07/10/19 | Cyber
HOW-TO: How to build your own "homemade" Firewall
A practical way to save and keep your data safe. In this period in which the finances of companies and public administrations are put to the test, it is easy ...
12473
Read

02/10/19 | Cyber
Cybertech 2019: many words and many good intentions. But the war has already been going on for years ...
In an important period for innovation and digital growth in Italy and throughout Europe, Cybertech, as it has for four years now, reaffirms itself as the main...
315
Read

23/09/19 | Cyber
Stories and anecdotes of a computer pioneer
Not quia difficilia sunt non audemus, sed quia non audemus difficilia sunt. (It is not because things are difficult that we do not dare, it is because we do not dare that they are difficult.) Lucio ...
1145
Read

16/09/19 | Cyber
Cortana, what happens when "le" is asked to try out a mission to the limit?
Cortana, artificial intelligence from Microsoft with a name borrowed from a character from the Halo videogame, what happens when "her" is asked to try her hand at a ...
1796
Read

14/09/19 | Cyber
Biometric Authentication: where we are and what impacts
It's been 23 years since Peter Steiner published the infamous cartoon "On the Internet, Nobody Knows You're a Dog" in The New Yorker, illustrating and, to some extent, ...
1044
Read

12/09/19 | Cyber
F-35: analysis on cyber risks of fifth-generation fighters
The following article is for purely informative, illustrative and study purposes. The "tests" performed in the article are not real tests on the infrastructures or networks of others, but ...
3200
Read
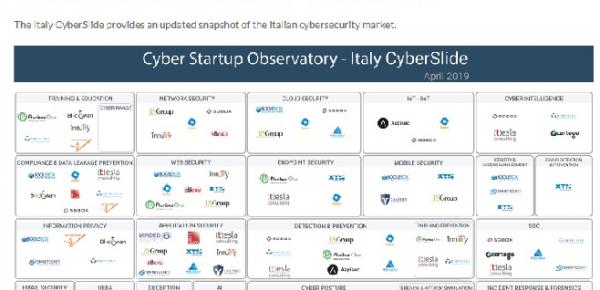
05/09/19 | Cyber
Create an innovative cyber startup: the main opportunities in Italy
We can say with certainty that MSME (micro and small-medium enterprises) represent the "backbone" of the Italian economy. In fact, considering the only "micro" (ie ...
1182
Read

02/09/19 | Cyber
Protection from cyber-risks: at what point are they and what should cyber insurance cover
Interestingly, in a recent article in The Insurance Insider, a world-class insurance broker (AON) stated that according to data he collected for ...
199
Read
21/08/19 | Cyber
Quantum Computing and Cryptography
The Human Being, by its nature, needs to evolve and communicate. Communication is one of the aspects ...
4065
Read

12/08/19 | Cyber
Sea Turtle: attack on the entire structure of the Internet
Among the numerous cyber attacks that are discovered, reported (but never publicly admitted), often ...
1021
Read

05/08/19 | Cyber
Italian CyberChallenge: the experience of the team from the University of Cagliari
In the past we have given space to the activity called CyberChallenge.IT, with an article explaining the object ...
857
Read

30/07/19 | Cyber
Data, Information Security and Cyber space: protect billions of data or dollars?
Most scholars and policy makers say that cyberspace favors lawlessness while ...
326
Read

22/07/19 | Cyber
The Russian Sytech, FSB contractor, hacked !!! Projects and data made public
News begins to arrive, albeit with a delay. The one hit doesn't seem like a big one, it's not a big one ...
1393
Read
17/07/19 | Cyber
Regin, the RAT used against the "Russian Google" Yandex
In the world of computer security, the potential risks to companies and institutions, in the form of malware and toolkits ...
757
Read

11/07/19 | Cyber
Cybertech 2019 Tel Aviv: Israeli Excellence, a Military Model in favor of the Community and Innovation
That of the Tel Aviv CyberTech 2019 was a worldwide event, with hundreds of companies, guests and ...
709
Read

01/07/19 | Cyber
Metasploit, when the best defense is attack
In recent years we hear more and more often about "cyber attacks", "cyber warfare" and more generally about ...
3104
Read

25/06/19 | Cyber
BlackBerry
BlackBerry Limited is a Canadian company headquartered in Waterloo, Ontario, active in 30 countries. Founded in 1984 with ...
1549
Read

17/06/19 | Cyber
The NATO Cooperative Cyber Defense Center of Excellence celebrates the entry of four new members
Bulgaria, Denmark, Norway and Romania join NATO CCDCOE thus bringing the number of participating countries to ...
640
Read

10/06/19 | Cyber
Are CISCO routers at risk?
A few days ago, on Wired, an article with a disturbing title was published: "A Cisco router bug has massive ...
2312
Read