29/03/18 | Cyber
WannaCry infects Boeing: does the law of retribution strike again?
Who doesn't know Boeing? The leading US company in the aerospace field seems to have been hit by the malware known as WannaCry, a virus of ...
1525
Read

18/03/18 | Cyber
How the security measures in the GDPR will change our approach to risks involving personal data
As indicated in the previous article (read) the new European legislation on the protection of personal data is upon us, and with it the whole system is innovated ...
875
Read

12/03/18 | Cyber
The secret war of hackers: The Equation Group, the "armed" cyber arm of US intelligence
That the network of the Internet was designed and implemented in the military in the United States is certainly not a mystery. As it is known that also many of the technologies ...
2622
Read

03/03/18 | Cyber
INTERconNETtiamoci but with your head!
Italy is a strange country, one in which the inconclusiveness of the institutions is flanked (and made up for!) By personal excellence. Today I want to tell you about a case in which the ...
625
Read

26/02/18 | Cyber
Interview with Carlo Mauceli: The theft of credentials, risk factors and guidelines for the safety of Italian companies
Today we have the opportunity to talk about credential theft with one of the leading cybersecurity experts in Italy, Carlo Mauceli, Chief Technology Officer at Microsoft ...
757
Read

19/02/18 | Cyber
DefenseReady, the software for the US Defense organizations
It is known that the Defense of the United States of America has for years had an excellent relationship with Microsoft, the information technology multinational based in Redmond. The combination of skills ...
1406
Read

15/02/18 | Cyber
From North Korea, The Lazarus Group. Cyber warriors or cyber criminals?
Being able to orient oneself correctly in that enormous "gray zone" that cyber-space is becoming is a very complex undertaking. Being able to establish who really is the perpetrator ...
1392
Read

06/02/18 | Cyber
China: National Cyberspace Security Strategy
In December of the 2016 China made public the national strategy of the cyber sector through the publication of a high-level document called precisely ...
783
Read

25/01/18 | Cyber
Cyber defense? Cisco Umbrella and Investigate
The term "cyber" has now become part of the common vocabulary and associated with other terms such as "attack", "defense ...
3358
Read

22/01/18 | Cyber
The future computed: artificial intelligence according to Microsoft
The theme of Artificial Intelligence (AI in English) has entered strongly in our homes projecting us to ...
411
Read
15/01/18 | Cyber
Chaos Computer Club vs Italy!
On 23 December 2016, the so-called FOIA, or the Freedom Of Information Act, came into force in Italy ...
1191
Read

08/01/18 | Cyber
SATORI, "the awakening" of the botnets and the other 2018 challenges for cyber security
Understanding which will be the most important trends for the year just inaugurated in terms of cyber security is not certain ...
488
Read

03/01/18 | Cyber
Cryptocurrency hacked? And the bitcoins go down!
One of the businesses of the moment seems to be investing in cryptocurrency. The best known are Bitcoin, Ripple, ...
1257
Read
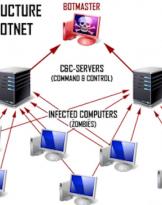
02/01/18 | Cyber
Dismantled the "Andromeda" botnet
A few days ago the news, passed over in silence as usual, of the dismantling of the Andromeda botnet in ...
3868
Read

19/12/17 | Cyber
The higher the digitization level the greater the cyber risk
What factors determine cyber risk? What happens to a society that is too digitized? These questions arise ...
443
Read

18/12/17 | Cyber
Can a cyber attack endanger life?
The answer is yes. It has been like this for some time, even if it is not mentioned. A cyber attack is as dangerous as an attack for ...
979
Read

09/12/17 | Cyber
US Cyber Attack against North Korean missile capabilities?
Has the United States of America carried out cyber activities to sabotage the missile capabilities of North Korea? ...
2830
Read

06/11/17 | Cyber
The Sandworms and Ukraine: when cyber security takes on a strategic role
During the two days of Cybertech Europe (see article), inside the famous "cloud" of the new congress center in Rome ...
1652
Read

03/11/17 | Cyber
There are no shortcuts in Cybersecurity!
In my last article: "Artificial Intelligence: opportunity or risk?", I tried to highlight some aspects ...
590
Read

25/10/17 | Cyber
Artificial Intelligence: Opportunity or Risk?
In Italy it has passed virtually unnoticed - perhaps for fear of derision - a fact that happened a few months ago and that ...
1863
Read