“Cyber security is difficult (maybe even impossible), but imagine for a moment that you have succeeded. Strong cryptography is applied where needed, security protocols perform their functions flawlessly. We have both reliable hardware and reliable software at our disposal. The network we operate on is also completely secure. Wonderful!
Unfortunately, this is still not enough. This wonderful system can do anything useful only with the participation of users.
People are often the weak link in a system of security measures, and it is they who constantly render them ineffective.
In terms of security, the math is flawless, computers are vulnerable, networks are bad, and people are just plain disgusting. "
(taken from: "Secrets and Lies: Digital Security in a Networked World", by Bruce Schneier)
Information is one of the most important assets of a company.
The information may constitute a trade secret of the company, for example in existing or possible circumstances it may serve to increase revenues, avoid unjustified expenses or help maintain a dominant position in the market for goods, works, services or bring other commercial benefits to the company . Consequently, such information must be protected.
Since people potentially move to work in any company, the influence of the human factor inevitably arises on all processes of the organization. Including the process of protecting confidential information.
Any human action associated with a breach of the security regime can be divided into two broad categories: intentional and unintentional.
Intentional actions include the theft of information from employees, the modification information or theirs destruction (sabotage). The latter is an extreme case and must be dealt with retrospectively, involving the police bodies.

unintended actions we mean, for example, the loss of storage media, the destruction or damage of data through negligence. The person in this case does not realize that his actions lead to a violation of the trade secret regime.
The same is true for any involuntary actions carried out for the benefit of the wrong people, often deceived through so-called "social engineering" techniques.
In many cases an employee does not realize that his actions may involve violations of the trade secret regime, but at the same time those who ask him clearly know that he is violating the regime.
Social engineering techniques
All social engineering techniques are based on the peculiarities of human decision making.
There are various techniques and types of social engineering:
- The pretexting it is an action elaborated according to a prescribed script (pretext). Consequently, the target (victim) must provide certain information or perform a certain action. This type of attack is usually used over the telephone. More often than not, this technique involves nothing more than simple lies and requires some preliminary research (for example, personalization: finding out the employee's name, position, and the names of the projects they are working on) in order to ensure credibility when we present ourselves to the target.
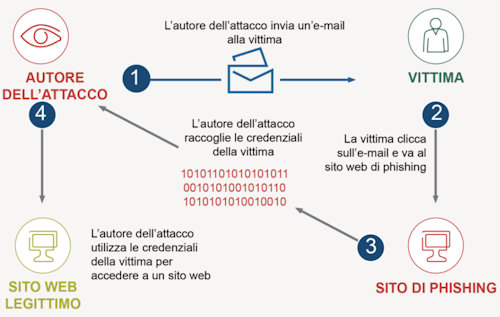
- The Phishing: a technique aimed at fraudulently obtaining confidential information. Typically, the attacker sends the target an email, forged from an official letter - from a bank or payment system - requesting that certain information be "verified" or certain actions taken. This letter usually contains a link to a fake web page, which mimics the official one, with a logo and company content, and contains a form that requires you to enter confidential information, from your home address to your credit card PIN.
- Trojan horses: This technique takes advantage of the target's curiosity or greed. The attacker sends an email containing an attachment with a major antivirus update or even new compromising evidence against an employee. This technique remains effective as long as users blindly click on any attachment.
- Road Apple: this method of attack is an adaptation of a Trojan horse and consists in the use of physical supports. An attacker can place a CD or a memory card, in fact, in a place where the medium can be easily found (corridor, elevator, parking lot). The vehicle is forged as official and is accompanied by a signature designed to arouse curiosity.
Example: An attacker could throw a CD with a company logo and a link to the target company's official website and label it "Q2010 XNUMX executive salary". The disc can be left on the elevator floor or in the hall. An employee may unknowingly take a disk and insert it into a computer to satisfy his curiosity.

- Quid pro quo: An attacker can call a random number from the company and present themselves as a technical support employee asking if there are any technical problems. If there are any, in the "fix" process, the target enters commands that allow an attacker to launch malicious software.
- Reverse social engineering.
The goal of the social reverse engineering it is to make the target go to the aggressor for "help". To do this, an attacker can use the following techniques:
Sabotage: creates a reversible problem on the victim's computer.
Advertising: The attacker slips the victim with an announcement like "If you have problems with your computer, call this number" (this mainly affects employees who are on a business trip or on vacation).
However, we can limit the percentage of being scammed and stealing sensitive data that could compromise our image and our daily life.
The most basic defense against social engineering is through education. Because whoever is warned is armed. And ignorance, in turn, does not exempt from responsibility. All company employees need to be aware of the dangers of information disclosure and how to prevent it.
In addition, company employees should have clear instructions on how and on what topics to talk to a generic interlocutor, what information they need to obtain from him for accurate authentication of the interlocutor.
 Here are some rules that might be helpful:
Here are some rules that might be helpful:
1. All Password user are owned by the company. It should be explained to all employees on the day of hiring that the passwords provided to them cannot be used for any other purpose, for example for authorization on Internet sites (it is known that it is difficult for a person to keep an eye on all passwords and access codes, so use the same password often for different situations).
How can this vulnerability be exploited in social engineering? Suppose a company employee is a victim of Phishing. As a result, your password on a particular website has become known to third parties. If this password matches the one used in the company, there is a potential security threat to the company.
In principle, it is not even necessary for an employee of the company to become a victim of Phishing. There are no guarantees that the required level of security will be observed on the sites accessed. So there is always a potential threat.
2. All staff should be educated on how to deal with i visitors. Clear rules are needed to establish the identity of the visitor and his / her companion. A visitor should always be accompanied by someone from the company. If a company employee encounters a visitor wandering around the building alone, then he must have the necessary instructions to correctly find out what purpose the visitor was in this part of the building and where his escort is.
3. There should be a rule for correct disclosure only the information that is really needed by telephone and in person, as well as a procedure to verify if the person requesting something is a real employee of the company. It is no secret that most of the information is obtained by an attacker during direct communication with company employees. We also need to take into account that in large companies, employees may not know each other, so an attacker can easily pretend to be an employee who needs help.
All the measures described are simple enough to implement, but most employees forget about these measures and the level of responsibility they are assigned when signing the non-disclosure obligations.
Thus the company spends huge financial resources to ensure information security by technical means that unfortunately can be easily circumvented if employees do not take measures to thwart social engineers and if the security services do not periodically check company personnel.
Image: Pluribus One / web