Cyber attacks are never accidental, and often have roots in the geopolitical situations of the countries involved.
A cyber attack of this kind is cheap, does not cause victims and can hardly be attributed, it is therefore useful for creating pressure towards a nation, creating a controlled destabilization and at the same time keeping diplomatic channels open.
A "fake" like the screenshot above, could be useful to create a destabilization in public opinion.
The moment someone went to check for the presence of the tweet, one might always think it has been removed, keeping the doubt alive.
This behavior, typical of fake news, is useful for creating a rift in public opinion which, depending on political preferences, may believe or not believe that the post is true.
This technique can also be used to "distract" public opinion about a specific problem.
To maximize the effectiveness of such a campaign, a relatively new technique called "deepfake".
Il deepfake is a special technique that allows you to process an image by superimposing and modifying the original image through Artificial Intelligence, thus creating a false indistinguishable from the original image.
This technique is widely used, and the case of deepfake aired by the Striscia la Notizia program (link to the video: https://www.youtube.com/watch?v=E0CfdHG1sIs)
To make a video deepfake it is necessary to use an NVIDIA video card that supports the CUDA architecture, that is, that allows the processing of the calculations in parallel.
Currently, therefore, it is sufficient to use a normal gaming computer, and the software that can be found on the net.
It is normal to expect that, for those who have enough resources, it is very easy to create structures, campaigns and pages / images / videos that are so well made as to bring about a large-scale and highly effective attack.
You can still protect yourself from all this, and I would like to make a suggestion: as you have seen, however complex the operation, here the target of the attack is not a machine but the single person, which represents the greatest "vulnerability", as one's own experiences and emotions may or may not influence a judgment.
To defend oneself it is necessary to "keep up to date", without prejudice dictated by a political color or a personal preference, analyzing the various situations according to one's own common sense, inquiring, in order not to fall victim to a scam or to avoid playing the game of those who draw profit from a destabilization.
To learn more:
https://promon.co/security-news/strandhogg/
https://it.wikipedia.org/wiki/Phishing
https://it.wikipedia.org/wiki/Deepfake
https://it.wikipedia.org/wiki/Rete_neurale_artificiale