Speaking of anonymity on the net need browsing the Dark Web Tor is often referred to. In the common imagination, Tor is seen both as an Internet communication method to enable online anonymity and as a tool for accessing the "dark network". It is therefore necessary to clarify some of the myths.
The first substantial difference concerns the fact that the browsing the Dark Web is profoundly different from the browsing in incognito, also called "private browsing", which is offered as an option on all browsers. This difference should be emphasized because, too often, it is the subject of some false beliefs: Incognito browsing simply has the advantage of not saving the browsing history, cookies, site data and information entered in the site modules but is very far from guaranteeing real anonymity to the surfer.
The Internet Service Provider tracks all activities in each case, knows the IP address and can identify the location of the Internet user.
Furthermore, incognito browsing does not allow us in any way to enter the Dark Web which represents a world apart from the Web that we all browse.
Deep Web e Dark Web they are two different worlds
Dark Web e Deep Web they are two very different worlds and in a certain sense not communicating with each other. In fact, it is good to underline how we all routinely sail in the Deep Web which, by definition, indicates the set of pages on the web that are not indexed by common search engines such as Google, Bing, etc. It includes new sites, web pages with dynamic content, web software, corporate private sites, networks peer-to-peer.
The opposite of the Deep Web is called surface web which is made up, instead, of pages indexed by search engines. Therefore, Deep e surface web they are the two sides of the same coin with the difference that the first is not indexed and, therefore, we can only reach it if we know the URL. Let's consider Deep Web the page of our Facebook profile, as well as the web page of our Hotmail box and the websites of Cloud Service Providers where our files are stored as well as the many corporate, government, financial pages for internal use only, present on the web, but not indexed. The image, where the web is represented as an iceberg, effectively illustrates the concepts expressed.
Il Dark Web instead, it is a very small fraction of the web. It is a separate and inaccessible world that relies on darknet which are closed networks to access which require special configurations. The main ones darknet I'm:
- Freenet, little used;
- I2P;
- Tor, The Onion Router, which has now become the most famous and used of these networks.
It is important to point out that browsing the Dark Web it has nothing to do with the browsing in incognito of browsers. Traditional browsers, in fact, do not allow us to access the Dark Web. To enter the Dark Web we need appropriate tools. The best known and used browser is "Tor" which we try to describe to get to know it better and to dispel a false myth: browse the Dark Web it is not illegal, unless it is used for illegal actions.
Tor
La Darknet Tor it has existed since 1998 when the US Navy made it using the "onion routing" technology developed to guarantee anonymity. In 2006 it was made public and in the same year it was born Tor Project Inc., a non-profit organization based in the USA. It is an infrastructure hardware dedicated and made up of server that host it. Today Tor is headed by Bruce Schneier, world-renowned cryptographer and security technologist whose blog, dedicated to the topics of cyber security, is among the best known and most popular in the world. The organizations that constitute Tor Project are, among others, the US Department of State Bureau of Democracy, the Human Rights and Laboratory. Therefore, I would say it is obvious how Tor Project is not a clandestine or cybercrime association. Far from it, as, however, can be read on the site: “Defend yourself against tracking and surveillance. Circumvent censorship ".
For these reasons, Tor is a communication network used mostly by journalists, political activists and whistleblowers less democratic countries where it is necessary to circumvent censorship and surveillance to express one's opinion. The fact that it is also used by the "bad guys" does not affect its value. It is, without a doubt, the network darknet most popular and well-known and is used around the world by over 750.000 Internet users every day.
Tor infrastructure
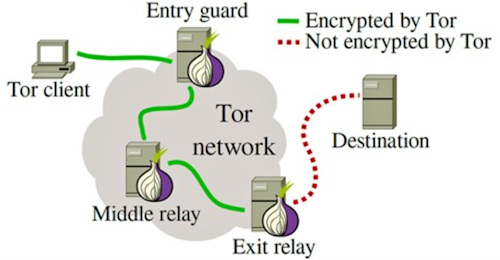
The Tor network consists of several thousand server scattered around the world. Specifically, we are talking about a number that is between 6.000 and 8.000 "relays" and almost 3.000 "bridges", almost all managed by volunteers. Browsing data does not flow directly from the client to the server but the transit passes through i relay Tor operating from router, thus creating a layered encrypted virtual circuit, exactly like an “onion”, hence the name Onion.
For this reason, the URLs of the Tor network have the TLD, Top Level Domain, which is not the classic .com or .it but .onion. When you start browsing by opening the Tor browser, three nodes are randomly chosen to form a navigation chain.
In each step, the communication is encrypted and this happens for each node. Furthermore, the fact that each node on the network only knows the previous and the next makes it difficult to be able to trace the starting client. There are three types of relay in the Tor navigation system:
- guard / middle relay;
- exit relay;
- bridge.
As we said, for security reasons, Tor traffic goes through at least three relay before reaching its destination. The first is the guard relay, the second is a middle relay which receives the traffic and finally passes it to theexit relay.
I relay intermediate, guard and middle, are only visible within the Tor network and, unlike the output relay, do not make the owner of the relay as the source of the traffic. This means that a relay intermediate is generally safe. We may also have it in the server of our home, thus becoming a node of the Tor infrastructure. The relay exit is the last node Tor traffic passes through before reaching its destination.
The services that Tor clients connect to, such as the website, chat service, email provider, etc. they will see the IP address of the egress relay instead of the Tor user's real IP address. This means that it is the IP address of the egress relay that is interpreted as the source of the traffic.
The topography of the Tor network is completed with i bridge. It is important to know that the structure of the Tor network provides that IP addresses of relay Tor are public. Therefore, if a government or ISP wanted to block networks, they could easily do so by blacklisting the IP addresses of these public Tor nodes. For this reason there are i bridge which, being nodes that are not listed on the public list as part of the Tor network, make it more difficult for governments and ISPs to block the entire network. THE bridge are essential tools for circumventing censorship in countries that regularly block the IP addresses of all relay Tor listed publicly, such as China, Turkey and Iran.
In fact, they are used instead of the entry node, normally referred to as server of a given country, to prevent the ISP from knowing that you are using Tor.
To use Tor through i bridge it is necessary to know in advance the address of at least one bridge. Tor project distributes the IP addresses of the bridge by various means, including the website and email.
It is clear that, in this way, it is possible that an adversary also obtains this information and it is for this reason that, beyond the protection measures used by Tor Project, the best thing is to find in another country a trusted person or an organization that maintains, for those who request it, a bridge clouded "private". In this case, private means that the bridge is configured with the option PublishServerDescriptor 0. Without this option, the Tor Project will know of the existence of the bridge and he could distribute his address to other people who, in this way, would risk ending up in the hands of an opponent.
You can set the use of bridge from the network configuration of the Tor browser.
 When the welcome window appears, click on the "+" and in the dialog box, under "Additional Settings" choose "Network Configuration" and then select the option "Configure a Tor bridge or local proxy".
When the welcome window appears, click on the "+" and in the dialog box, under "Additional Settings" choose "Network Configuration" and then select the option "Configure a Tor bridge or local proxy".
I bridge they are less stable and tend to have lower performance than other entry nodes.
The Tor network relies on volunteers to offer their servers and bandwidth. Anyone, therefore, can make their own computer available to create a relay of the Tor network. The current Tor network is underpowered by the number of people using it, which means Tor needs more volunteers to increase the number of relays. Managing a relay Tor, as explained on the dedicated page of the site Tor Project, you can help improve the Tor network by making it:
- faster and, consequently, more usable;
- more robust against attacks;
- more stable in case of outages;
- safer for its users because spying on multiple relays is harder than spying on a few.
There is one last aspect to consider, however peculiar and which represents a not negligible problem: safety comes at the expense of speed. The "world tour" that the data flow will have to make, as we have explained, will make navigation slow. So don't think about using Tor for streaming, file sharing or for activities that require large data streams.
How secure and anonymous is Tor?
In theory it should be safe and guarantee the anonymity of those who use it. In practice there are doubts - even well founded - about its real safety. On the same Tor Project site, on the support page, to the question: “Am I completely anonymous if I use Tor?”, The following answer is given: “In general, it is impossible to have total anonymity, even with Tor. Although there are some practices to put in place to increase your anonymity, while using Tor, but also offline. Tor doesn't protect all of your computer's internet traffic when you use it. Tor only protects applications that are configured correctly, so they can pass their traffic through Tor ”.
That said, while Tor is anonymous in theory, in practice the "exit nodes", where traffic leaves the secure "onion" protocol and is decrypted, can be established by anyone, including government agencies. Anyone who manages an exit node can then read the traffic passing through it.

And in fact, alas, for more than 16 months, we have seen the addition of server to the Tor network in order to intercept traffic and perform attacks on SSL stripping to users who access sites where cryptocurrencies are operated.
The attacks, which began in January 2020, consisted of adding server to the Tor network and mark them as "output relays", which, as explained above, are i server through which traffic leaves the Tor network and re-enters the public Internet after being anonymized.
these server they were used to identify traffic to cryptocurrency websites and carry out a SSL stripping, which is a type of attack aimed at downgrading traffic from an encrypted HTTPS connection to plaintext HTTP.
The most likely hypothesis is that the attacker downgraded the traffic to HTTP in order to replace the IP addresses of the server of cryptocurrency with their own and thus hijack transactions for personal profit.
The attacks are not new and they have been documented and first exposed last year, in August, by a security researcher and Tor node operator known as nusenu.
At the time, the researcher said that the attacker had managed to flood the Tor network with malicious Tor output relays on three occasions, bringing the peak of their attack infrastructure to about 23% of the output capacity of the entire Tor network. before being closed since Tor team.
But in one new research recently published and shared with the record, Nusenu said that although their operations were publicly exposed, the threats continued and are still ongoing.
According to Nusenu, the attacks reached and exceeded a quarter of the Tor network's entire output capacity on two occasions in early 2021, peaking at 27% in February 2021.
The second wave of attacks was detected, just like the first, and the malicious Tor exit relays were removed from the Tor network, but not before the attack infrastructure was alive and intercepting Tor traffic for weeks or months.
The main reason the attacks worked for more than a year was because the malicious actor added malicious output relays "in small doses" thus managing to hide within the network and build the malicious infrastructure over time. .
The latest attack was spotted, however, quickly due to the fact that the output capacity of the Tor network had gone from about 1.500 output relays a day to more than 2.500, a value that nobody could ignore.

Although more than 1.000 have been removed server, Nusenu also said that as of May 5, 2021, the attacker still controls between 4% and 6% of the entire output capacity of the Tor network, with attacks from SSL stripping still in progress.
In August 2020, the Tor Project has issued a number of recommendations on how website operations and Tor Browser users could protect themselves from this type of attack. Users who use the Tor browser to access cryptocurrency or other financial sites are advised to follow the advice provided on the site.
It is clear that there is no infrastructure that cannot be attacked and that the attacks are aimed, more and more, at hitting areas of growing interest such as, as reported in the article, the cryptocurrency market.
In short, no one can be considered safe. Not even with the browsing in incognito.












