20/10/21 | Cyber
October, Cyber Security month
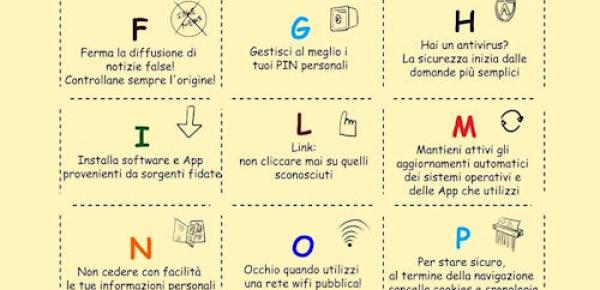
Online Defense and SICYNT united in the month of Cyber Security invite you to share the ABC of Security on Digital Information. Print a copy for the class of ...
424
Read
18/10/21 | Cyber
The impact of artificial intelligence on intelligence analysis
Let's go back to the discussion, only mentioned in a previous article, relating to the role of Artificial Intelligence in the field of intelligence analysis. The question that ...
588
Read

14/10/21 | Cyber
The evolution of the Operating Systems
The computer as we know it, that is a small and relatively inexpensive device, capable of performing numerous calculation functions in a very short time, is ...
2482
Read

13/10/21 | Cyber
Zero Day vulnerabilities: the new and powerful cyber weapons
Everybody knows that computer viruses are now a consistent and persistent threat to companies. Attacks like Egregor Team's against the chain ...
1284
Read

11/10/21 | Cyber
Quantum Supremacy: the Italian race
In recent years, the term Quantum Computing is increasingly used also outside research laboratories, engaging more and more specialized figures in the race to ...
1355
Read

06/10/21 | Cyber
Deep Instinct: from detection to prevention
It has been established that antiviruses are not always able to protect us. In a 2012 study, security journalist Brian Krebs found the effectiveness of ...
516
Read

04/10/21 | Cyber
Situational Awareness, Artificial Intelligence, cyber security and adaptive systems
In the modern world, it is increasingly important to make conscious decisions relatively quickly. This is the case of political decision-makers in the face of a national crisis or of ...
895
Read

27/09/21 | Cyber
Adaptive Systems and Situational Awareness
The world is changing at an incredible speed ... in all sectors. What would you say if overnight you no longer had to waste time understanding the changes made by ...
888
Read

22/09/21 | Cyber
Cisco Networking Academy, a resource!
It often happens that to find an interesting and well done course you have to pay an arm and a leg, perhaps having to ...
690
Read

20/09/21 | Cyber
War law and humanitarian protection symbols in cyber space
One grows up in military schools with the principle - moral, rather than juridical - of never attacking anyone, in the field of ...
884
Read

08/09/21 | Cyber
Cyber Security: differences between Firewall and Web Application Firewall
Untangling among the IT security products, comparing them and then choosing them is not easy at all, not even ...
1627
Read

06/09/21 | Cyber
Chaos in the cosmos (DB)
A few days ago, while glimmers of coolness crept into the Augustan heat wave, he appeared again on social media ...
541
Read

02/09/21 | Cyber
The new SOC Exprivia: between technology and territory
In this period talking about Cyber security is more and more common, even if it is not always spoken with knowledge of ...
607
Read

30/08/21 | Cyber
Internet of Things: the Internet of Things
The term Internet of Things or IoT, often mistranslated with Internet of Things when it would be more appropriate ...
476
Read

25/08/21 | Cyber
And so let's go to the cloud, but carefully!
To quote a famous American saying, cloud is the best invention from sliced bread to the present day! It is one of ...
899
Read

21/08/21 | Cyber
Towards "controlled and guaranteed origin" software. Will they be enough to make us safer?
President Biden orders software security labeling and consumer disclosure of the list ...
660
Read

17/08/21 | Cyber
OWASP ZAP - Zed Attack Proxy
What I am about to describe to you is an event that often happened years ago but now, fortunately, it has become rather ...
1334
Read

16/08/21 | Cyber
DNS and IT security
Smart technologies solve problems, effective technologies prevent them. What are DNS? DNS acronym ...
861
Read

11/08/21 | Cyber
PEBKAC: the problem of level 8
PEBKAC. Never heard this word, of nerdy origin but which represents one of the biggest and most difficult plagues ...
2392
Read

09/08/21 | Cyber
Windows 11, an even safer operating system
We want to move people from needing Windows, to choosing Windows, to loving Windows. [Satya Nadella] Microsoft had ...
1860
Read