What I am about to describe to you is an event that often happened years ago but now, fortunately, it has become rather rare: we are on a web portal that collects movie reviews and we want to look for one on “The Man Who Knew Too Much”. We identify the portal's internal search engine, insert "best films of the year" in the available field and click on the "search" button.
At this point, our browser reports a strange response page in which there are recognizable parts of the portal but they are badly formatted, pieces of programming language ... What happened?
If instead of looking for another movie portal, we dwell on that strange event, with the help of Google we could discover that to cause that disservice was a character contained in the string "The man who knew too much": the apostrophe.
In a programming language the apostrophe (or superscript) can have enormous importance and if the script that manages the search within the portal in question does not take this possibility into account, then that script and the module it governs are vulnerable. .
What does vulnerable mean in practice? It means that that module can be used to insert malicious code that could compromise the functionality of the portal or worse, expose all the data of other users registered in it.
Nowadays there are many tools that try to repeat the event described above. Usually it is sufficient to provide the address of the website to be analyzed: the tool navigates through the pages of the site in search of a module to attach and, if it finds it, tries to insert parts of the code. If it receives a known response, then it marks that page as "vulnerable". Unfortunately, however, that of the example is one of the most classic vulnerabilities; there are thousands of others and new ones come out every day. Similarly, the tools used to find these vulnerabilities are functional one day, useless the next day because they are obsolete.

So? Fortunately, there are free tools such as OWASP ZAP (Zed Attack Proxy), a tool created following the principles of the OWASP Foundation (Open Web Application Security Project) in order to offer everyone the opportunity to analyze their applications and websites, making them more safe.
ZAP is a tool within everyone's reach, from the most inexperienced user to the professional in the sector; it is open-source and contains most of the vulnerabilities still present and is constantly updated by a dedicated community.
Installation
As said, ZAP is open-source, for which it is free to download at this link (https://www.zaproxy.org/download/); the only prerequisite it requires is the presence of Java 8+ with which to make all its modules work. One of its peculiarities is precisely that of being available for many types of platforms and operating systems, and a version that can be used on Raspberry is even available.
Once downloaded, the installation procedure is really simple and intuitive.
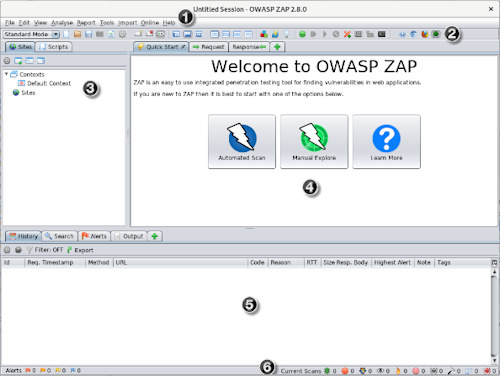 operation
operation
ZAP It is mainly a proxy and in fact it stores all the data coming from the site we are analyzing and processes them by submitting them to the archive of the vulnerabilities it possesses. For this ZAP has two analysis modes: the default is the scan that we can call "light" but if you want you can increase the brutality of the attack to make a more in-depth analysis. This last mode naturally implies an increase in terms of execution time, performance usage and stress of the application or website.
Opening it, the first thing we notice is its main module, the scanner: just enter the URL of the site we want to analyze and ZAP will report all the oddities in the form of colored flags based on the severity of what was found.
The ZAP Spider analyzes every piece of code and catalogs what it finds according to the severity and type of vulnerability; each warning is expandable and accompanied by both a brief explanation and a link on which to find more detailed information (in addition to the strategies to avoid the identified vulnerability).
Very often, the first thing we will get will be a considerable amount of information, much of it perfectly useless for our purpose; this is because it is necessary to waste some time in profiling ZAP correctly and adapting it to your needs. However, the advice is to deepen the knowledge even of this information that may seem useless, since in the future they could be a symptom of a new vulnerability.
Like all tools of this type, only practice and knowledge can increase their potential for use.
The scan is active
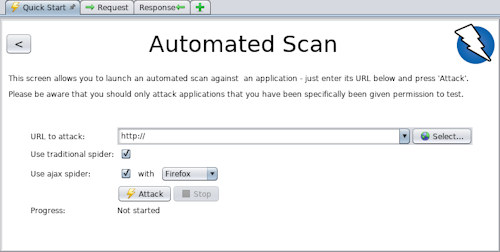
With active scanning it is possible to use the browser integrated in ZAP and, once you have found an element of the site that we consider sensitive, with the right mouse button you can have it analyzed, greatly reducing time and avoiding putting the entire structure under stress. .
This is a very convenient solution for those who are already quite practical and want to conduct targeted searches without wasting time and without committing their workstation by cataloging useless data.
Sessions and Reports
At each use, ZAP asks the user if he intends to create an active session of the analysis that is about to be carried out or a temporary one. The discriminating factor in the request lies in the use you want to make of the data that will be collected: in an active session all the scans are stored locally to be analyzed more in depth at a later time.
The Market Place
As mentioned, ZAP is also oriented to the professional sector, so it is possible to customize it by enabling or disabling types of attacks or by using the included store where it is possible to purchase additional analysis modules, created and certified by the OWASP community. Among the modules on sale there are many in trial version or even in beta testing to allow users to experiment with new types of vulnerabilities and subsequently report the results of their assessments to the community.
To conclude
ZAP is part of the large family of "PenTesting Tools" (Penetration Testing) and basically simulates an attacker who really wants to find a vulnerability and take advantage of it: I don't think it is useless to remember the criminal consequences if this tool is used without explicit authorization from the owner of the site in question.
ZAP is just one of the many projects of the OWASP Foundation born with the intention of helping those who develop or use web applications and who often, either out of haste or inexperience, avoid those precautions that, unfortunately, become facilities for malicious people.
To learn more:
https://www.zaproxy.org/community/
https://www.difesaonline.it/evidenza/cyber/sicurezza-e-devops-cosa-vuol-dire-shift-left












