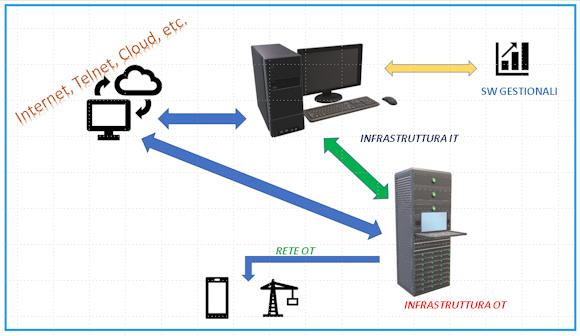
An automated production system managed in Industry 4.0 necessarily has an internal / external data and process management network available (production recipe, warehouse management cycle, automated tests, etc.).
In the opening image it is possible to understand the complexity of a complete OT system developed according to modern standards.
This applies to the simple sensor that transmits the data to the Control Room up to the remote management of a robotic island, where from Server & Hosting the recipe for the new positions for the various robots on the island is sent based on the new component to be built (think for example of in-line painting robots in an auto component production chain).
The recipe or the value of the data constitute the know-how of the company, often they are the very basis of the success of the given process. As for natural persons (employees, employees, managers, etc.) confidentiality is a must, the same commitment must be made to avoid the theft of data stored on the Cloud, local archives, memories distributed in the various points of the company network. . The same applies to access: not everyone can access particular places where an industrial secret is kept, and the same applies to those who want to access it via the network.
Similarly, maintaining the integrity of both the data and the structure that processes and transmits it is also fundamental: what would happen if the sensor went out of calibration and instead of reading the correct value, it reads a different value? What if the robot applies a different recipe to the component in production? In the first case it could cause the system to stop if the value sent is above a certain threshold of warning or alarm. In the second case it could force the robot to perform a maneuver that damages the piece or the robot itself. Just like any human error.
However, there is a third, much more subtle case with regard to integrity and it is the concept of "apparent integrity": The system under attack is basically functioning but in the process there is a value that often random it is altered in order to distort the final result of the process. For example, testing at the end of the production line, in addition to its own natural waste, will accuse of waste due to false signals given by the sensors and which will be recognized as natural waste.
In the control chain, no information is related to the intervention of the malware hidden, but in the meantime the same every now and then makes its contribution to the total number of pieces discarded, aggravating the company cost in a continuous dripping. Or vice versa, even worse case, such malware will result in a manner random "good" a piece that is actually "waste" and therefore this component will be placed on the market!
The third point of the triad refers to Availability: both the system and the data must be available, even following an attack. As a rule of good practice, the PLC program or the ICS (Industrial Control System) is already redundant, as are all the critical parts of the network. But the basic practice is the execution of back-up of physical system and organized in an "artisanal" way: Putting the data on an external hard-disk that is connected just for this purpose and then disconnected and alternating it with a second hard-disk is much more efficient in the phase of recovery that not an expensive system and for the required pace of recovery often too cumbersome and slow.
How to protect yourself and with what strategies
From the above, the starting point is the CIA and this concept must be clear in the development of the OT network. A parallel triad must be preliminarily prepared and updated with greater commitment:
- Self Consciousness
- Knowledge of
- Operational context
The first two components refer to the human factor: If all operators, at any level, agents in the OT system do not have awareness and knowledge of the delicacy of cyber security and of the risks that can turn into threats or attacks, no protection system is can really protect.
The basis is trivial to say the least: each of us wonders what would happen if the PC I try to turn on does not boot. What immediate consequences? Which in the medium to long term? What if the production line PC doesn't start? Or the whole production or quality control system?

Being aware of this is the first barrier against possible attacks as it triggers the self-defense mechanism with the search to know how to protect yourself, apply to implement the protections and also update by suggesting or agreeing with the IT manager, based on the application context, such as are the real possible risks and perhaps what could be the possible mitigation actions.
While leaving the definition of the OT structure and management to the expert technicians, the corporate security policy must be drawn up by your own are built on? which must involve and empower.
After the "evangelization" part, the suggestions come spontaneously from the various actors and therefore it turns out that:
- Analog sensors that simply provide the data in analog format (for example the classic 4-20 mA) or digital (but only in output) without the possibility of being calibrated remotely, are much safer than sensors in IoT (Internet of Things) logic ;
- Sensors or systems in IoT logic are very performing compared to the former, but they must be protected with dedicated passwords and all communications must be encrypted;
- All passwords of sensors and systems supplied by default by suppliers must be changed from the first use;
- Each time the specific system or sensor is accessed for process change, calibration or predictive maintenance or remote access via an external line, the security settings and password must be changed;
- The process referred to in point 4, if automated, must be through an internal company system;
- An appropriate formalized back-up procedure, whether physical or on the cloud or on multiple entities, must be implemented and verified.
Lastly, but which is actually the weak link of all of the above and for this reason we indicate it as a final reminder, the human factor (both as a possible error and as a predetermined action) plays a fundamental role in IT security and especially in the OT system since it is distributed both as IT network and physically for all phases and production locations.
THEInsider Threat must be properly assessed and the possible consequences foreseen and mitigated with a formal and very flexible approach based on contingent situations.
Also read: "Confidentiality - Integrity - Availability in Operation Technology from an Industry 4.0 perspective: part one"
REFERENCES
[1] Stuxnet Worm Attack on Iranian Nuclear Facilities (stanford.edu)
[2] https://www.nbcnews.com/tech/security/colonial-pipeline-paid-ransomware-...
[3] https://www.mise.gov.it/index.php/it/incentivi/impresa/beni-strumentali-...
[4] http://ijarcsse.com/Before_August_2017/docs/papers/Volume_4/1_January201...
[5] What is the CIA Triad? Defined, Explained, and Explored (forcepoint.com)