The world of technology, more particularly that of cyber security, is now full of acronyms and acronyms that make a dialogue between practitioners in the sector seem almost an alien language.
The goal of this article is to clarify a handful of these, relating to some important company initiatives no profit American MITER.
Established in 1958 to support the federal government in matters of advanced technologies in relation to national security issues, over the course of over six decades of existence, MITER has given life to numerous projects, recently playing a primary role in supporting companies in the field. cyber security with five very important initiatives.
Before analyzing the acronyms, trying to dissect their contents, it is essential to become familiar with a concept that represents a common thread behind these initiatives: the compromise chain or kill-chain.
When it comes to cyber attacks, the presence of an attack strategy is now well established, which develops over time in some very specific phases.
As already illustrated by Alessandro Rugolo and Lino Porceddu in a great article last March, identifying the attacker's activities as early as possible in the chain of compromise allows for the organization of extremely effective measures to counter the attack and mitigate damage.
To do this, it is crucial to identify the type of opponent based on the tactics, techniques and procedures used. And here is the content of a very frequently used acronym: TTP.
Le Tactics they are about understanding the opponent's goal.
Le Techniques they concern how the opponent achieves the goal.
Le Procedure they are about the way tactics are operated.
The theme of TTP and the importance of being able to identify them was dealt with by Orazio Danilo Russo in a interesting article last May.
Understanding the chain of compromise and TTPs allows you to appreciate the enormous value of MITER's five main cyber security initiatives.
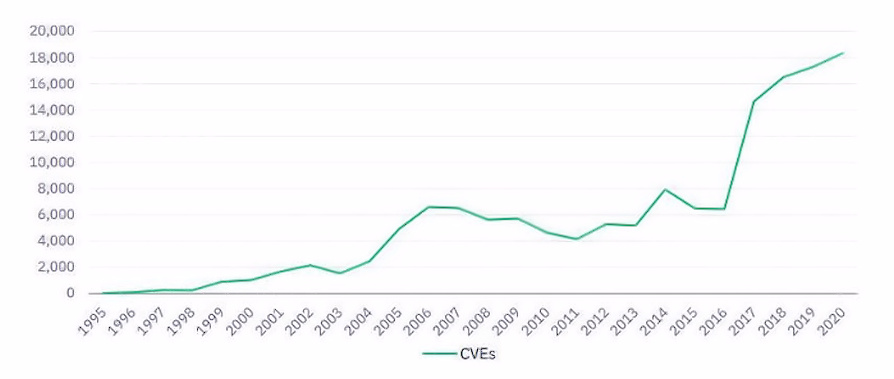
The first - well known and popular - has been a point of reference for twenty-two years, a cyber lighthouse to navigate the multitude of vulnerabilities that afflict infrastructures and software of all kinds. I'm talking about CVE, an acronym for Common Vulnerabilities and Exposures: a centralized web-based collection of security holes, organized to be quickly searchable and searchable based on various criteria.
To give an idea of the mammoth work behind this initiative, just look at the graph below which shows the trend of vulnerabilities recorded over time up to last year:
The second acronym that is an excellent source of information for cyber defenders is the very famous ATT & CK, what does it mean Adversarial Tactics, Techniques & Common Knowledge.
Online compendium that represents in a very well constructed and usable scheme the typical tactics of the attackers, detailing the most commonly used techniques for each. Each of these two groupings provides a context that allows the mapping of what is observed in the field.
For example, let's assume we dig deeper into the tactic Initial access, which describes how an attacker gains a first access path to the victim's infrastructure.
One of the techniques described in this set is the Phishing, of the different forms of which I wrote in a recent article, which exploits social engineering through communication and messaging applications. Within this context, several sub-techniques are distinguished, such as Spearphishing Attachment - which strikes the victim through attachments (e.g. e-mails) armed to engage in malicious behavior when opened.
To deepen this interesting initiative I point out another article by Orazio Danilo Russo of last June dedicated to the ATT & CK initiative.
The third acronym, certainly less known than the first two but equally important for arming the cyber defenses, is CAR - expanded in Cyber Analytics Repository.
It is a very useful analytics library, i.e. models for data analysis available both as pseudo-code and in practical implementations ready for use in the most common platforms for data correlation - such as SIEM systems ( Security Information & Event Manager).
Modeled on the ATT & CK matrix for the identification of opposing TTPs, this repository is composed of elements that contain the distinctive features of the complex events that we want to detect. One example is writing batch files to the Windows System32 directory: although batch files are not malicious in themselves, they are particularly rare for them to be created in the system directory after installing the operating system.
To monitor its occurrence, simply consult the CAR page dedicated to this event at the link CAR-2021-05-002 to have all modules for different platforms.
Fourth initiative that we consider is ENGAGED: it is not an acronym but a conceptual nomenclature. The idea is to provide a methodology for analyzing and planning actions to counter, deceive, and deflect the opponent.
By processing the behaviors of the attackers observed in the field, ENGAGE allows you to act on three levels:
understand how the deviation, the deception and the contrast of the attacker can enter the cyber strategy of an organization
how to counter the attacker
understand how cyber deception tools in use by an organization are aligned with the strategies of MITER ENGAGE.
The AEP initiative, an acronym that means Adversary Emulation Plan.
Formally an ATT & CK resource, it represents a set of documents to model attack resilience testing activities based on strategies used by known groups.
In this way, companies will be able to test their defense systems just as if they were actually being targeted by actors in the cyber threat landscape.
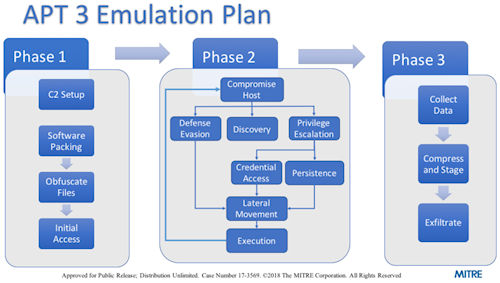 The diagram (image) illustrates how the different phases of this test would be carried out, wanting to simulate the activity of the actor known as APT3 - a Chinese attack group known since 2015.
The diagram (image) illustrates how the different phases of this test would be carried out, wanting to simulate the activity of the actor known as APT3 - a Chinese attack group known since 2015.
Arming the defenses of an organization in order to increase both its maturity in the cyber environment with respect to prevention and remedy, and its resilience with respect to the speed of detection and response to anomalies can be a very complex activity.
Understanding the tremendous value of these MITER initiatives and how to combine them with the processes and resources already in place is critically important to reduce this complexity in a very effective way.












