Verkada, Triton, Colonial pipeline... they are not mysterious words of a quiz game, but simply the mirror of the reality we are facing in which both the boundary between digital and real and the protection from threats of malicious people are increasingly blurred.
Scenarios of digital attacks on industrial devices, also called OT or IoT, are increasingly commonplace; with an important impact on our privacy, our businesses or even worse the life of each of us if we talk about critical infrastructures such as oil pipelines, hospitals, etc.
Verkada - March 2021 - "A group of hackers claims to have breached a huge amount of security camera data collected by Silicon Valley startup Verkada Inc., gaining access to live feeds from 150.000 surveillance cameras inside hospitals, companies, departments of police, prisons and schools. "
Triton - 2017 and 2019 - "Hackers use Triton malware to block industrial plants and systems. Malware is designed to target industrial systems and critical infrastructure."
Colonial pipeline - June 2021 - “The hack that blocked the largest gas pipeline in the United States and led to shortages across the east coast was the result of a single compromised password. Hackers entered Colonial Pipeline Co.'s networks through a virtual private network account, which allowed employees to remotely access the company's computer network. The account was no longer in use at the time of the attack, but could still be used to access Colonial's network. "
In this context, it is with great hope that we see concepts such as “Zero Trust”, “Operational Continuity”, “Industrial Device Protection”, etc. becoming more and more established in the IT and Cybersecurity world. However, explaining to companies how to protect industrial devices, which often have an average of 30/40 years of service, in a physically and digitally isolated building, is not always easy..
This article wants to try to open an insight into this scenario and help to understand how the protection logics of industrial devices (often and willingly called devices Operation Technology - OT, or the latest devices Internet of Things - IoT) can intersect with the classic logic of devices belonging to the IT world that most of us know, highlighting how it is possible to apply concepts such as Zero Trust even to a world legacy like the industrial one.
What devices?
First let's define what we mean by OT / IoT devices, using the following nomenclature for simplicity:

It goes without saying that in a reality operating for example in the manufacturing world, where perhaps we have a prevalence of devices in the industrial field (OT), three very specific ecosystems can be found:
- An IT environment with hardware between 5 and 10 years, which uses protocols such as TCP / IP, HTTPS and where basic identity protection concepts such as Multi Factor Authenthication (MFA) are applied (or at least should be applied), spam / phishing mail protection, anti-malware protection, etc;
- An OT environment, with hardware dated at will, which uses strictly specific protocols and - as security logics - purely uses an "isolation" criterion;
- A Cloud environment, used both to extend the capacity of your own on-premise datacenter (group of servers held and controlled on site, ed) both for applications / services and for reasons of scalability, time or simply costs, it is more efficient to start from cloud.
OT devices
Let's focus this article's attention on the second point: OT environments. We generally find legacy (older) OT devices and Industrial IoT, newer footprint devices: these control physical equipment - hence common technology such as heating, ventilation and air conditioning (HVAC) systems - as well as specific equipment of the sector for production - that is, oil and gas facilities, utilities, transportation, civil infrastructure and more.

These OT systems are often monitored by the IT environment to provide business analytics and other insights into physical business operations. Although IT platforms and underlying IP networks are similar to IT, OT environments are different in several respects:
- The set of measures and tools designed to prevent or reduce accidental events is the main safety item OT (Safety); this is in stark contrast to the IT world which focuses on the set of actions and tools in response to an ongoing threat, organized precisely for the purpose of causing damage to IT systems (Security). This difference is due to the fact that a failure of the OT system could directly cause bodily harm or death: for example, to employees working on or near heavy machinery; customers using / consuming a product, citizens living / working near a physical facility, etc.
- As we have already anticipated OT hardware / software is much older than IT systems because physical equipment has much longer operational life cycles than typical IT systems (in many cases up to 10 times longer). It is not uncommon to find 50-year-old equipment that has been modernized to electronic control systems.
- The security approach of OT systems differs from the IT world because these systems have often not been built with modern threats and protocols in mind (and often rely on software cycles to "end of life"). Many established IT security best practices such as software patching are impractical or completely ineffective in an OT environment, and even if they were selectively applied they would still have a limited security effect.
We have mentioned the "isolation" criterion of OT devices, to apply which various logics can be implemented:
- Hard Boundary: complete disconnection of traffic, often physically disconnected devices ("air gap");
- Soft Boundary - based on a firewall or other network traffic filter, like any security boundary, a soft boundary requires monitoring and maintenance to remain effective over time. Unfortunately, we see many cases where organizations set firewall rules to block traffic, without a comprehensive approach of people / processes / technologies to integrate security into change management, closely monitor anomalies, continually check for changes, test the boundary with attack simulations, etc.
- Internal segmentation: isolating groups of OT systems from each other as an additional impediment to attacks. This practice requires that the communication / traffic models are compatible with this approach and continuous maintenance towards both control and exception management.
These security practices apply zero trust principles well, although they are constrained by static configurations and network controls due to the age of the OT systems.
The Industrial Environment and the "outside world"
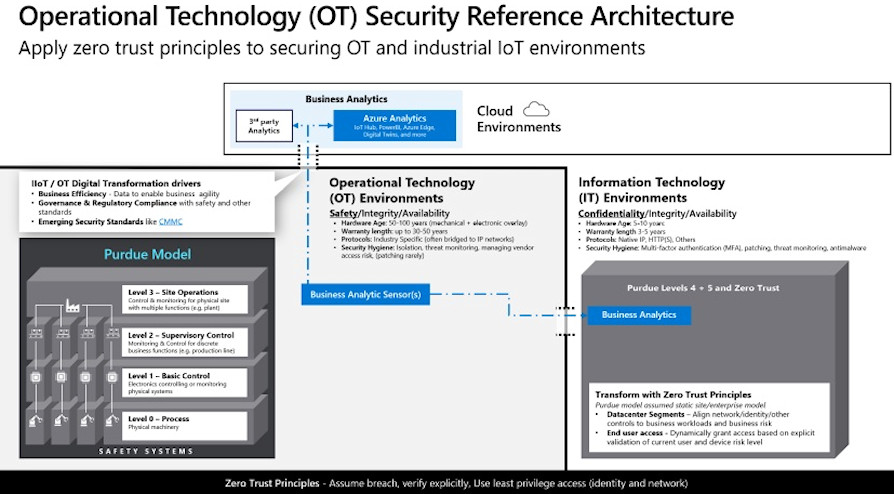
Since 1990, the Purdue Enterprise Reference Architecture (PERA), aka Purdue Model, has been the standard model for the organization and segregation of business and industrial control system (ICS) security measures and network functions, indicating the following Operating Levels:
- Level 0 - The Physical Process - Defines the actual physical processes.
- Level 1 - Smart devices - Detection and manipulation of physical processes (Process sensors, analyzers, actuators and related instrumentation)
- Level 2 - Control systems - Supervision, monitoring and control of physical processes (Controls and software in real time; DCS, human-machine interface (HMI); supervision control and data acquisition software (SCADA)).
- Level 3 - Production Operating Systems - Management of the production workflow to produce the desired products. Batch management; production execution and operations management systems (MES / MOMS); laboratory, maintenance and facility performance management systems; historical data and related middleware.
- Level 4 - Company logistic systems - Management of activities related to the production operation. For example, the ERP is the main system; establishes the plant's basic manufacturing schedule, material usage, shipping, and inventory levels.
Since the definition of the PURDUE Model, levels 0-3 (OT Environment) have changed little compared to the remaining architecture, i.e. level 4, which reflects a more modern approach thanks to the principles of zero trust and the advent of mobile and cloud technology.
The advent of digital transformation, the so-called Industry 4.0, required analytics aimed at making business aspects more efficient: increasing the correlation of the ever-increasing volume of production data with an IT world and a Cloud world. Thanks to the collection of data from OT / IoT devices with dedicated services and the available computing power, the cloud approach has allowed the application of predictive and prescriptive analysis logics.
But, as we initially saw, we know that cybersecurity attacks are increasingly extending to IT, IoT, OT environments requiring incident response processes (and prevention strategies) to converge towards a unified approach, which extends to these environments while having to adapt them to the abilities and limits of each one.
Therefore, a useful weapon to face these increasingly diversified attacks consists in adopting OT / IoT protection solutions.

There are multiple protection solutions in the industrial world, i.e. of OT / IoT devices, some of which are based on a network-level approach called passive monitoring or Network Detection and Response (NDR) - which has a zero impact on industrial networks: it is implemented an on-premise network sensor (physical or virtual appliance), which connects to the SPAN port of a switch. This sensor identifies abnormal or unauthorized activity using behavioral analytics and IoT / OT-specific threat intelligence, with no impact on device performance.
Regardless of the individual functionalities of the solutions, these are the four fundamental characteristics:
- Possibility of asset management of OT / IoT devices: often a company is not aware of all the devices inside it. The first goal of these solutions is to create a complete inventory of all IoT / OT assets, analyze proprietary industrial protocols, view network topology and communication paths, identify equipment details (manufacturer, device type, serial number , firmware level and backplane layout);
- Identify device vulnerabilities: missing patches, open ports, unauthorized applications and unauthorized connections; detect changes to device configurations, controller logic, and firmware;
- Detect anomalous or unauthorized activity using behavioral analysis and artificial intelligence on IoT / OT compatible threats, for example by immediately detecting unauthorized remote access and unauthorized or compromised devices. Analyze traffic chronologically and catch threats such as zero-day malware or explore packet capture (PCAP) for deeper analysis;
- To reach a holistic vision it is necessary to be able to report these alerts and threats to a SIEM / SOAR monitored by the Security Operation Center (SOC); ensuring both higher interoperability with other service ticketing tools and a reduction in the recognition and remediation time (MTTA, MTTR) of Security Analysts towards a potential threat.
Is it possible to apply Zero Trust logic to OT / IoT environments? Absolutely yes and it is a fundamental point in the holistic vision of protection we are providing:

This is because even in an industrial environment it is essential to maintain solid guidelines:
On strong identity to authenticate devices - Register corporate devices of any type, assess vulnerabilities and insecure passwords, use passwordless authentication where possible, provide less privileged access to reduce the impact surface of a possible attack and related damage that it can bring.
Device health - to block unauthorized access or identify devices in need of remediation for various reasons, proactively monitoring threats to identify abnormal behavior.
Use centralized configuration and robust update mechanism - to ensure devices are up to date and in good repair.
Sometimes thinking of attacks in the field of IoT devices seems like science fiction or very far from our everyday life but the attacks mentioned initially are a good starting point to make us change our mind, furthermore below, I would like to make you reflect on another example not very far from what it could happen in any work context:

Conclusion
It is essential for companies to evaluate the security of their IoT and OT systems with the same rigor applied to IT systems: while PCs, for example, are normally required to have updated certificates, IoT devices are often distributed with predefined passwords of factory and kept in that configuration for decades.
If it is true that in a chain of attack the human link is certainly the weakest link, and here "training / education" is the first real activity that needs to be started, it is also true that the safety of the chain from a point of technical point of view depends on the weakest element which unfortunately, in the OT world, is almost always present.
Technology is here to help and support us but above all it must be able to face the aforementioned threats to reduce the possible impact and allow a rapid resumption of production and / or business continuity, after a potential attack.
To this end, more than the single functionalities, however relevant, the integration that can be obtained with these solutions is important because the attackers act without rules and without borders of devices, identities, networks, etc.
The only way to protect yourself is to favor an "overview" in order to make the analysis, detection and remedy.
References
-
Verkada Breach Demonstrates Danger of Overprivileged Users (darkreading.com)
-
Tesla (TSLA), Cloudfare (NET) Breached in Verkada Security Camera Hack - Bloomberg
-
Hackers use Triton malware to shut down plant, industrial systems | ZDNet
-
Triton hackers return with new, covert industrial attack | ZDNet
-
One password allowed hackers to disrupt Colonial Pipeline, CEO tells senators | Reuters
-
Microsoft Cyber Security Reference Architectures - Security documentation | Microsoft Docs
-
How to apply a Zero Trust approach to your IoT solutions - Microsoft Security Blog
-
IoT security: How to protect your IoT devices in OT systems (trendmicro.com)
-
Learn how Microsoft strengthens IoT and OT security with Zero Trust - Microsoft Security Blog












