As we have seen previously, SQLi are still fearsome despite their age. If anyone has missed the basic information on SQLi I recommend taking a look at the first article: SQL injection attack: what is it?
Naturally, the security industry has developed tools to combat SQLi, these are applications capable of filtering web requests and determining with good approximation whether they are legitimate requests or attack attempts.
Naturally, hackers also did not let themselves be discouraged and found a whole series of tricks to "bypass" the defenses, among these the attack called JSON - SQL bypass.
Let's try to understand what it is, but first a few words about JSON.
JSON is a data exchange format based on a subset of the JavaScript programming language, in fact it stands for JavaScript Object Notation.
Over time JSON has become the most used format in data exchange and databases have included JSON support in SQL. The same thing has not happened to many security tools which consequently are unable to identify SQLi attack attempts carried out with this technique.
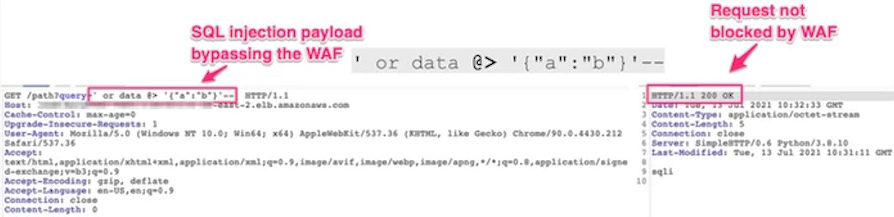
For example, if we consider a web application protected by a WAF and try to carry out an SQLi attack to try to exfiltrate data to which we do not have access, the WAF controls are generally able to identify the improper request and block the attempt. of attack. However, if an attack is attempted using a string in JSON format, the WAF is fooled by not being able to understand that the string contains an SQL command while the database is capable of correctly interpreting the command as it supports the JSON syntax.
The result is that the main WAF producers (Palo Alto Networks, Amazon Web Services, Cloudflare, F5, and Imperva) had to take action in 2022 by inserting rules to guarantee control of the JSON syntax.
The CLAROTY research team TEAM82 discovered this new type of attack.
Now, given that this is a fairly recent attack, I suggest that all those who use a WAF to protect their WEB services have specific tests carried out to check whether they are protected by JSON SQL Bypass.
There will be many who think that there is no need to be alarmed as it is a very complex attack to carry out: I advise the latter to pay close attention instead as SQLMap allows you to automatically search for sites vulnerable to JSON SQL Bypass attack.
SQLMap, easy-to-use opensource tool... No, that's another story!
To learn more:
- https://www.picussecurity.com/resource/blog/waf-bypass-using-json-based-...
- https://www.json.org/json-it.html
- https://claroty.com/team82/research/js-on-security-off-abusing-json-base...












