The following article is for informational, illustrative and study purposes only. The "tests" performed in the article are not real tests on the infrastructures or networks of others, but simple research and analysis of public data, found through third platforms.
Every real test MUST be performed after the WRITTEN CONSENT of the owner of the network or infrastructure being analyzed.
Any test performed without explicit written consent is ILLEGAL.
The Jet F-35 Lightning II is a fifth generation fighter, developed by the American Lockheed Martin, born as a multi-role stealth aircraft, for air supremacy.
Three different models have been designed:
- the F-35A CTOL model - Conventional Take-off and Landing, or a model with conventional take-off and landing
- the F-35B STOVL model - Short Take-Off and Vertical Landing, a short take-off and vertical landing model
- the F-35C CATOBAR model - Catapult Assisted Take Off, but a model with catapult-assisted take-off and cable-assisted shutdown.
 This model in particular, given the take-off and landing system, is designed for aircraft carriers.
This model in particular, given the take-off and landing system, is designed for aircraft carriers.
Since the aircraft must be able to operate in any situation and has different take-off and landing systems depending on the model, everything is transformed, from the technological point of view, into a very complex system, consisting of multiple sub-systems with components hardware and software interconnected.
The jet is designed to achieve aerial supremacy thanks to its armament and information sharing, for this purpose a real network has been created, with two support systems for pilots and operators to which the fighter is constantly connected thanks to two software systems designed for the purpose, the ALIS system and the JRE system.
The ALIS (Autonomic Logistics Information System) system supports aircraft maintenance operations, allowing operators to replace a component or simply control the status of the aircraft in a centralized manner, increasing the availability of the aircraft themselves.
 Moreover, through ALIS it is possible to create and maintain a planning of operations in a shared manner.
Moreover, through ALIS it is possible to create and maintain a planning of operations in a shared manner.
An in-depth study of this system is available, directly on the website of the hunting company (link).
The JRE system (Joint Reprogramming Enterprise) is a shared database, which allows the exchange of information between allies of an operation.
As an example, if an F-35 detects an enemy radar this information will be shared and all allies will know of the existence of that radar, making it easier to implement a possible strategy or simply avoiding that all allied forces should find the information in turn.
This type of information sharing is a key factor in the success of a mission, but since the aircraft system is connected to a network for exchanging them, this can hide major IT security problems that can compromise the result for which this fighter was created.
To be able to understand the risks deriving from these systems, we analyze both the systems aboard the fighter, and the network to which it connects, through an analysis of the public data, available on third-party platforms and available online.
The F-35 has a complex processing system, and every processing system has its own operating system.
An operating system (OS - Operating System) is software that manages both the hardware and software components of a computer.
 The operating system equipped by the F-35 is of the "real time" type, that is a particular type of OS that must respond to the elaborations in a predetermined fixed time, precisely in Real Time.
The operating system equipped by the F-35 is of the "real time" type, that is a particular type of OS that must respond to the elaborations in a predetermined fixed time, precisely in Real Time.
The OS in question is the INTEGRITY RTOS (an abbreviation of "Real Time Operating System"), developed by Green Hills.
Currently, this OS is present, as well as in the F-35, also in the B-2 stealth bomber, in the F-16 fighter, in the F-22 fighter Raptor and in the civil aircraft Airbus A380.
Having to manage systems of critical importance, the OS is protected by one sandbox, or a protected area isolated from the remaining hardware and software components.
To be able to better explain the concept of operating system in one sandbox, you can imagine a room (system), with a safe in the center (sandbox), protected with a strong combination (password) and perhaps with an alarm (Firewall).
Inside the safe (and therefore inside the sandbox) there is the "heart" of the system, which has the most value and carries out the most critical operations.
Protect the OS by enclosing it in one sandbox therefore it allows to raise the overall security level of the whole system.
Tale sandbox is made up of various components, such as Interpeak IPShell, Interpeak IPWEBS and Interpeak IPCOMShell.
The first serious risk is related to some vulnerabilities able to bypass the sandbox, to communicate directly to the operating system and be able to execute commands:
https://github.com/bl4ckic3/GHS-Bugs
The vulnerabilities have been recognized and marked with CVE (Common Vulnerabilities and Exposures), or rather the unique codes of recognition of vulnerabilities:
CVE-2019-7711 - https://nvd.nist.gov/vuln/detail/CVE-2019-7711
CVE-2019-7712 - https://nvd.nist.gov/vuln/detail/CVE-2019-7712
CVE-2019-7713 - https://nvd.nist.gov/vuln/detail/CVE-2019-7713
CVE-2019-7714 - https://nvd.nist.gov/vuln/detail/CVE-2019-7714
CVE-2019-7715 - https://nvd.nist.gov/vuln/detail/CVE-2019-7715
The vulnerabilities found are related to the version of Integrity RTOS 5.0.4
The second risk derives from the interconnected nature of the aircraft subsystems, this because if an attacker could penetrate an auxiliary system, for example the GPS, he could also gain access to the central system, compromising the entire aircraft.
This possibility, if combined with the vulnerabilities described above, could constitute a serious threat to the safety of the pilots and missions they carry out.
As previously stated, the true nature of the F-35 fighter is not that of being a "stand-alone" aircraft, but true evolution is the support and data exchange network with other aircraft.
 This great strength can easily turn into a vulnerability, since being connected to an external network, this is potentially attackable.
This great strength can easily turn into a vulnerability, since being connected to an external network, this is potentially attackable.
The hunting support network is made up of several national "hubs", or connection nodes, which however refer to two central nodes, managed by Lockheed Martin in Fort Worth, Texas, and Orlando, Florida.
In these two nodes all the information present in the peripheral nodes is conveyed.
Some experts have raised many doubts and controversies about the amount of information transmitted to Lockheed Martin and claim that they are more than necessary.
This type of network can pose a serious risk, as despite the fact that these data centers (ie a series of servers that process information received from external nodes) have extremely high security measures, if compromises were made, the entire network of connected fighters would be compromised, causing in the worst case the combat incapacity of the entire F-35 fleet.
This hypothesis, however incredible, is not to be considered remote, as there may be operators inside the datacenter who can make the most disparate operations by mistake (or, in the worst case, intentionally harmful) by exploiting their position.
This type of threat is called "internal threat" (or "internal threat").
This possibility of an internal threat, consequently, leads the experts to wonder if the data and the entire network relating to the missions is managed by Lockheed Martin in the most appropriate manner.
In this regard, we can try to find indicators of impairment, or "clues" that can be traced back to a possible compromise on Lockheed Martin's network.
Obviously this analysis is to be considered only an example, and the data obtained could prove to be false positives, as they could have been generated by honeypot (operating systems specially installed to divert an opponent from real systems) or from other alarm systems that have already neutralized a possible threat.
Furthermore, the analysis is carried out using exclusively data from public sources, and not directly on the network concerned, increasing the possibility of a false positive.
The platform on which we will perform the analysis is ThreatCrowd, a free platform, which draws on the data of other platforms such as VirusTotal, and draws a graph representing the connections made in a network.
The results returned by the platform can be of four types:
- IP - IP addresses connected to the domain under analysis, not necessarily malicious
- E-mail - Server or e-mail addresses connected to the domain
- Sub-domains - Sub-domains directly connected to the domain under analysis
- Hash - Alphanumeric strings representing files detected by the various platforms connected to ThreatCrowd, not necessarily malicious.
Here is the ThreatCrowd platform:

Source: https://www.threatcrowd.org/
In the search box, we enter the domain "lockheedmartin.com".
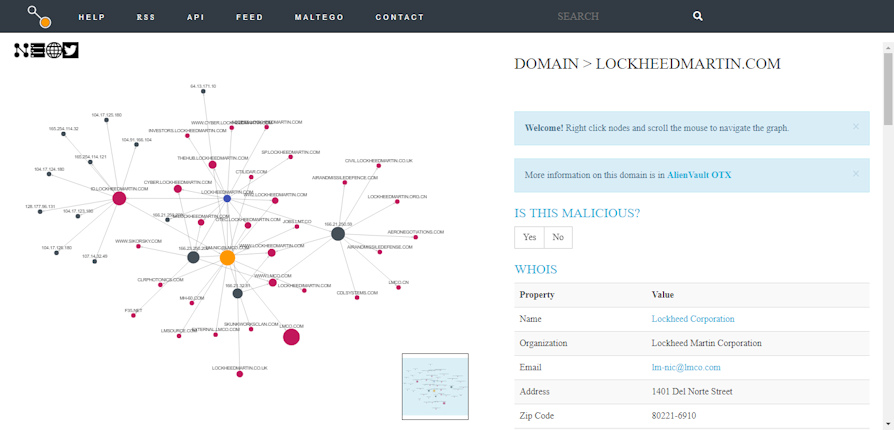
Source: https://www.threatcrowd.org/
The platform returns a graph of the connections that take place in the internal network, and in the various sub-domains:
By clicking on the appropriate button at the top left, we can analyze the result in table form:
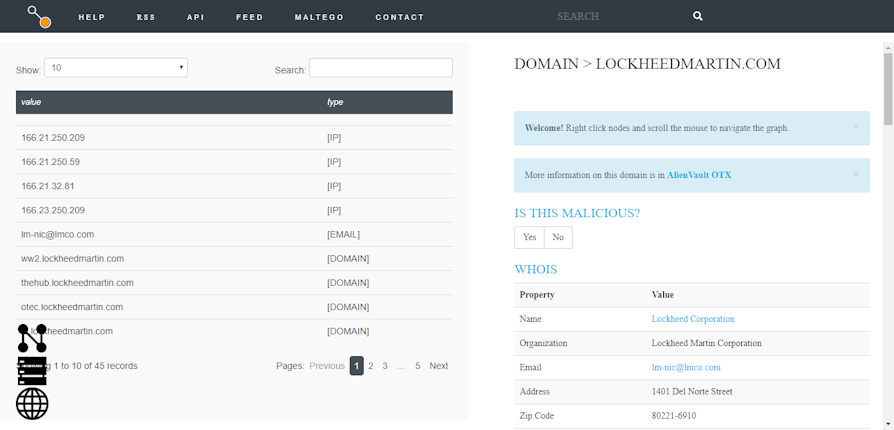
Source: https://www.threatcrowd.org/
Analyzing the result, we can see that there are no hashes, but only sub-domains, IP addresses and an e-mail.
The presence of hash on the platform is an indication that over time the various platforms from which ThreatCrowd retrieves data have signaled the presence of malicious files, in this case the hashes can be interpreted as virus "signatures".
Although this does not indicate direct compromise, as these alerts can also be generated by anti-intrusion systems installed to protect the Domain, this indication is certainly an important indicator, as it can highlight a possible past security incident.
Therefore, there does not seem to be any certain indicator of compromise, at least on the surface.
To go a little deeper, we need to individually analyze the results returned by ThreatCrowd.
The first result useful for analysis is the e-mail address. lm-nic@lmco.com of which the platform returns five useful hashes:
e21b3469b4fc1efddf76d8c89f1ebb2a
709622547c3e4b44144047282940995b
11769c481554f793ec20fe2b0189a751
4ca7d150cc798011d5cb7d4c5be89f41
9844a1b8a10ed4568240ae7a528bef5d
To verify that these hashes refer to malicious files, we insert these values on VirusTotal to examine the results.
VirusTotal is a particular platform on which the user can upload any type of file, to have them analyzed automatically by numerous antivirus engines.
The results of the virus scans are then shared on the platform, which checks the connections made by these files in one sandbox, to make the analysis more complete.
Since the platform can analyze files and websites, it appears to be a valuable tool in searching for indicators of compromise in external networks, without performing invasive analysis.
This is the result of VirusTotal of the first hash:
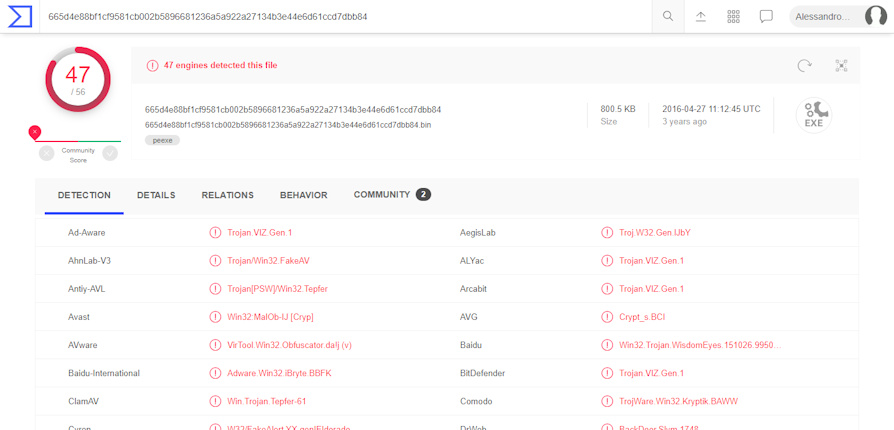
Source: https://www.virustotal.com
As you can see, this file turns out to be malicious, but to check if it can be a real indicator of compromise, we have to analyze if for the email detected there are recent reports for an alleged infection.
We cannot directly search for the e-mail address, but we can search on VirusTotal for the "lmco.com" domain.

Source: https://www.virustotal.com
As you can see, the platform detects that there are more than 10 suspicious files that communicate with the domain being analyzed.
To view suspicious files, click on "Relations"
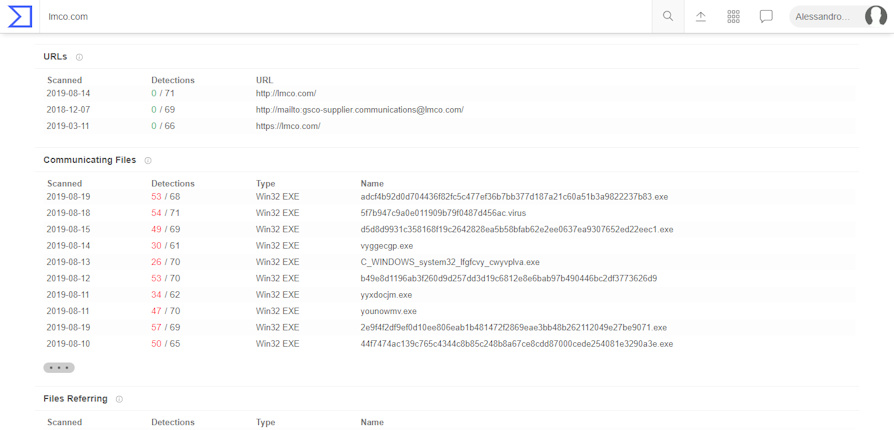
Source: https://www.virustotal.com
As we can see, there are many malicious files that communicate with the domain "lmco.com", connected to the domain "lockheedmartin.com", whose date (19 / 08 / 2019) is very close to the date of writing of the article ( 20 / 08 / 2019).
This can represent an ongoing attack, but since this can also derive from honeypot, Intrusion Prevention Systems (ie systems created to stop threats before they reach the servers involved), Antivirus or other analysis systems, once again we are not sure that there is really an attack (but it can still be considered an indicator of compromise) .
Another indicator can be seen by analyzing the domain "lockheedmartin.com"

Source: https://www.virustotal.com
In this case there are two detected files that communicate with the domain, with dates very close to the analysis.
There are also some files, in which the analyzed domain is present ("Referring files" section)
VirusTotal, in fact, not only analyzes the connections that are established by malicious files, but analyzes the contents of the files (body), and analyzes it in search of domains, IP addresses and text strings that can be useful for future analysis.
To get a broader view of the systems being analyzed, let's try to find on Shodan (a search engine created to search for devices connected to the Net) the string "lockheed martin":

Source: https://www.shodan.io/
As shown in the screenshot, we can see that there are servers, publicly accessible, that have the RDP (Remote Desktop Protocol - Remote Desktop) enabled.
This obviously cannot be considered an indicator of compromise, but it certainly represents a risk, due to the numerous vulnerabilities affecting this protocol.
With this we want to emphasize, once again, that this does not mean that the detected servers are vulnerable, but in the analysis is to be taken into consideration as a possible risk.
This type of analysis is useful because, since the internal network is not known, considering the worst case, an internal system could be connected to the central interchange hubs with which the ALIS and JRE systems communicate.
Although the analysis is external and all the limitations of the case have been taken into consideration, before the publication of this article the company has already been contacted for these indicators, as it manages a critical system.
 Limiting ourselves to the F-35 cyber risk analysis, I remember that the aircraft can equip B-61 bombs, or hydrogen nuclear warheads (the Lockheed Martin and F-35 systems themselves, therefore, are considered critical systems) .
Limiting ourselves to the F-35 cyber risk analysis, I remember that the aircraft can equip B-61 bombs, or hydrogen nuclear warheads (the Lockheed Martin and F-35 systems themselves, therefore, are considered critical systems) .
Obviously the F-35 is not affected only by cyber problems, in June 2019 only the 8,7% of the test fleet reached full combat capacity, compared to the budgeted value of 80%.
The program itself is very expensive, it is estimated that only Italy has spent 4 billion to date to finance the project, and currently in Italy there is a complete production line, managed by Leonardo, in Cameri (v.articolo)
The greatest risk, from this point of view, is purely industrial and is represented by the possibility that the Cameri plant could be without aircraft to be built by the 2023.
For Italy, this could really be a topic to be addressed quickly, since this risk can easily turn into a great opportunity for the country.
In addition to the cyber risks analyzed here and to the inefficiencies reported by the tests, it is to be added that new sixth-generation fighters are being tested and planned, but, since the development of these fighters is at an early stage, it does not represent a direct risk for the F-35.
To learn more:
https://it.wikipedia.org/wiki/Lockheed_Martin_F-35_Lightning_II
https://www.lockheedmartin.com/en-us/products/autonomic-logistics-information-system-alis.html
https://www.theregister.co.uk/2019/03/28/f35_software_fail/
https://www.documentcloud.org/documents/5000528-GAO-Cybersecurity-Report-2018.html
https://www.documentcloud.org/documents/5736009-FY2018-DOT-E-F35-Report.html#document/p8/a483617
https://www.theregister.co.uk/2018/01/30/f35_dote_report_software_snafus/
https://www.ghs.com/products/safety_critical/integrity-do-178b.html
https://www.pogo.org/investigation/2019/03/f-35-far-from-ready-to-face-current-or-future-threats/
https://www.dote.osd.mil/pub/reports/FY2018/pdf/dod/2018f35jsf.pdf
https://www.airforce-technology.com/features/future-fighter-aircraft-sixth-generation/
https://www.defenseindustrydaily.com/you-can-track-your-f-35s-at-alis-maintenance-hub-04368/
Photo: US Air Force / US Navy / Lockheed Martin












