21/12/22 | Cyber
Knowledge Management and technology
As always happens, there comes a time when something needs to change, in life as in work or in society. Many transformations are due, guided or simply...
289
Read

04/12/22 | Cyber
From Information Warfare to Cognitive Warfare
It will not have escaped those who follow the evolution of the military field that after Cyber Warfare, Information Warfare and Hybrid Warfare, it is increasingly common to read about Cognitive...
1243
Read

29/11/22 | Cyber
Lockheed Martin and Microsoft, classified cloud and new technologies for American defense
A few days ago the announcement was made that the two giants, Lockeed Martin and Microsoft, have decided to enter into a strategic alliance aimed at supporting the Department of Defense...
538
Read

03/11/22 | Cyber
Browser fingerprint, with all due respect to privacy!
I think everyone knows what a browser is, so I take it for granted and ask instead if you know what a browser fingerprint is. If we try to translate we get "imprint of ...
1924
Read

17/10/22 | Cyber
Is there democracy without cyber security?
“If we want everything to remain as it is, everything must change”. So spoke Tancredi Falconeri in "Il Gattopardo" addressing his uncle, prince of Salina, skeptical of ...
426
Read

10/10/22 | Cyber
SICYNT: the importance of disclosure in the digital society
The first SICYNT conference on the importance of ...
398
Read

12/09/22 | Cyber
The geopolitics of chips
For several years now we have been hearing about semiconductor geopolitics and for me it is time to deepen the subject. To do this, let's start with a recent article ...
3264
Read

05/09/22 | Cyber
Robot and Artificial Intelligence
We now hear a lot about Artificial Intelligence (AI), the Strategic Program for Artificial Intelligence 2022-2024 (see document) defines it as the whole ...
2226
Read

22/08/22 | Cyber
Zero trust: what does it mean?
The world of security is constantly evolving and with it, the language used by technicians and the ...
872
Read
26/07/22 | Cyber
Hacked the Revenue Agency?
July 25, in Rome the temperature is always higher, and not just that of the weather! A few days ago the government fell ...
1739
Read

25/07/22 | Cyber
Cyber Influence, and we are all part of the global community!
"Cyber-Influence, a new term created to indicate an activity as old as the world, influence, carried out with ...
514
Read

23/07/22 | Cyber
Ergonomic Cybersecurity
I have often had the opportunity to evaluate different approaches to cyber protection, in different areas. Many times the ...
590
Read

18/07/22 | Cyber
Information warfare and cyber warfare, what are the relationships?
As it happens more and more often, I find myself writing an article to answer the curiosity of friends. This...
1107
Read
07/07/22 | Cyber
Grandma in Alexa
Personally I am fascinated by artificial intelligence, technology and how gradually but ...
1019
Read

27/06/22 | Cyber
How safe are VPNs?
With this short article I will try to answer the question that was asked to me a few days ago: "How much is ...
3550
Read

13/06/22 | Cyber
Metaverse, society and cybersecurity
For some time now I have been thinking of writing something about it. As I reflected, time passed and the web is now ...
862
Read

06/06/22 | Cyber
What is a computer virus?
Someone argues that when disclosure in the cyber sector, everything is fine to get the message across ...
973
Read
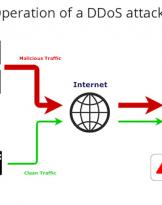
16/05/22 | Cyber
DDoS and viruses
It may seem strange but in our hyper-connected world, where you go by dint of English acronyms and terms, you don't ...
1613
Read

11/05/22 | Cyber
ALAMEDA: Artificial Intelligence for the treatment of brain disorders
Provide personalized care and better treatments to patients with major brain disorders by reducing the ...
712
Read

09/05/22 | Cyber
Locked shields 2022: Finland in first place
This year Finland takes first place in one of the largest and most complex live cyber defense exercises in the ...
858
Read