Cyberspace is the most complex thing that man has ever built: on the one hand, it represents the union of thousands of networks that make it difficult even to have a snapshot of who is connected to it, on the other it is a sort of layering of software programs and protocols developed over the last forty years. This complexity generates vulnerabilities: from software errors to incorrect configurations and weaknesses in protocols, which are exploited by cybercriminals to steal data or cause damage.
Cybersecurity is considered one of the main emergencies around the world together with climate change and the migration of people and concrete initiatives are being studied to address this emergency. Blocking of company operations, surreptitious control of critical infrastructure services, theft of intellectual property or information crucial for the survival of a company, are examples of the threats that a country must face.
In an increasingly digitalised world, cyber attacks raise alarm in the population, cause significant damage to the economy and endanger the very safety of citizens when they hit distribution networks of essential services such as health, energy, transport, to say the critical infrastructures of modern society but also platforms that offer services that for many have become a commodity such as Netflix, Play Station, etc. In our country, entire sectors of excellence, such as mechanics, shipbuilding, Made in Italy, tourism, agri-food and transport, could suffer heavy downsizing of turnover due to attacks perpetrated in cyberspace by sovereign states or competitors.
A successful cyberattack could be a moment of no return for a company's credibility, business development and the ability to sell products under healthy competition. Equally, a successful cyber attack could destabilize the stock market by plunging entire countries into chaos or blocking gas supplies in the winter or the management of the municipal waste cycle.
 Many times the damage of cyber attacks depends on a weak link and often this is the human factor. Man is now an integral part of cyberspace and represents the most important and unpredictable vulnerability of this macrosystem. A wrong click can in some cases destroy any technological defense line of an apparatus, an organization, a country. They are the people who let themselves be "caught" by a phishing campaign, who use the name of the cat or the spouse as a password, who use the same smartphone to let their children play and to access the company network. They are the first to open doors for criminals to their organizations' sites, networks and databases, with dangerous and unpredictable effects.
Many times the damage of cyber attacks depends on a weak link and often this is the human factor. Man is now an integral part of cyberspace and represents the most important and unpredictable vulnerability of this macrosystem. A wrong click can in some cases destroy any technological defense line of an apparatus, an organization, a country. They are the people who let themselves be "caught" by a phishing campaign, who use the name of the cat or the spouse as a password, who use the same smartphone to let their children play and to access the company network. They are the first to open doors for criminals to their organizations' sites, networks and databases, with dangerous and unpredictable effects.
Not only industry, but also democracy can be subject to cyber attacks. "Fake news" is the evolution of attacks based on social engineering: created and spread through cyberspace, false information tends to confuse and destabilize the citizens of a country, plunging them into an uncontrolled information space, with an almost infinite set of news sources.
The year that is drawing to a close was the best commercial cybercrime could have. 2020 has been a difficult year for many reasons and, not least, the violations and attacks that have hit end users and organizations in all sectors indiscriminately worldwide. The ransomware threat dominated the headlines, with an endless stream of compromises affecting schools, governments, and private companies, which was also offset by a huge amount of hacked data. All while the criminals demanded ransoms worth millions of dollars.
Like every year, I love to trace the "best" of what happened in the past year. It is a way to become a child again, when on the last day of the year I sat in front of the television and, in love with sports as I have always been, I loved watching “A year of sport”.
Here, using a similar and, no doubt, more dramatic title, we can witness "A year of Hacking".
We can say that nobody is saved anymore and it is important to recognize how, especially with regard to the latest attacks, it is no longer to be considered a daring undertaking to associate the term "geopolitics" with digital. Indeed, geopolitics carries within itself a geographical reference, that of an analysis of the dimensions of power contextualized in the territory. For this reason, geopolitics has often shown limits, sometimes becoming the pretext for developing a rather dated realist thought, as it is very linked to borders and the extension of the domain of control. Following this trend, therefore, it may seem counterintuitive to associate a reflection on the consequences of digital in international politics with a geopolitical reflection, also because the digital world wide web conveys the idea of a "non-territory", or rather that of a territory universal.
The use of the term geopolitics, however, is not accidental: in the international scenario we are, in fact, increasingly witnessing a series of developments that tend towards a territorialization of the digital domain, a dimension that seems imbued with contradictory trends, between openings and closures but which shows a common denominator and that is the fact that cyber attacks have no borders, that they are perpetrated against critical infrastructures and operators of essential services and which, increasingly, take on a political dimension, capable of bringing individual countries.
The attack on Solarwinds
2020 has decided to leave us, as a last gift, one of the most devastating violations of recent years, not so much as an economic dimension, perhaps, but as an engineering and subtlety of the attack.
Hackers, which many public officials claim may have the Russian government behind them, have been compromising SolarWinds' Orion software distribution system since late 2019. As we have come to know, Solarwinds is one of the leading American companies in the world. development of network monitoring solutions used by tens of thousands of organizations. The hackers hacked the update servers and thus managed to generate a domino effect through which they would have the potential possibility of hacking all the company's customers.
It will take a long time for investigators to assess the damage. This is because not everyone who has installed the "malicious" updates has been attacked. What is certain is that security firm FireEye said the hackers searched for information about their government customers and stole non-public tools used by the Red Team to test the company's defenses. customer safety. Meanwhile, US officials have said dozens of Treasury Department emails have been compromised.
Although the full extent of such an attack and, above all, the effects of the breach will not be known until a few months, it is already clear that the attack on SolarWinds has highlighted how the "supply chain" can be weak and how in a similar scenario, the chain of which each company represents a link is extremely critical. Security cannot and should no longer be considered as an element that belongs to a single entity.
Importantly, the industry-wide compromise came to light from the FireEye investigation that was targeted by the attack and not by any of the government security agencies. Is it just a coincidence or does this episode demonstrate the different strength and capacity of companies in the IT security sector?
Massive compromise of Nintendo and Twitter accounts
In July, Twitter lost control of its internal systems due to a hacker attack carried out through a cryptocurrency-based scam. The breach was notable because it compromised the accounts of politicians, celebrities and business executives, many of them with millions of followers. Although the damage was modest in economic terms (around 100.000 dollars in Bitcoin and some personal data stolen) it is clear that an attack like this could have been used to do much more damage. Try for a moment to think about the effects that such an announcement could have on international markets in terms of their manipulation. Another element that made this attack particularly critical was who perpetrated it and the tactics used. Authorities accused a 19-year-old, XNUMX-year-old and XNUMX-year-old who allegedly used spear phishing attacks to steal an administrative password from a Twitter employee who was smart working during the COVID-XNUMX pandemic. Nintendo suffered a similar compromise in April.
Ransomware attacks at the University Hospital of Dusseldorf, Garmin and Foxconn
These are separate violations, but put together, they underline that there has not only been a price in money to pay for the organizations affected but also the impact on millions of people directly or indirectly involved. The decommissioning of the systems at the Dusseldorf hospital resulted in the death of a patient who, dying, was rejected by the emergency room and died while being transported to a more distant hospital. It is possible or even probable that the patient would have died anyway, but the compromise highlights, if it were still needed ☹, how cyber attacks can not only result in death but have an impact on social balance and on everyone's life the days.
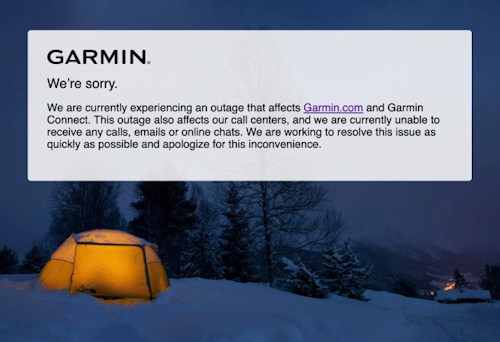 The attack on Garmin caused a four-day blocking of all GPS services not only for sports enthusiasts but also for airlines that needed to plan maps and flight routes.
The attack on Garmin caused a four-day blocking of all GPS services not only for sports enthusiasts but also for airlines that needed to plan maps and flight routes.
Another ransom note attack that attracted attention was the breach by electronic giant Foxconn. The attackers asked for $ 34 million to allow the company to regain possession of the data. It was the highest ransom note ever recorded, naturally among those made public.
Data breaches hitting Marriott and EasyJet
These were two separate attacks that had the same outcome: the compromise of personal data belonging to hundreds of millions of people. For Marriott this is the second time in three years. We're talking about an information leak for over five million guests. The EasyJet breach affected nine million passengers.
An iPhone zero-click exploit and the extraction of an Intel CPU crypto key
Not all hackers are bad. Indeed, very often, we are in the presence of "good hackers" who, at times, are so elegant that they are to be admired for their ingenuity and goodness of mind. In 2020, the best palm goes to Ian Beer, a member of the vulnerability research group of Google's Zero project. He devised an attack that, until Apple developed the update, gave him access to any iPhone that hooked onto his malicious Wi-Fi access point. Its attack did not require the iPhone user to do anything but showed how exploiting a vulnerability, in jargon exploit, could allow malicious spread from one device to another as long as they were part of the same area, in this case defined by a Wi-Fi network.
THEexploit is one of the most impressive hacking features in recent history and shows the damage that can come from a single vulnerability. It reminds a little of the example of the rotten apple. Apple developed the patch for the buffer overflow flaw discovered by Beer after being notified by Beer himself privately. Another of the Top attacks of 2020 was the extraction of a secret key used to encrypt the microcode on an Intel CPU; a first in the annals of security and the reverse enigineer. The key allows you to decrypt the microcode updates that Intel provides to fix security vulnerabilities and other types of bugs. Having a decrypted copy of an update can allow hackers to reverse engineer and track down the security bug.
There is an old saying in the security world that "attacks can only get better". 2020 has shown that the saying is absolutely true, and we can be sure, without a shadow of a doubt and without wanting to be birds of ill omen, that in 2021 it will be the same.
The hope is that this sentence - "A country that does not put cybersecurity at the center of its digital transformation policies is a country that puts its economic prosperity and independence at serious risk." - that has accompanied us over the years can finally be denied.
Happy 2021!
Further reading:
-
A Patient Dies After a Ransomware Attack Hits a Hospital | WIRED
-
Nintendo Breach: Now 300,000 Accounts Affected - Infosecurity Magazine (infosecurity-magazine.com)
-
Marriott Reports Data Breach Affecting Up to 5.2 Million Guests (bleepingcomputer.com)
-
EasyJet says 9 million travel records taken in data breach | TechCrunch
-
Foxconn electronics giant hit by ransomware, $ 34 million ransom (bleepingcomputer.com)
Photo: US Marine Corps / web