04/08/21 | Cyber
A new way to certify open-source software. The challenge of the AssureMOSS project
Europe is largely dependent on open-source software designed primarily overseas. Within the European Digital Single Market, most software is ...
644
Read

02/08/21 | Cyber
Internet-of-Things, a systemic risk technology. Here because
For Internet-of-Things (IoT) we mean all those technologies that enable the use of intelligent objects, i.e. sensors and actuators which, connected to the internet, ...
727
Read
28/07/21 | Cyber
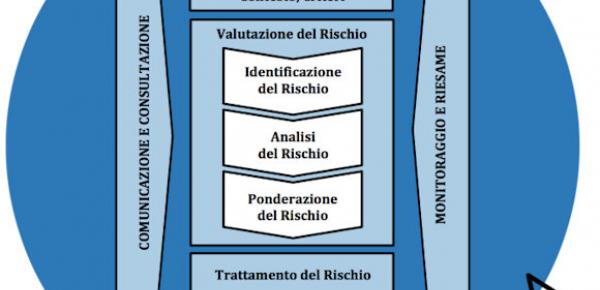
Cybersecurity: prioritize remediation of the vulnerable surface
Prioritization is the art of answering the questions "where do I start?" and "with what do I continue?" In this article we analyze how to compare theory and practice to solve ...
1027
Read

26/07/21 | Cyber
Windows versus Sourgum
It is Saturday 17 July 2021 and together with Alessandro Rugolo, Danilo Mancinone, Giorgio Giacinto and their respective families we are near Dorgali, a small town in the center of ...
1367
Read

21/07/21 | Cyber
Estonia and Russian Special Services influence operations in Cyberspace
According to the annual report "International security and Estonia" of 2021, Russia continues to be the main threat to Western democracies, even in cyberspace. The...
509
Read

19/07/21 | Cyber
Artificial Intelligence: evasion techniques and cyber defenses
It is counterintuitive to the idea of rationality, speed, effectiveness and efficiency that we have made of computers, but the reality is that artificial intelligence systems (AI ...
579
Read

14/07/21 | Cyber
Fake News, Deepfake, Fake People: the new frontier of Cyber Security
During last year's lockdown I started writing an article that never had the light and which had the aim of making people reflect on the phenomenon of fake news that I have ...
1554
Read

12/07/21 | Cyber
From raw data to usable information: visibility and observability
Once upon a time there was traditional IT ... In a well-defined and limited company perimeter, servers, routers, switches, workstations, laptops, firewalls, and various other entities coexisted ...
457
Read

07/07/21 | Cyber
Confidentiality - Integrity - Availability in Operation Technology from an Industry 4.0 perspective: part two
An automated production system managed in Industry 4.0 necessarily has an internal / ...
285
Read

06/07/21 | Cyber
Surviving under attack: cyber resilience
As repeatedly recalled on these pages, and reiterated a few days ago by the Delegated Authority of the ...
666
Read

05/07/21 | Cyber
The Operating System: the soul of PCs
We can say that the first great IT revolution took place with the birth of the Operating Systems which ...
3915
Read

30/06/21 | Cyber
Social Engineering: Why Should Companies Fear It?
“Cyber security is difficult (maybe even impossible), but imagine for a moment that you have succeeded. There...
1050
Read
28/06/21 | Cyber
Confidentiality - Integrity - Availability in Operation Technology from an Industry 4.0 perspective: part one
With this study we want to invite you to learn more about the world of Operational Technology (OT) with reference ...
554
Read

23/06/21 | Cyber
Diversity & Inclusion: the cyber protection of vulnerable groups
In cyber risk assessment, the consideration of a large slice of vulnerability is based on evidence and ...
394
Read
21/06/21 | Cyber
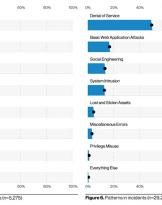
Security and DevOps: what does "shift left" mean?
In the DBIR (Data Breach Investigations Report) 2021 document released in May by Verizon we analyze the ...
1610
Read

16/06/21 | Cyber
Microsoft PowerShell and the new frontiers of malware
Most Microsoft Windows users (in particular, system administrators) will have heard of ...
2078
Read

14/06/21 | Cyber
Consume Cyber Threat Intelligence
Work often leads me to have conversations with clients about CyberSecurity, their programs, their ...
549
Read

10/06/21 | Cyber
International alert! When the cyber-enemy breaks through the closet ...
Since the 70s, social and technological evolution has progressively changed the paradigm ...
860
Read

07/06/21 | Cyber
Vaccines and dark web
COVID 19 has affected our lives over the past 18 months forcing us to change our lifestyle habits ...
616
Read

02/06/21 | Cyber
"Networking" to defend the "network": the MITER ATT & CK case
As mentioned in my previous article, any hacker has an "attack operating profile", recognizable by the ...
728
Read