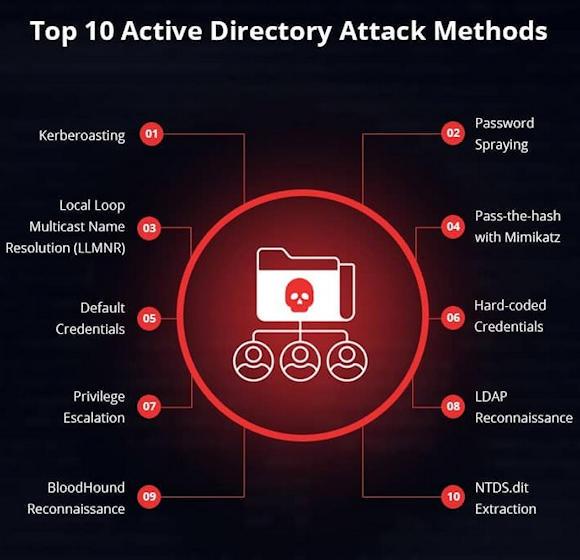
Reading while reading I came across one infographics really interesting. I must admit that infographics attract me for their ability to represent concepts in a clear and immediate way through diagrams or drawings. This way of representation often arouses my curiosity and so it was this time too.
This is a LinkedIn post published on a group (Ethical Hackers Academy) where ten methods for attacking Active Directory (AD) are represented.
And so, I thought it was appropriate to delve into it for a moment as more than once I realized that there are many who think that having an AD domain can be a security solver.
Like all systems, AD brings security benefits but it is not without limitations and vulnerabilities (and even more often of bad configuration!) and we will talk about this in this article.
But what is Active Directory?
A directory service, such as Active Directory, provides methods for storing directory data and making it available to network administrators and users. Active Directory stores user account information, such as names, passwords, phone numbers, and so on, and allows other authorized users on the same network to access that information. Active Directory uses a structured data store as the basis for a logical and hierarchical organization of directory information and contains information about Active Directory objects. These objects typically include shared resources such as servers, volumes, printers, and network user and computer accounts. Security is integrated with Active Directory through login authentication and access control to objects in the directory. With a single network login, administrators can manage organization and directory data across the network, and authorized network users can access resources anywhere on the network. Policy-based administration simplifies management of even the most complex network.
So let's not forget that AD performs certain functions and not all of them are security functions. AD serves as a centralized repository for some data, such data can be replicated and disseminated throughout a complex organization to ensure high availability of some services, performs security functions by allowing the use of various types of authentication, GPOs and workflows, performs audit on some events that can occur in the Identity Management system such as user authentication and can also perform Single Sign On functions.
Given the number and importance of the functions, it is therefore necessary to pay particular attention and ask yourself a question: what happens if AD is attacked?
Well, without wanting to be exhaustive, here are some types of attacks that should be studied to make them harmless or at least to realize you are under attack.
Kerber-roasting. According to the definition of CROWDSTRIKE, it is a post-exploitation attack technique (attack that tends to extend and elevate one's credentials when one is already inside a system). This attack consists in obtaining the hash of the password of an AD account that uses the SPN service (Service Principal Name: Identity Management service). Once the hash is obtained, the attacker deciphers the password and at this point he has everything he needs to impersonate the user and thus have access to all networks or systems to which he is authorized.
Password Spraying attack. Also according to CROWDSTRIKE, this type of attack consists of trying the same password against a list of users on the same application. This is therefore a brute force attack, easier to hide than the more common attack against a single user with multiple passwords. In this case Active Directory is used by the attacker to collect a list of active users on the system, but this collection of information can also be done in other ways, so in my opinion it is not correct to consider this type of attack among those that take it targets active directories. And let's move on to the third.
Local Loop Multicast Name Resolution (LLMNR). It is a protocol that allows name resolution in a local network thanks to the use of a multicast packet on UDP port 5355. In this case AD, if it does not contain in its GPO the indication not to use LLMNR, it plays the game of the attacker. Also in this case it is not a weakness of AD but an evaluation (hopefully) of the network administrator, in fact in some cases the use of LLMNR is useful, even if nowadays such cases have reduced a lot.
Pass-the-hash using Mimikatz. This attack technique consists in stealing credentials from AD. Credentials which can then be used to perform lateral movements within the attacked environment. To carry out this attack, it is necessary to extract the password hashes of the domain users, which are located in the Ntds.dit file, together with other information about objects and groups. So thanks to the use of a tool called Mimikatz it is possible to use the hashes to carry out the attack, impersonating any user of the domain.
LDAP Reconnaissance. The technique called LDAP Reconnaissance consists of an attack conducted from within the system and which aims to collect information from LDAP. This user information can then be used to conduct more sophisticated targeted attacks.
Bloodhound Reconnaissance. BloodHound is a tool that allows you to search for vulnerabilities in AD, but not only. BloodHound exploits graph theory to identify hidden relationships, permissions, sessions and possible attack paths in a windows domain. In theory, its purpose is to help cybersecurity experts defend their domain, but of course it can also be used by an attacker.
It must be said that in principle these are not specific attacks or tools for AD but are often valid also against other systems.
The list of ten attacks also includes truly generic attack techniques, not directly involving AD, in particular: default credentials, hard-coded credentials, privilege escalation. These techniques are not exclusively against AD but can be used against any computer system.
I always wonder the why of things, especially when I write.
A title can have a lot of influence in attracting or not attracting readers and readers don't always pay enough attention to what they read. The result is the usual: one is influenced, for or against a specific subject or idea.
In this case, of the ten attack methods against Active Directory, wanting to be wide-ranging, a maximum of six can be taken into consideration. In any case, I thank the Ethical Hackers Academy for giving me the opportunity for a little insight.
PS As always, thanks to SICYNT friends who wanted to contribute with suggestions and corrections
To learn more:
- https://www.linkedin.com/posts/mohessa511_activedirectory-kerberos-attac...
- https://www.crowdstrike.com/cybersecurity-101/kerberoasting/
- https://thebackroomtech.com/2018/08/21/explanation-of-service-principal-...
- https://www.crowdstrike.com/cybersecurity-101/password-spraying/
- https://www.blackhillsinfosec.com/how-to-disable-llmnr-why-you-want-to/
- https://www.blackhillsinfosec.com/?s=Active+Directory
- https://www.advantio.com/blog/attacking-active-directory-by-llmnr-nbsn
- https://blog.netwrix.com/2021/11/30/passing-the-hash-with-mimikatz/
- https://blog.netwrix.com/2021/11/30/extracting-password-hashes-from-the-...
- https://www.netwrix.com/ldap_reconnaissance_active_directory.html
- https://blog.netwrix.com/2022/12/09/bloodhound-active-directory/
- https://learn.microsoft.com/pdf?url=https%3A%2F%2Flearn.microsoft.com%2F...
- https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/plan/sec...
- https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/plan/sec....