Among the cyber attacks that exploit methods of script injection il Cross Site Scripting (XSS) it is certainly one of the most famous and in this short article I will try to explain the risks and the important role played by a tool called WAF (Web Application Firewall) as the first line of defense against these attacks.
XSS is an attack, as already mentioned, of the injection type, i.e. in which a script is injected into a web page, making it infected and allowing an attacker to steal data of various kinds from the victim who is browsing.
First of all, there are two main types of XSS, the so-called Reflected and Stored, the latter also called Persistent.
In both cases the aim of the attack is to exploit a vulnerability in the site or web browser and to compromise the interaction that the user is having with the aforementioned application and the consequences can be harmful for both parties.
In Reflected XSS the victim's browser is attacked, the script is located in a link malicious, often sent to the victim in an email, link which is apparently legitimate but which once clicked will start the script placed inside it, compromising the user's session with the application he is using.
Session data, cookies and any other sensitive data will be promptly sent to the attacker.
in Stored XSS the application is attacked directly and typically vulnerabilities of websites that use some type of form that the user must fill in are exploited, upon response from the application a piece of malicious code that has been attached by the hacker to the site is activated by the user. In both cases the user remains unaware of the risk as the applications appear completely legitimate.
Lo Stored XSS it is certainly a more complex and dangerous type of attack as it affects every user who accesses the vulnerable application, the hacker remains hidden by stealing sensitive data for prolonged periods of time, hence the name "Persistent XSS".
So how can we protect our web applications from this type of attack?
As we well know, private companies and public bodies rely on the correct functioning of services available on the web on a daily basis. The reliability anduptime of some of these services is absolutely vital and must be preserved as best as possible and to guarantee their existence a large number of these are protected by an extremely important technology, namely the Web Application Firewall or in short, WAF.
WAFs are an important help in protecting us from external threats of various kinds, from malicious attacks and from unwanted traffic to our servers, such as bot protection, denial of service (DOS) type attacks injection, attacks of Cross site scripting (XSS) ed SQL injection and more.
WAFs are to be considered an important line of defense against type attacks injectionBy monitoring traffic at the application level, they are able to identify one of these attacks before it is too late, checking potentially harmful character sequences and patterns that may be indicative of an attack of this type.
WAFs can prevent or make us realize that a similar attack is underway thanks to a "signature based" filtering that manages to block a large part of malicious requests, obviously this set of rules and lists of "malicious signatures" must always be updated.
For this reason the WAFs are maintained by teams of experts who work to continuously update knowledge on attack vectors and the rules to prevent them.
Obviously WAFs do not offer infallible protection, the defense potential against a similar attack, but also against other types, derives from a correct configuration of the rules in use.
WAFs analyze and prevent what is known, while extremely sophisticated and never before seen methods will unfortunately not be reported, there are also techniques of bypass firewalls that often make use of loopholes in their configuration.
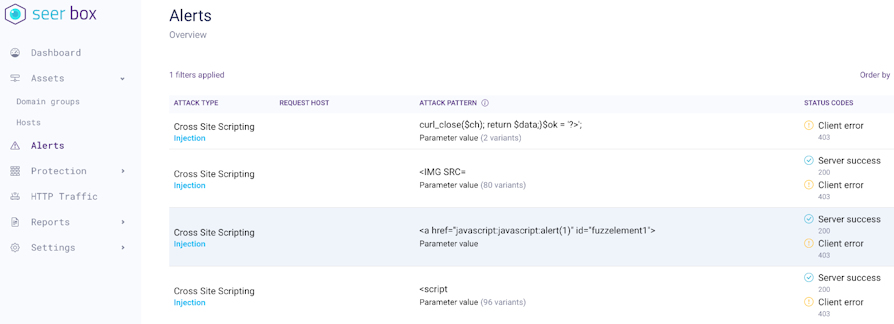
For this reason some WAFs help the user to inspect the operating characteristics of the product, providing detailed information on the type of traffic received from the monitored services and the parameters received, and this is not a common feature in every WAF, which often only provide the log with the notification relating to the activation of the rule in use.
Furthermore, some WAFs focus on an enforcement strategy of legitimate behavior rather than a signature based approach like the one explained previously, a strategy which in some cases could make the difference and help significantly the process of identifying the attack and combined with the ability to some more complex WAFs, starting a deployment of a virtual patch even without stopping the service can ensure an uptime rarely achievable by less advanced software.
https://owasp.org/www-community/attacks/xss/ for more detailed info on xss
https://seerbox.it/ example of non-signature-based WAF