24/05/21 | Cyber
Know the opponent's cyber tactics
Any IT security and cyber protection activity is based on the determination of a border to be guarded (the security perimeter) and on the ...
2356
Read

17/05/21 | Cyber
Venticento: a Made-in-Italy excellence in IT security
In other articles we have already dealt with the SOC (Security Operation Center) defining it as a complex organizational unit, generally centralized, which deals with ...
846
Read
10/05/21 | Cyber
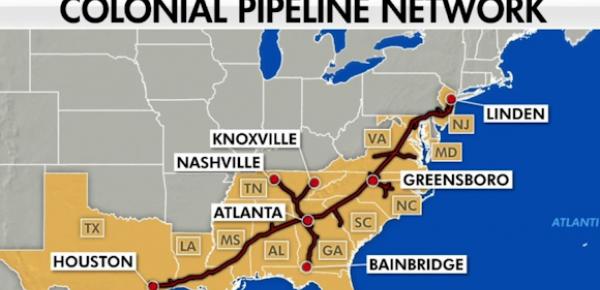
How vulnerable is the US energy infrastructure?
This is what Americans are discovering these days. Sure, it's not the first time this has happened, but it's probably the first time a problem of this size has happened. There...
1495
Read

03/05/21 | Cyber
The rise of cyber crime
It might sound like a movie title, but it's not. It is much more simply a trivial reality! Every day the news about hacker attacks, carried out in ...
453
Read

26/04/21 | Cyber
l CISCO Co-Innovation Center in Milan one year after its opening
In January 2020, the Cisco Cybersecurity Co-Innovation Center opened in Milan, within the structure of the Science Museum, the first in Europe. A little more than ...
716
Read

19/04/21 | Cyber
Locked Shields: the largest cyber tutorial in the world. This year Sweden wins
Also this year, between 13 and 16 April, the cyber exercise Locked Shields was held. As every year, the preparations and the conduct of the exercise have seen ...
1736
Read

12/04/21 | Cyber
Facebook Data Public Disclosure and the disturbing feeling of addiction to the data breach
Technology is no exception, as every other area of society has its arguments and some magic words that are on everyone's lips. Cyber security ...
536
Read

05/04/21 | Cyber
The Quantum-Secure Net project (part 3/3): European product of QUANTUM KEY DISTRIBUTION
The following is the third and final part of the series of articles on quantum cryptography, which began with the previous two articles, where the elements were introduced ...
521
Read
29/03/21 | Cyber
What is the cyber kill chain?
In several articles we have mentioned the so-called "cyber kill chain" but on closer inspection we never really ...
7868
Read

22/03/21 | Cyber
Whaling: what it is and what are the risks
In recent years, cyber attacks have evolved, changing shape and intensity. The global health crisis has ...
895
Read

08/03/21 | Cyber
The SolarWinds case, let's take stock
In an article from December 14, 2020, we talked about FireEye and how it was hacked. It was the same company ...
796
Read
03/03/21 | Cyber
The cyber national security perimeter: a new challenge for general counsel and compliance officers
In the difficult moment of reconstruction that will follow the great economic crisis caused by the pandemic, one of the assets ...
639
Read

01/03/21 | Cyber
The Quantum-Secure Net project (part 2/3): European product of Quantum Key Distribution
In the first article we introduced what are the main problems of modern cryptography, or rather, what ...
926
Read

22/02/21 | Cyber
TryHackMe: cyber and gamification
Some time ago I told you about the Ares project, an online platform developed according to the concept of ...
1604
Read

15/02/21 | Cyber
Microsoft: security and privacy at the time of Covid
A few months ago we talked about the importance of security and privacy at the time of COVID (see article) ...
345
Read

01/02/21 | Cyber
CyberChallenge.it, the 2021 edition at the starting blocks
CyberChallenge.it is one of the many answers that Italy is giving (together with new degree courses, ...
748
Read

25/01/21 | Cyber
The Quantum-Secure Net Project (part 1/3): The quantum threat to modern cryptography
This article is divided into three parts, and aims to retrace the main elements of cryptography and ...
1150
Read

18/01/21 | Cyber
The AIDA project: Artificial Intelligence at the service of law enforcement
The postulate of the eternal struggle between cops and thieves is also confirmed in its digital transposition. The...
983
Read

11/01/21 | Cyber
Money muling: a way to launder money
In this article I will talk about "money muling": an illegal practice that favors drug trafficking, trafficking ...
1442
Read

04/01/21 | Cyber
2020: a year of hacking
Cyberspace is the most complex thing man has ever built: on the one hand, it represents the union of thousands of ...
1349
Read