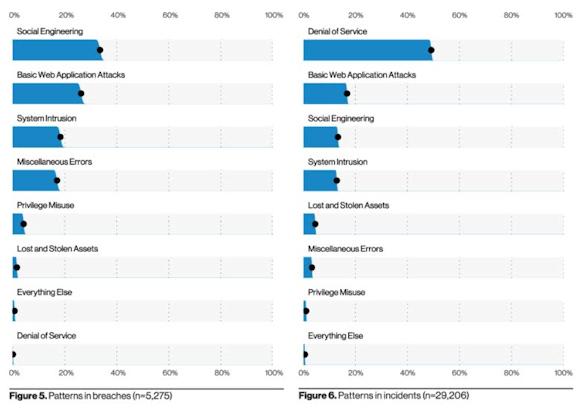
The DBIR (Data Breach Investigations Report) 2021 document released in May by Verizon analyzes the investigations on accidents and data breach computer scientists of the difficult year just ended.
Among the different evidences identified in the causes of accidents and data loss, one is striking both for the recurrence in both categories and for the position in the standings - second most important: attacks on web applications.
The combination of digital transformation of companies and the pandemic emergency have characterized important changes, which recently have enormously amplified the use of web applications for a large part of personal and professional productivity.
On the one hand, the much-deprecated "work from home" has actually proved to be an excellent solution, which has helped to mitigate the devastation that otherwise would have affected the operations of companies in an important way.
Companies that both managers and employees have shown remarkable creativity despite known infrastructural and operational problems.
On the other hand, there was an exponential increase in the attack surface exposed and the consequent risks of compromise.
The Open Web Application Security Project (OWASP) consortium maintains a list of 10 categories of severe vulnerabilities on web applications, in order to allow security teams to intervene in their control.
The problem remains in the lack of attention to apreventive digital hygiene and controls applied only when the application is published on the Internet, therefore reachable both by legitimate users and - unfortunately - by cybercriminals.
Another cause of weakness in web applications lies in the very wide intervals - sometimes even semesters or more - with which checks are carried out for the presence of vulnerabilities.
It is necessary to increase the level of maturity of companies and organizations towards this missing digital hygiene, with an action often referred to as shift left security.
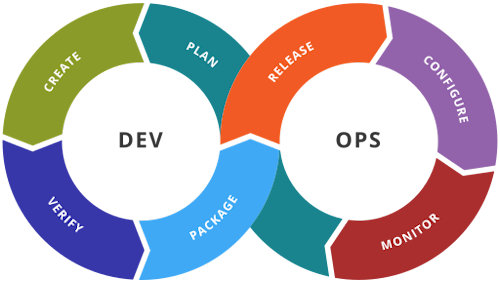
To better understand the idea, the process by which web applications are developed, verified and finally published must be analyzed, according to the dictates of the agile methodology that provides for Continuous Integration, Continuous Delivery / Deployment (CI / CD).
Often represented as a cycle that resembles the shape of mathematical infinity, the operational flow of continuous integration and implementation is frequently summarized with the term DevOps - indicating the close collaboration between the development team (Dev) and the operational management team ( Ops).
The important question at this point becomes: where to insert the security controls, to prevent vulnerabilities - therefore potential attack vectors - from being discovered when the application is visible and reachable by anyone?
Here is the idea behind “Shift Left Security”.
When an organization implements the DevOps paradigm, the process often involves adopting software platforms that facilitate the transition between the various phases of the cycle.
Examples of these platforms are Jenkins, Bamboo, TeamCity, etc.
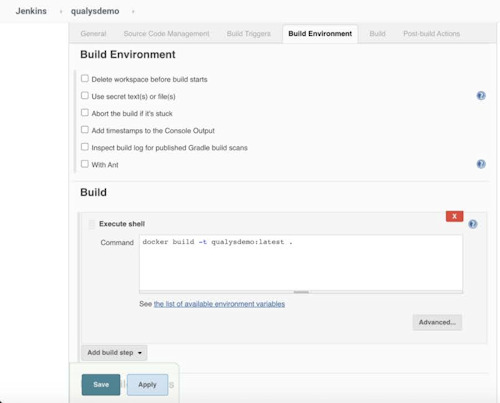 The logic used involves managing the various moments, such as retrieving the code from the centralized repository (eg. GitHub), executing the instructions to compile the application (phase of build), perform actions before or after the build (e.g. transfer the semi-finished product to another environment or run the compiled).
The logic used involves managing the various moments, such as retrieving the code from the centralized repository (eg. GitHub), executing the instructions to compile the application (phase of build), perform actions before or after the build (e.g. transfer the semi-finished product to another environment or run the compiled).
Most of these platforms are structured in an open way, supporting software plug-ins that allow to expand the basic functions provided by the platform.
Thanks to these plug-ins it is possible to integrate automatic security checks, so that they intervene in the steps between one phase and the next.
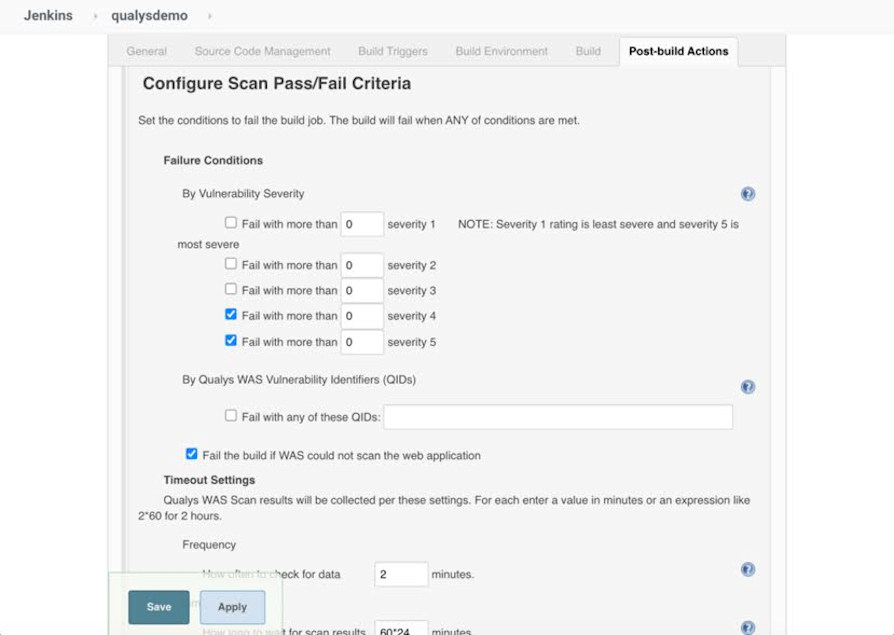
Depending on the plug-ins used, it is even possible to set security policies, based on which the build can end successfully or with error (bottom image).
For example, define that in the presence of software vulnerabilities beyond a certain numerical threshold or criticality, progress along the pipeline Other plug-in configuration options allow you to expose errors and security problems directly in the screen visible to developers, in order to make them autonomous in solving the problem.
In this way the security controls move more and more towards the origin, guaranteeing a better resilience of the application when it is finally promoted into production and mitigating the risk of cyber attacks.
The technique of "Shift left" it does not only concern the production pipelines of web applications, but is often adopted to implement the same level of agility in areas such as application containers, cloud resource training, server and client images, infrastructure.
In essence, it is a growth in the maturity of an organization's security program that manages to efficiently combine agility, operational speed and effectiveness in security controls.
Images: Verizon DBIR 2021 / web