Last March 29 La Repubblica published an article whose incipit was this: “The current health and social crisis, triggered by COVID-19, has led to an exponential increase in the number of people who work from home, who adopt smart-working to safeguard public health. At the same time, there is an increase in cybersecurity risks. This is mainly due to two factors. On the one hand, the redeployment of workstations outside the office and the increase in the use of virtual collaboration platforms greatly expand the base of potential attacks. This could threaten the digital infrastructure we rely on today more than ever for business continuity. If not addressed proactively, it could even threaten critical infrastructure and the delivery of critical services. On the other hand, the COVID-19 crisis offers cybercriminals new opportunities for targeted attacks, be it phishing emails or other scams. These tactics aim to take advantage of the most vulnerable situation people find themselves in, as they are obviously concerned about their own health and safety. "
Personally I agree in half with what is reported by the well-known newspaper as the attacks we are witnessing affect, for the vast majority, private infrastructures which, alas, suffer from the weaknesses they have always suffered and which, in a period such as this, in which they are subjected to continuous stress, show all their weakness.
In this regard, in fact, I would like to talk to you about securing desktop virtualization platforms which is one of the most used and which, if not properly configured, represent a huge risk for all those who do not like or do not want to use those cloud with all due respect to the investment portfolio in Hardware and Software, literally thrown away.
Security Guide for Remote Desktop Adoption
The rapid increase in the smart working over the past two or three months has led many companies to rush to understand how infrastructures and technologies would be able to handle the increase in remote connections. Many companies have been forced to improve their capabilities to allow remote access to business systems and applications, very often, relying on remote access through the use of the remote desktop protocol, which allows employees to log in directly to workstations and systems.
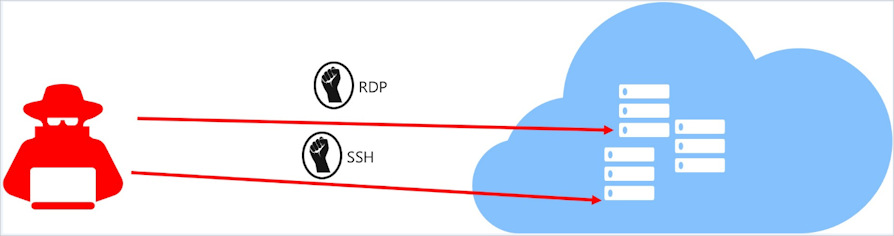
Recently, John Matherly, founder of Shodan, the world's first search engine for Internet-connected devices, conducted some analyzes on ports accessible via the Internet from which some important innovations emerged. In particular, there has been an increase in the number of systems accessible via the traditional port related to the use of the protocol Remote Desktop Protocol (RDP) and through a well-known "alternative" port used for RDP. We could say that John's research had the effect of highlighting a massive use of the RDP protocol and its exposure to the Internet.
Although Remote Desktop services can be a quick way to enable access to systems, a number of potential security concerns need to be considered before using Remote Desktop becomes the ultimate remote access strategy. This is because, as reported in a previous article of mine (Parinacota eCyber Resilience), the attackers try to exploit the protocol and the related service, to compromise corporate networks, infrastructures, systems and data.
Therefore, it is necessary to make some security considerations for the use of the remote desktop and to focus attention on a series of elements that must, necessarily, be part of the strategy to mitigate the risks regarding the use of RDP and that we can summarize in:
- Direct accessibility of systems on the public Internet.
- Vulnerability and patch management of exposed systems.
- Internal lateral movement after initial impairment.
- Multi-factor authentication (MFA).
- Session security.
- Remote access control and registration.
With regard to these considerations, I analyzed the use of Microsoft Remote Desktop Services (RDS) as a gateway in order to grant access to the systems. The gateway uses Secure Sockets Layer (SSL) to encrypt communications and prevent the system hosting the remote desktop protocol services from being exposed directly to the Internet.
To identify whether a company uses these services, it is necessary to perform a policy check on the firewall and scan the addresses exposed on the Internet and the services used, to identify any exposed systems. Firewall rules can be labeled "Remote Desktop" or "Terminal Services". The default port for Remote Desktop Services is TCP 3389, the one used by the RDP protocol, although, at times, it is possible to use an alternative port such as TCP 3388 in case the default configuration has been changed.
 The Remote Desktop Service can be used for session-based virtualization, for the Virtual Desktop Infrastructure (VDI) or for a combination of these two services. Microsoft Remote Desktop Service (RDS) can be used to protect local deployments, cloud deployments and remote services from various Microsoft partners such as Citrix, for example. Using RDS to connect to local systems improves security by reducing the exposure of systems directly to the Internet.
The Remote Desktop Service can be used for session-based virtualization, for the Virtual Desktop Infrastructure (VDI) or for a combination of these two services. Microsoft Remote Desktop Service (RDS) can be used to protect local deployments, cloud deployments and remote services from various Microsoft partners such as Citrix, for example. Using RDS to connect to local systems improves security by reducing the exposure of systems directly to the Internet.
The infrastructure could be local, cloud or hybrid depending on needs, network bandwidth availability and performance.
The experience that arises from using Virtual desktop can be improved by taking advantage of the Windows Virtual Desktop service, available on Microsoft Azure. Defining a cloud environment simplifies management and offers the ability to scale virtualization services for virtual applications and desktops. The use of Windows Virtual Desktop, net of any performance issues due to local network connections that must be addressed with the increase in the availability of network bandwidth, takes advantage of the security and compliance features inherent in the Azure platform.
Secure remote administrator access
Remote Desktop Services are used not only by employees for remote access, but also by many system developers and administrators to manage the systems themselves and cloud and local applications. Allowing administrative access to server and cloud systems directly via RDP poses a risk because the accounts used for these purposes typically have higher access privileges to physical and logical systems and infrastructures, including system administrator access.
In this sense, the use of the Microsoft Azure cloud helps system administrators to access securely using Network Security Groups and Azure Policies, allowing secure remote administration of services thanks to the JIT (Just-In-Time) access features. ).
JIT access improves security through the following measures:
- Approval workflow
- Automatic access removal
- Restriction of the IP address allowed for connection
Risk assessment
Considerations for selecting and implementing a remote access solution must always take into account the organization's security factor and risk appetite. The use of remote desktop services offers great flexibility allowing remote workers to have an experience similar to that of working in the office, offering some separation from threats on endpoints (for example, user devices, managed and not managed by the 'organization). At the same time, these advantages should be compared with the potential threats to the corporate infrastructure (network, systems and therefore data). Regardless of the implementation of remote access used by the organization, it is essential to implement best practices to protect identities and minimize the attack surface to ensure that no new risks are introduced.
Images: US Air National Guard / Microsoft