The approach is approaching Black Friday, a commercial event of American origin but which, due to globalization, represents a much awaited pre-Christmas moment for us too.
Christmas is also approaching, which in addition to much higher meanings has an important commercial thrust characterization.
These two events involve a psychological propensity to spend, to gift, to purchase. This propensity is combined with the enormous popularity obtained in recent years by eCommerce services and consumer logistics, amplified by the recent emergency that has further diminished the mobility to traditional shops in favor of online shopping experiences.
This perfect storm represents a situation in which the alert threshold towards scams is at very high levels, requiring consumers to refine their awareness of the risks to avoid unpleasant consequences.
The cybercriminal world is in fact very clear about these trends, as well as the need to continuously find effective channels to undermine the security of this value chain to your advantage.
One of the most used techniques is to target the user via social engineering transmitted directly to the mobile phone.
These messages often contain malicious links, suitably designed to steal important credentials to act in the name and on behalf of the victim. Or links to sites that contain malware able to install itself without arousing suspicion on smartphones, tablets or other devices that the victim uses to visit these sites.
This technique is called Smishing, a recently coined neologism that combines the acronym SM - per Short Message, that is, short message - with the word Phishing - which indicates an attack that uses a series of methods to lure unsuspecting users and convince them to take malicious actions.
Lo Smishing has some distinctive features, which I will try to illustrate to increase resilience to this type of attack in those who receive the message - known according to a recent report1 only by a fraction of the American population between 22% and 34% depending on age.
One of the main difficulties is precisely to determine the authenticity of a text message, often coming from unknown senders or telephone numbers not encoded in the address book.
Another risk factor is that we are used to seeing and using so-called text messages Short URL, i.e. links to sites structured to consume a few characters, for example bit.ly or cutt.ly, followed by a short sequence of characters.
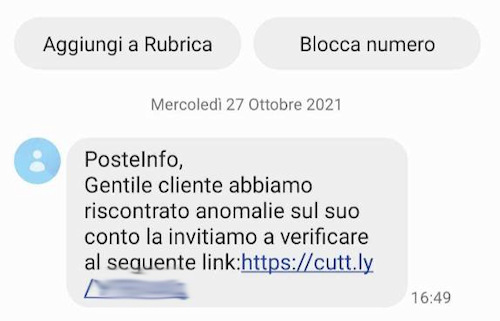
When these addresses are used they connect to intermediate systems that redirect to their final destination, allowing attackers to effectively mask malicious destinations with a system used for many valid and legitimate addresses.
According to Gartner2, several researches show that the SMS open rate is around 98%, compared to a sad 20% that characterizes email.
Also according to the aforementioned report, the attacks by smishing increased by 328% in 2020!
How to defend yourself then?
A very important countermeasure is to raise awareness of risk and the alert in each of us: if a message arrives that there is a package being delivered or waiting at the Post Office with a link for further information and we are sure not to stay expecting nothing, we ignore the message.
The sites these links redirect to are often clones of original crafted with great accuracy, even in the ability to perform strong multi-factor authentication.
The attacker in fact knows the number of your mobile phone because it is the information that allowed him to send you the first message of smishing.
Then, entering your credentials will make you believe that the authentication process requires a further step of entering the code that you will receive - coincidentally - right on the mobile phone.
In the meantime, you will have diligently provided the criminals with a username and password valid for Amazon, Paypal, Poste and other services.
Sometimes these messages are extremely credible, they aim to instill in the recipient a sense of urgency using a specific language. For example: "if we do not receive a reply within 24 hours, we will return the package to the sender" or "in the absence of a verification within 2 hours we will block the account".
To give a further perspective of how much this attack methodology is growing, we can examine the 2020 report of the Internet Crime Complaint Center (IC3) department3 by the American FBI: in 2020 the number of victims of these attack techniques - which include Phishing, smishing, vishing e pharming - they were 240.000; for comparison, victims of virus attacks or malware in the same year there were 1.400!
The four techniques mentioned all involve the attack using social engineering to persuade the victim to perform actions. They differ in the transmission medium because Phishing use e-mail, smishing short messages via SMS, vishing the voice call, pharming the websites to which the victim is directed.
So let's pay close attention - especially in this period - a do not accept text messages from strangers. If we mistakenly mistake a real one for a fake and the person really needs to contact us, they will try again or call us (since they have the number).
Instead, proceed with a click reckless could be the cause of the financial, data and peace of mind that the Christmas season should be a harbinger of.
1 State of the Phish 2020: https://www.proofpoint.com/sites/default/files/gtd-pfpt-us-tr-state-of-the-phish-2020.pdf
2 https://www.gartner.com/en/digital-markets/insights/the-future-of-sales-follow-ups-text-messages
3 Link to learn more: https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf












