In the collective imagination, volcanoes are often linked to the image of power and destruction. In Roman mythology, for example, Volcanos is the divinity who symbolizes the unstoppable force of nature and, in Ostia for example, the priest of Vulcan played a fundamental role in the life of the city.
Even today the Volcano fascinates but, at the same time, it inspires fear. Sometimes it can become the symbol of a nation, as in the case of Mount Fuji, an unmistakable icon of Japan. Other times, however, it becomes part of novels or films as happens in the Book of the Volcanoes of Iceland1 or in the film Secret Dreams by Walter Mitty2 where the eruption of the mountain, with its unpronounceable name, Eyjafjallajökull is of central importance.
You may be wondering what volcanoes have to do with cyber security. How come this introduction? If you want to find out, venture into reading this article.
So-called human-operated ransomware attacks3”Represent a significant and growing threat to companies and represent one of the most impactful trends in cyber attacks today. In these targeted attacks, which are different from self-spreading ransomware like WannaCry4 o NotPetya5, the opponents employ credential theft and lateral movement methods as attack criteria.
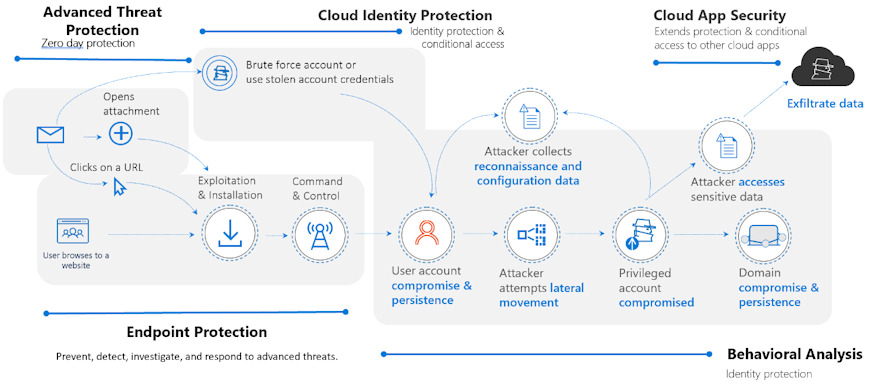 These attacks are known to exploit the weak points in the network configuration as well as any vulnerabilities of services or operating systems so as to distribute payloads6 malicious ransomware. And while ransomware represents a visible action, there are other elements such as malicious payloads, theft of credentials and unauthorized access that operate silently and steal data from networks, at which point, compromised.
These attacks are known to exploit the weak points in the network configuration as well as any vulnerabilities of services or operating systems so as to distribute payloads6 malicious ransomware. And while ransomware represents a visible action, there are other elements such as malicious payloads, theft of credentials and unauthorized access that operate silently and steal data from networks, at which point, compromised.
As for volcanoes, the news is very oriented to tell the effects that an eruption causes and, on the contrary, they tell very little about what is done to prevent them, so, information on ransomware attacks, too often, focus on down times which provoke, on the payments of the redemptions and on the details relating to the malicious payloads, not taking into consideration, however, the permanence of this type of campaign nor, on the contrary, the knowledge, sensitivity and ability to prevent them.
Working in contact with the Microsoft Threat Intelligence Team7, based on our investigations, these campaigns have shown that they are able to operate even in the presence of any restrictions and network protections. The compromises, in fact, take place starting from identity theft of credentials relating to users with minimum privileges and then to capture the credentials, instead, of users with higher privileges thanks to the use of dumping techniques of the credentials with which you have access to the network infrastructure in order to stay there as long as possible.
Human-operated ransomware attacks often start with malware such as banking Trojans or unsophisticated attack vectors which generally trigger alarms which, unfortunately, tend to be treated as irrelevant and, therefore, are not carefully studied and corrected. which are associated, at a later stage, with malicious payloads that also block antivirus and ransomware systems such as Revil8, Samas9, Bitpaymer10 and Ryuk11.
Fighting and preventing attacks of this nature requires a change of mindset that focuses on the complete protection of the attack chain, which is needed to slow and stop attackers before they can succeed.
And here, finally, we come to the volcanoes. One actor who has emerged overwhelmingly as responsible for these attack campaigns is an active, highly adaptive group that often uses Wadhrama ransomware12. As Microsoft we refer the groups according to a specific naming convention and in this case, the one used refers to the names of the volcanoes. Therefore, specifically, the group in question was given the name of PARINACOTA.
PARINACOTA is a group, as mentioned, particularly active, which operates with a frequency of three or four attacks a week to different organizations. During the 18 months it was monitored, changing tactics of compromise were observed with a variety of purposes including cryptocurrency mining, sending spam emails, or proxies for other attacks. The objectives and use of payloads have changed over time, influenced by the type of infrastructure to be compromised even though, in recent months, they have focused on distributing the Wadhrama ransomware.
The group is increasingly using a method called "smash-and-grab". Through this method, the group tries to infiltrate a machine and then proceed with a lateral movement to take possession of the largest number of machines whose disks are encrypted, and ask for the ransom; all in less than an hour.
 The attacks of PARINACOTA, in general, are of the brute force type13 and try to exploit the roads that are eventually opened on the servers that use the Remote Desktop Protocol (RDP) service exposed on the Internet, always, as mentioned, with the aim of moving laterally within a network or performing further activities outside the network itself thanks to the protocol in question if not properly covered by patches.
The attacks of PARINACOTA, in general, are of the brute force type13 and try to exploit the roads that are eventually opened on the servers that use the Remote Desktop Protocol (RDP) service exposed on the Internet, always, as mentioned, with the aim of moving laterally within a network or performing further activities outside the network itself thanks to the protocol in question if not properly covered by patches.
Attacks, in most cases, aim to compromise accounts related to local administrators of servers or clients. In other cases, however, the attacks are directed towards Active Directory (AD) accounts that use simple passwords, which never expire, such as service accounts, or no longer used but still active.
In detail, to find the targets, the group analyzes the Internet looking for machines listening on RDP port 3389, thanks to tools such as Msscan.exe14 able to find vulnerable machines across the Internet in less than six minutes.
Once a vulnerable target is found, the group proceeds with a brute force attack using tools like NLbrute.exe15 or ForcerX16, starting with common usernames such as “admin”, “administrator”, “guest” or “test”. After successfully gaining access to a network, the team analyzes the compromised machine to verify its Internet connection and processing capacity. It then checks whether the machine meets certain requirements before using it to conduct subsequent RDP attacks against other targets. This tactic, which has not been observed in similar groups, gives them access to additional infrastructure that is less likely to block them so that they can have a good game of leaving their tools running on compromised machines for months on end by establishing Command and Control channels.17 (C2C) with which to check the infrastructure.
After disabling the security solutions, the team downloads a zip archive that contains dozens of well-known attack tools and batch files for credential theft, persistence and reconnaissance. With these tools and batch files, the team clears event logs using wevutil.exe and conducts extensive reconnaissance of machines and the network looking for new ways to move sideways using common network scanning tools. When needed, the group elevates local administrator privileges to SYSTEM using accessibility features in conjunction with a batch file or exploit-laden files named according to the Common Vulnerabilities and Exposure specification18 (CVE) found.
The group dumps the credentials of the LSASS process, using tools such as Mimikatz19 and ProcDump20, to gain access to local administrator passwords or service accounts that have elevated privileges and that can be used to launch both interactively and scheduled tasks. PARINACOTA then uses the same remote desktop session to exfiltrate the acquired credentials. The group also attempts to obtain credentials for specific banking or financial sites, using findstr.exe21 to check for cookies associated with these sites.
In light of all this, awareness cannot fail to grow, just as it is better to keep away from the slopes of a volcano and avoid building houses that could be easily destroyed, in the same way, in a connected world, in an Information scenario Technology and Operation Technology, profoundly changed, The new safety model should be based on the metaphor of the immune system this time, also considering the experience we have been experiencing in recent months due to Covid-19, rather than that of the trench, starting from the assumption "assumes already compromise".
We are therefore talking about developing all those governance, risk analysis and management, intelligence sharing and incident management initiatives that can contribute to significantly raise the cyber resilience of organizations, i.e. their ability to function even if continuously under attack, being, often, already compromised well before evident symptoms of an ongoing attack emerge, in the same way as the immune system does, which does not persist in wanting to keep threats outside the body but, having to survive in a complex and extremely dynamic environment, it identifies them in real time, classifies them and keeps them at bay thanks to continuous monitoring, dedicating precious resources only to truly dangerous pathogens, and ignoring everything that is not relevant.
How to make such a model?
First of all, by stopping "looking at the navel" and having, instead, a 360 ° view that does not drown in its logs polluted by the background noise of its networks and systems but which analyzes user behavior within and outside your network by implementing threat intelligence and in-depth monitoring processes.
Secondly, to establish a continuous Cyber Risk Management process, which evaluates all the variables at stake 24 hours a day, including those outside the perimeter, such as Social, shadow IT, IoT, and gives indications to management to define defensive strategies that can change rapidly in the face of constantly changing threats. This is completely different from continuing undeterred to carry out activities that are now outdated, such as an annual Audit, which would allow us to allocate resources efficiently.
Finally, to allocate the necessary resources to these security activities because in no field today the relationship between safety spending and the value of the asset to be protected is as low as in Information Technology (ICT).
Cyber Resilience must become not only one of the pillars of an organization's activity but that element that enables all the others and makes them possible, considering on the one hand the growing pervasiveness of ICT in today's society and on the other the corresponding threat growth. As the latest news reports teach us, these resources must be found and used as soon as possible, and the change of business model, from the fortress to the immune system, must be carried out urgently, or, inevitably, the attackers will have the upper hand, causing the community increasingly expensive damage.
1 https://iperborea.com/titolo/513/
2 https://it.wikipedia.org/wiki/I_sogni_segreti_di_Walter_Mitty
3 https://www.microsoft.com/security/blog/2020/03/05/human-operated-ransom...
4 https://www.certnazionale.it/news/2017/05/15/come-funziona-il-ransomware...
5 https://www.certnazionale.it/tag/petya/
6 https://www.cybersecurityintelligence.com/payload-security-2648.html
7https://www.microsoft.com/en-us/itshowcase/microsoft-uses-threat-intelli...
8 https://www.secureworks.com/research/revil-sodinokibi-ransomware
9 https://www.securityweek.com/samas-ransomware-uses-active-directory-infe...
10https://www.coveware.com/bitpaymer-ransomware-payment
11https://www.certnazionale.it/news/2018/08/23/il-nuovo-ransomware-ryuk-di...
12https://www.zdnet.com/article/ransomware-these-sophisticated-attacks-are...
13https://www.certnazionale.it/glossario/brute-force-attack-attacco-a-forz...
14https://docs.microsoft.com/it-it/windows/security/threat-protection/inte...
15https://www.hybrid-analysis.com/sample/ffa28db79daca3b93a283ce2a6ff24791...
16https://www.mcafee.com/blogs/other-blogs/mcafee-labs/rdp-security-explai...
17https://www.paloaltonetworks.com/cyberpedia/command-and-control-explained
18https://en.wikipedia.org/wiki/Common_Vulnerabilities_and_Exposures
19https://www.ilsoftware.it/articoli.asp?tag=Mimikatz-il-programma-per-rec...
20https://docs.microsoft.com/en-us/sysinternals/downloads/procdump
21https://en.wikipedia.org/wiki/Findstr












