PEBKAC extension. Never heard this word, of origin nerd but which is one of the biggest and most difficult to solve problems of computer security?
It's an acronym, it means Problem Exists Between Keyboard And Chair - that is, the problem lies between the keyboard and the chair.
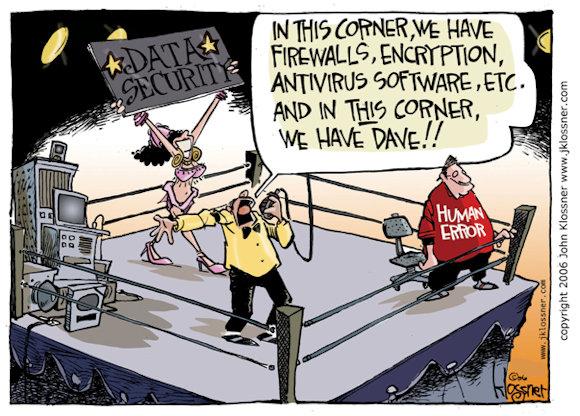
Others call it HF to indicate it Human Factor - the human factor; still others affectionately use the name Dave, based on a well-known 2006 cartoon on data security, drawn by cartoonist John Klossner.
All to indicate something dangerous, apparently harmless, but which cannot be - or at least it is inconvenient - to eliminate: the unaware user.
This article therefore has the ambitious goal of describing the risks of this unawareness, hoping to stimulate in each reader a reflection that increases awareness of the risk.
So imagine our Dave - a human resources employee at Acme Farmaceutici SpA - while he checks his email in the morning and receives a LinkedIN contact request from a certain Fiammetta Canestrelli, who says: “Dave, how many years have you been in high school? I certainly remember you well and I would like to have you in my professional network. "
Dave doesn't remember Fiammetta well - strange because with such a particular name - but if she remembers him why not get closer?
Dave therefore finds that invitation irresistible - perhaps thanks to the image of the blue-eyed brunette who stands out on the profile page to which - clicked on the email link - he accesses to confirm the contact ... certainly not paying attention to the intermediate site from which the connection pass after clicking on the link.
Site whose URL was displayed for less than a second in the status bar of the browser, but which served a system to intercept a lot of information on the connection, before redirecting it to the official LinkedIN site.
If Dave had tried to look for that nice pair of blue eyes in an image search engine he would have found dozens of results in addition to Fiammetta's professional profile: eyeliner ads, model casting agencies, online photo editing tutorials ... none of which Fiammetta mentioned.
Instead, visiting the profile, he discovers that his alleged ex-schoolmate has a very respectable experience in the field of cybersecurity, with years spent in the most important companies and two university masters in the United States; he is almost happy to have been his schoolmate.
Happiness that he finds a few days later when he sees the requests via Facebook and Instagram, thanks to which Fiammetta's photos multiply in other contexts: evenings in clubs, portraits in costume by the sea, there is also the photo in full-body suit from which he must have taken that of the professional profile ... a really nice girl, Dave thinks.
So when via Messenger you receive the link to visit Fiammetta's blog with many articles on how to make bread and great leavened products, click on it without thinking twice.
What Dave does not know is that the combination of his actions has led to another pair of eyes, not blue or even belonging to the girl, to have excellent visibility on his corporate PC remotely connected - due to a pandemic - to the human resources systems of the company. Acme Farmaceutici SpA.
Thanks to a piece of software downloaded in a totally oblivious and transparent way from the blog, two skilled hands run on a keyboard - guided by a brain trained in computer compromises. A connection that starts from Eastern Europe slips into untraceable networks up to Dave's laptop, from here via VPN it lands on the application with which ACME manages employee data. Operation not immediate thanks to the use of complex passwords that ACME imposes on its human resources employees ... other than those they use for personal use such as social networks.
But made enormously easier by Dave, who hates this practice and has memorized the password to log into the system directly in the browser, so he doesn't have to remember and type that complex 15-character sequence all the time.
And thank goodness that by accessing the VPN, ACME's IT does not require a one-time password, because the channel is safe!
The following month, ACME's CISO receives one of the worst emails of his career. “We have the complete database of employees: personal data, health status, work history and details of salaries, bonuses and family members to contact in case of an emergency.
In 48 hours this information will be made public, if we do not receive the sum of 20BTC (currently more than 666 thousand euros, NdA)"
After recovering from the shock, the CISO summons the company's crisis unit and prepares to explain how the hell an accident of this severity could have happened. despite the exorbitant investment in security technology that the company has made over the years.
Investment that provided for the reinforcement of the protection on corporate emails, anti-malware state-of-the-art authentication protection systems, VPNs for connecting remote employees (severely tested by the pandemic), even penetration testing and ongoing no compromise testing performed twice a year - the latest last month.
A protection that covered all seven levels of the ISO / OSI reference model for interconnection and communication between heterogeneous systems: physical, data-link, network, transport, session, presentation and application.
All!
Except for one small but important flaw at level 8: Dave.