Last May some articles appeared that read that several European supercomputers (at least twelve) were hacked, access disabled, and they had to be shut down to restore their security conditions. It seems that the aim of the attackers was to try to exploit the enormous potential of supercomputers to "undermine crypto currency".
On 11 May, the supercomputer of the University of Edinburgh was attacked, on which a pandemic simulation program was recently installed, available to scientists and researchers in the field. The British National Cyber Security Center, immediately informed, worked together with the University technicians to resolve the problems encountered.
The supercomputer, called ARCHER, is a Cray XC30 model, equipped with 118.080 Intel Xeon E5 processors, a model that is now outdated and will soon be discontinued.
On the same date 5 other supercomputers in Germany were attacked and turned off. Same fate for some supercomputers in Switzerland and Spain.
The first analyzes showed that the hackers had access to the supercomputers through a "Secure Shell" connection, used by researchers to connect remotely. Once they gained access, they installed malware capable of undermining cryptocurrency.
According to some analysts, however, it would not be a common attempt by clumsy hackers to exploit the immense resources of supercomputers but a move by some States to disturb British research on the Coronavirus pandemic. Indeed, on closer inspection, shutting down some supercomputers cannot be considered a good method to undermine cryptocurrency!
The United States has accused China and Iran of being the architects of similar attacks against universities and research centers working on vaccines for Coronavirus.
If you access the ARCHER service page, you can see the impact of the attack on services.

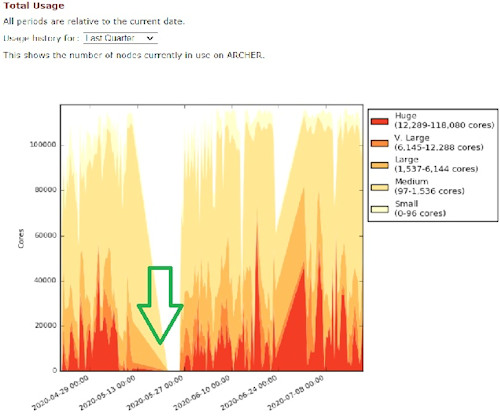 In the next image I highlighted the period of disservice, during which it is possible to see the total interruption until May 26th.
In the next image I highlighted the period of disservice, during which it is possible to see the total interruption until May 26th.
In the following period, work continued on various problems, apparently solved starting from 18 June. After June 18 it is possible to read that there have been electrical problems, which have also been solved since June 25.
If you take some time to read the comments on the incident in some forums, you can find different explanations of what happened and some users claim that what happened depends on the security architecture of access to the supercomputer, not correctly configured.
Unfortunately, I am unable to say what really happened, and I believe that only a careful analysis of all hacked supercomputers can give serious results.
Several technical reports, however, describe the incident, indicating cryptocurrency mining attempts, if this were true it could be assumed that a second Stratcom campaign was added to the hacker campaign, with totally different objectives.
One thing is certain though: if it is true that attacks on supercomputers have been - until now - a rarity, it is also true that for those who have an interest in cutting-edge technologies, for example in vaccines for Covid19, they represent prey coveted.
We will see what the future holds for us.
To learn more:
- https://www.bbc.com/news/technology-52709660?intlink_from_url=https://ww...
- https://www.theregister.com/2020/05/13/uk_archer_supercomputer_cyberattack/
- https://www.nytimes.com/2020/05/10/us/politics/coronavirus-china-cyber-h...
- https://www.theregister.com/2020/05/05/coronavirus_research_hacking/
- https://www.archer.ac.uk/status/
- https://tech.newstatesman.com/security/archer-supercomputer-cyber-attack
- https://www.cadosecurity.com/2020/05/16/1318/
- https://csirt.egi.eu/academic-data-centers-abused-for-crypto-currency-mi...












