(Sometimes they come back ...) A few months ago we stopped to analyze the cyber risks related to the F-35, this included an analysis of the network (obviously of what is publicly visible) of the manufacturer, the company Lockheed Martin (see article).
Today's article comes to life from a need that should be primary for anyone who wants to face the daily challenges related to information security, or changes in the "battlefield" and the threats involved.
To better understand the "change" of the scenario, it is a good idea for those who defend periodically to analyze their assets, as the attacker always tries to discover new weaknesses in the structure.
Leaving too much time means significantly increasing the risk.
In this article we will see precisely this change and we will be able to analyze closely how the situation is radically different for the same domain.
As always, the first step to be performed is the so-called "information gathering", ie the collection of information we need to perform the actual analysis.
In this case, we check whether valid indicators of compromise are present for the "lockheedmartin.com" Domain.
To simplify our work, we can use the VirusTotal API (Application Programming Interface - a series of functions that can be recalled to perform a series of operations even with different programming languages and third-party programs), to check whether a given file (or domain, in our case ...) must be deepened.

As can be seen, there are no files that can be considered suspicious, so we can perform a new search through the "ThreatCrowd" platform to search for other elements that can be related to the Domain and its sub-Domains:
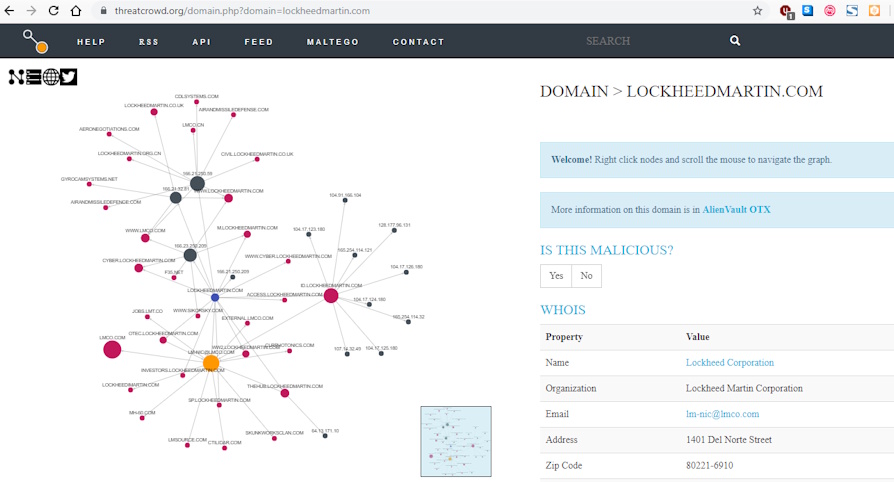 Source: ThreatCrowd
Source: ThreatCrowd
We can then view the data from the platform in tabular format: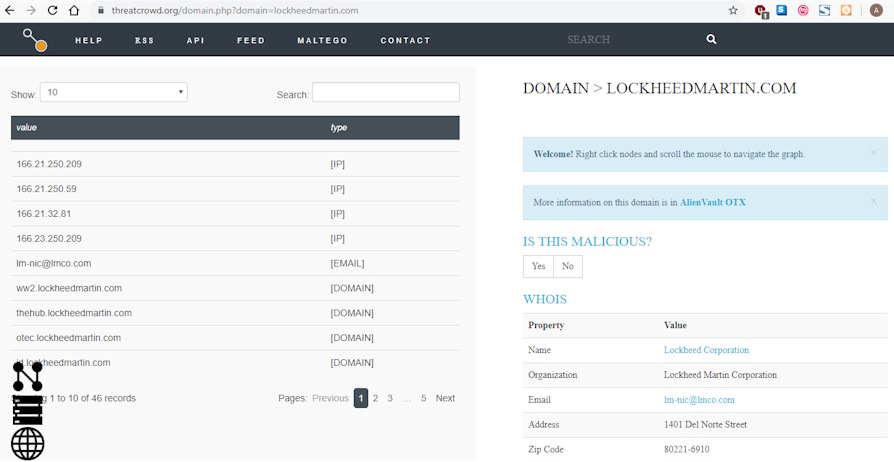 Source: ThreatCrowd
Source: ThreatCrowd
Among the information provided, the platform returns the email "lm-nic@lmco.com". At this point we can re-analyze the “lmco.com” domain and therefore observe the difference with the previous analysis. This time we will run this search with the VirusTotal API to make it easier for us:
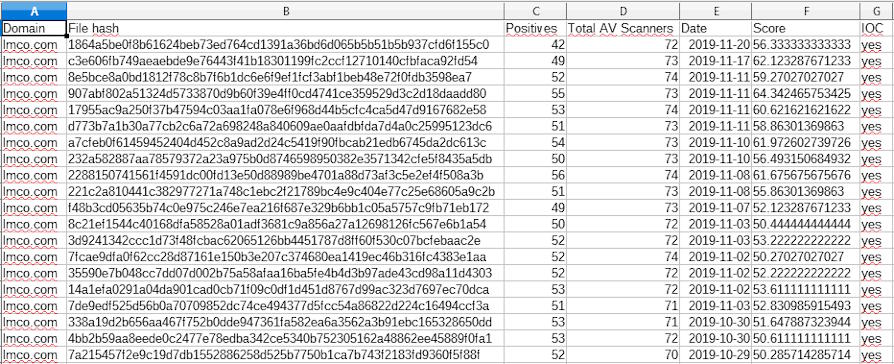
We can immediately observe that the situation has changed since the previous analysis, ie the same hash of the previous analysis are not present.
In a real analysis, we should analyze all the hashes found, to actually have a good overview.
In this case we will take as reference two hashes in particular, the first one:
1864a5be0f8b61624beb73ed764cd1391a36bd6d065b5b51b5b937cfd6f155c0
and the second hash:
907abf802a51324d5733870d9b60f39e4ff0cd4741ce359529d3c2d18daadd80
To study the nature of the first hash, we can always rely on the "VirusTotal" platform which, thanks to the analysis of the malware behavior, can provide us with an excellent insight into the Domains, the IPs contacted and the various changes to the system registry and file system that they can help us understand if a system is compromised or not.
You can observe the behavior of the first malware by simply clicking this link.
As can be seen, we have behavioral analysis.
By clicking on the "Full Report" button at the top right, you can view the sandbox report.
The sandbox allows you to run malware in an isolated and secure space, and analyze its actions to take the necessary actions, such as blocking IPs or malicious domains.
PLEASE NOTE:
Performing this type of operation is potentially harmful, as you literally run a malware on your own machine.
Perform this type of analysis ONLY AND ONLY IF YOU ARE PERFECTLY AWARE OF THE RISKS AND PERFECTLY ABLE TO MAKE IT IN TOTAL SAFETY!

Source: DrWeb vxCube
Analyzing instead the second malware, it is possible to notice something different:
From the analysis of the behavior it is possible to note that the malware, in addition to trying to contact the Domain of the Province of Milan, has a behavior of the singular, understandable from the analysis of the IPs contacted.
This below is the partial list of IPs contacted:
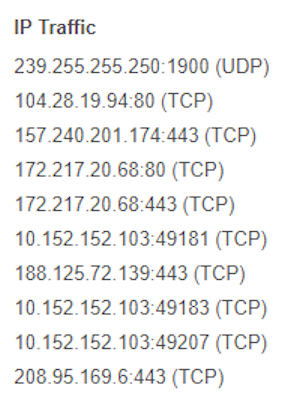
Source: VirusTotal
You may notice that the IPs contacted by the malware follow a particular “pattern”.
The interesting pattern is the "10.152.152.x"
This pattern coincides with the network of a widespread anonymization solution, namely Whonix.
Whonix is a virtual machine, whose Gateway automatically and "transparently" redirects (ie there is no need for interaction or knowledge of the operation by the user) the entire connection on the Tor network (the most common anonymization solution on the Web).
As reported on the official project page (available at link) to be able to redirect all the traffic of a client to Tor, through the Whonix Gateway it is sufficient to set the following parameters:
## increment last octet of IP address on additional workstations
IP address 10.152.152.50
Subnet netmask 255.255.192.0
Default gateway 10.152.152.10
Preferred DNS server 10.152.152.10
Interestingly, the malware tries to contact this type of network.
From this we can say that either it is a fortuitous coincidence, or we are faced with a possible case of a data leak.
Obviously, both the National CERT and the US-CERT were notified immediately.
I remember that all the analysis is based on publicly accessible data that can be consulted by anyone.
As done in the previous article we must warn you that since you do not have a view of the internal network, the situation could be the result of Antivirus, IPS, Honeypot, Sandbox or other defensive systems.
As shown, the situation between two analyzes can change radically, so I recommend a regular scan of your network and systems.
The advice is always the same: we must not see security as a "product", but as a process.
The study and relative analysis of the assets helps us to keep under control the threats, which are changeable over time and evolve with our defenses.
It is essential to keep track of changes and the evolution of threats so as not to be caught unprepared.
Images: Lockheed Martin / web












