John The Ripper, not to be confused with “Jack the Ripper” (Jack the Ripper, so to speak) is a tool Open Source for the 'audit (control) of password security and for password recovery, available for many operating systems and developed by Openwall1. This tool was developed for "constructive" purposes but, sometimes, it can be used by malicious people in a "destructive" way.
How is it used?
Passwords are the first line of defense for most computer systems and online accounts. A strong, complex password can help thwart hackers and unauthorized access. However, many users choose short, simple and therefore easy to guess passwords, compromising their own security and often that of others. Cracking tools like John the Ripper are designed to crack weak passwords (few characters, well-known and common phrases), using techniques such as:
► attacks to dictionary, a type of attack that exploits the search for words present in dictionaries or common language phrases.
► attacks by brute force, which use the "trial and error" method to guess the login information: you try all the possible combinations, alphabetical and numeric, hoping to guess the password correctly.
► hash decryption. A hash is a string of characters generated by a “hashing algorithm,” which takes an input (such as a password) and produces a unique sequence of characters. The main goal is to uniquely represent the original data. Hashes are commonly used to protect passwords, encrypt data, and ensure file integrity. This process is often irreversible, although with the "brute force" method (with large computing capabilities) one could trace the original input.
John was initially created for Unix systems and now used on several platforms. It supports multiple cracking modes, including “Single Crack” mode to focus on one password hash at a time, “Wordlist” mode to use a predefined list of words, and more. It is pre-installed on Linux systems. A notable feature of John is that it can automatically detect the decryption type for common formats. This saves a lot of time researching hash formats and finding the correct tool to decrypt them.
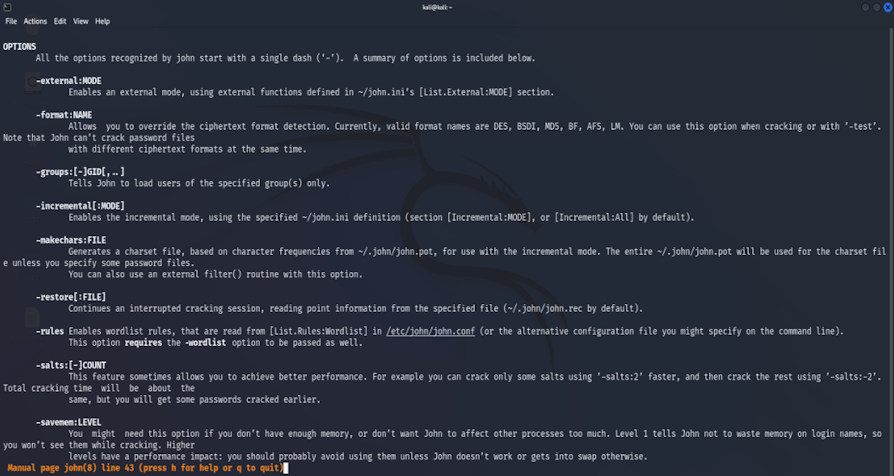
John has many options; you can get both an in-depth description of them by typing "man john" and a summary by typing "john" in the terminal.
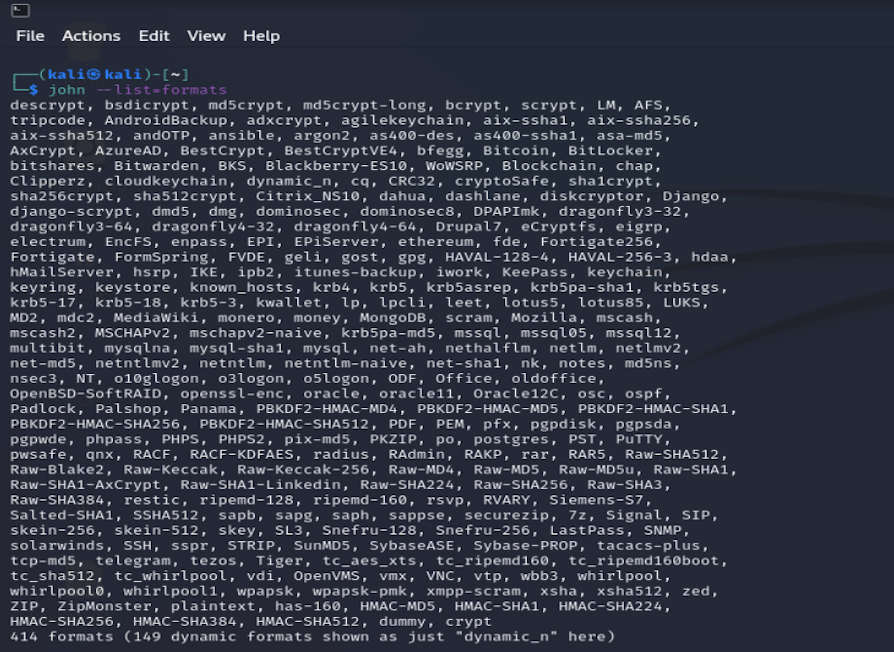
It can handle a large number of hash or file formats. "john --list=formats" shows all options supported by the tool.
Practical example of attack

Now let's try to use John on a password protected pdf file, “prova.pdf”. The file is protected by a “simple” password, with 5 characters and 2 numbers.
1) We calculate the hash of the file
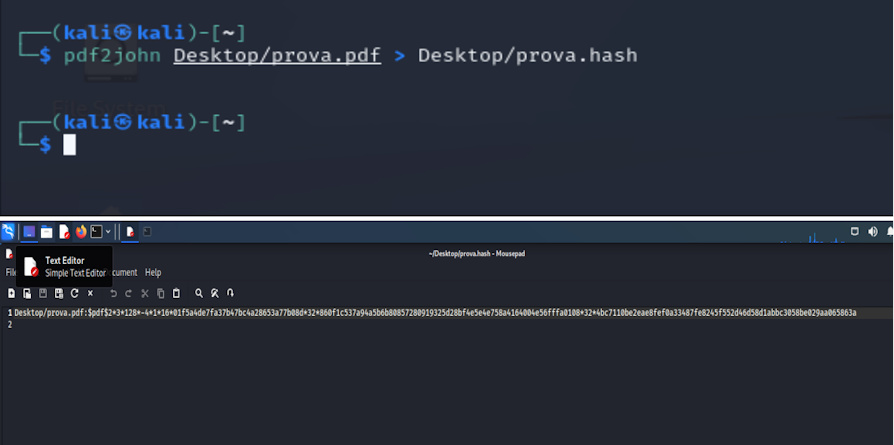
Contents of the “pdf.hash” file
We saw previously that we can carry out a brute force attack and a dictionary attack, let's try to test them both.
2) Brute force attack
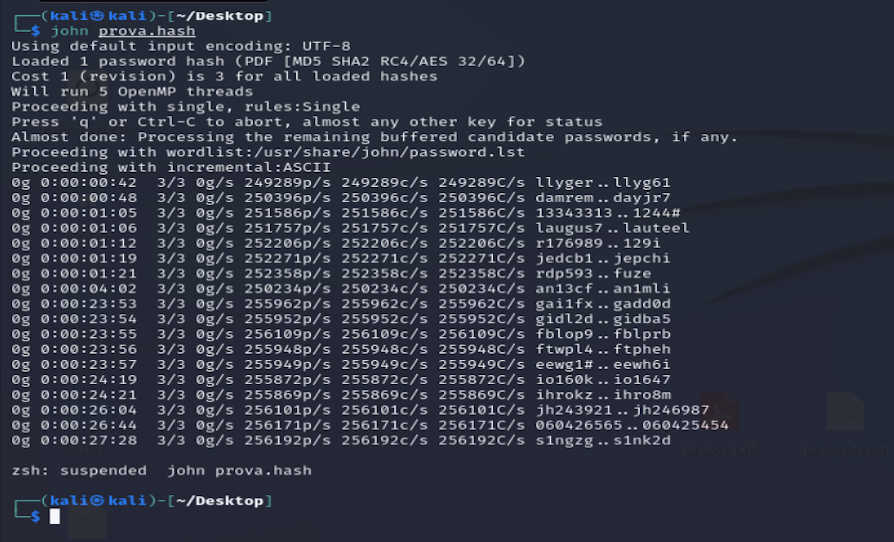
John tried every possible combination for almost 30 minutes, failing to find the password. He could have continued much longer and eventually found her, but that's not the point of this example.
3) Dictionary attack
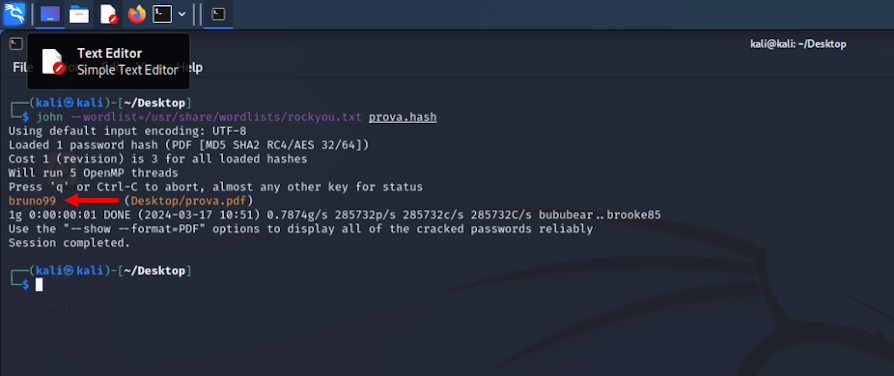
In a dictionary attack, using a text file open source (https://github.com/zacheller/rockyou), John deciphered the hash in according 1.
This makes us understand how important it is for a malicious user not only to have suitable tools to attack, but also to have information on the victim, in order to build an "ad hoc" dictionary. Contrary to the brute force attack, which searches for all possible combinations of characters, the dictionary attack exploits specific knowledge about the victim. This information may include names, important dates, keywords or other personal information that could be used as passwords (names of relatives, pets etc.)
Therefore, understanding the dictionary attack and taking steps to mitigate its effects is essential to protecting personal and business information.
Final tips for escaping such attacks
Increasing computing power requires longer and more complex passwords. Some key tips for choosing a strong password are:
• use at least 8-12 characters or more: the longer the better;
• use a combination of letters, numbers and symbols;
• do not use common dictionary words or personal information;
• do not reuse the same password on different sites or applications;
• change passwords regularly;
• If possible, implement two-factor authentication.
The security of a strong password is a fundamental aspect in the daily life of each of us. Implementing other security measures, such as the use of antivirus software, will further improve protection against cyber threats; However, we must not forget that man's worst cyber enemy is man himself, which is why we must first of all work on ourselves and then on our IT devices.
1 (Source: https://www.openwall.com/john/)












