The Quantum Key Distribution (QKD) Challenge
The Quantum-Secure Net (Q-Secure Net) project is a funded project of the European Institute of Technology Digital (EIT Digital) whose aim is to develop and bring to the market a completely European new generation and new generation network product, based on Quantum Key Distribution (QKD) technology, which is sustainable in terms of cost and interoperable with other existing systems. The aim of the project is to provide a telecommunications ready solution, integrated into network operation and management, to ensure quantum-level secure end-to-end (E2E) communications in high-security settings.
Proposed already in the early 1980s, QKD is a technology related to quantum computing due to the fact that it uses the same mathematical "terminology": it can be said that in this case we speak of "quantum" without the "computing" attribute . The technology has taken nearly 40 years to evolve, however, it is now a major area of technology competition among nations beyond 5G including China, Korea and the United States. QKD in particular uses the quantum properties of photons to exchange a symmetric cryptographic key, which can be used to encrypt messages which are then exchanged through a "traditional" channel. The security of QKD is based on fundamental laws of nature, which are insensitive to increasing computing power, new attack algorithms or quantum computers. This system allows, once introduced, to equip the highly secure network infrastructures with unconditionally secure communications.
The Q-Secure net project
The Q-Secure Net project aims to provide a cost-effective and flexible solution for unconditionally secure QKD-based communication services that work with existing fiber-optic metropolitan networks. The project leader is Italtel. Among the partners, Cefriel followed two of the application scenarios, Politecnico di Milano and CNR developed the QKD technology and error correction protocols, Polytechnic University of Madrid and Telefonica participated in the definition of the product and the tests on the metropolitan fiber optic network .
During the project, two prototype applications were developed, with the aim of demonstrating their use in the Blockchain and SSL context, showing how QKD technology can be applied both to the financial market and to secure IoT (Internet of Things) and IIoT communications. (Industrial IoT). The product is suitable for any service that requires a symmetric encryption key, and opens up to countless applications and use cases.
The SSL + PSK scenario
The first application developed is linked to the SSL / TLS protocol. These protocols allow secure communication between two entities by operating above the transport layer. Usually, SSL uses public key certificates for authentication. In particular, however, the standard already provides a special configuration (SSL + PSK Pre-Shared Keys) which uses symmetric keys, pre-shared in advance between the communicating parties, to establish an SSL connection. A configuration implemented, for example, to support cases in which the communicating parties cannot use asymmetric encryption because it is expensive in terms of connectivity or calculation (eg IoT) or because the parties are already "accredited" (eg military).
The detailed communication steps for SSL + PSK are as follows, directly inspired by the proposed Diffie-Hellman scheme for PKI.
-
Alice and Bob receive the same (symmetric) cryptographic key on a QKD link
-
Alice uses the QKD symmetric key to encrypt a temporary session key, randomly generated, which has a limited lifespan and sends it to Bob, over an insecure channel (ethernet)
-
Bob receives the message and decrypts it to get the temporary session key.
-
Alice and Bob use the temporary session key with AES to encrypt their messages over ethernet until it expires (then step 2 is repeated). In the event of an attack through the QKD link, Alice and Bob can request another secure QKD key.
The scenario is enabling for VPN and IPSEC services with QKD.
The Decentralized Finance scenario
Blockchain technologies were born at the end of 2009 with the advent of the Bitcoin protocol and evolve to this day in a family of protocols and SW systems essentially with the aim of creating a network (peer to peer network) of "peers" in able to exchange a transactional value (currency, asset with value, certification) directly, without a fiduciary third party. Thus eliminating, through the mechanism of shared consent, the need for third parties and activating the direct exchange of goods and services. These systems have an application in the financial field, both in interbank processes, for example in asset tracking and life cycle scenarios such as invoices (e.g., invoice discount) and in processes and services that can be created from tokens ( giving rise to the phenomenon of decentralized finance).
In particular, in the Decentralized Finance (Defi), one of the key aspects is the interoperability of systems and the exchange of tokens and cryptocurrencies, subject to known and considerable security challenges. Today there are tens of thousands of Ethereum derivative tokens, and they are “technically” interoperable with each other, which means that different applications can exchange these tokens just like exchanging currencies or stocks on the trading exchanges. These operations today are entrusted to centralized Exchanges which are often subject to security problems and represent the only element still centralized in systems which are, however, totally peer-to-peer.
In this "financial" context, there is always a "node" in the network, called wallet in technical jargon (wallet) which is enabled to exchange the value, i.e. the token. This node has specific information that allows it to execute the transaction.
Furthermore, in current Fintech scenarios, there are multiple cryptocurrencies and networks, a recognized weakness. The "transition" from one cryptocurrency to another, from one token to another, between two systems wallet, requires the transition to a trusted third party, contradicting the decentralization paradigm. This situation, for example in the Ethereum context, is solved by passing, in some cases, as recently proposed, through the mechanism ofAtomic Swap. THE'Atomic Swap is one of the possible solutions proposed to make different blockchain networks interact, and is a "system" for the secure passage directly between nodes participating in different blockchain networks, of information (hashlocks o time lock*) required to unlock the currency exchange.
This symmetrical information allows to couple different networks, and it is therefore important, in view of the evolution of blockchain networks in financial contexts, to keep it secure.
In the experimental configuration object of the project, theAtomic Swap takes place no longer on a "common" telecommunication network, but uses a QKD Link, which allows the transfer parameter of hashlock / timelock between two nodes of an Algorand network (note that in the jargon Algorand the term Atomic Transfers). This solution increases the intrinsic safety of the exchange and therefore makes it possible to use Atomic Swap even with cryptocurrencies.
Expected developments
In one year, the Q-Secure Net project led to the creation of a product ready for the first market applications, but which has the potential to seize the opportunities from a rapidly growing market. In the article, a first natural scenario of use of the QKD was mentioned, for connections with high safety requirements or where the everlasting security.
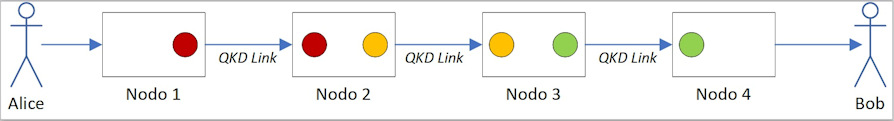
Networks of devices equipped with QKD Link are also interesting. A first "hop-by-hop" network architecture was demonstrated in Europe in 2008 by the SECOQC project; in such networks the messages pass through different relay nodes connected by QKD Link. In this case the decryption / recoding and relaying of the message is carried out at each intermediate node with different QKD keys (see Figure 1).
* CEFRIEL Polytechnic of Milan, Viale Sarca 226 - 20126 Milan
+ Italtel, Via Reiss Romoli - loc. Castelletto - 20019 Settimo Milanese (Mi)
|
[1] |
Digital Tech, “Q-Secure Net Factsheet,” 2019. [Online]. Available: https://www.eitdigital.eu/fileadmin/files/2020/factsheets/digital-tech/E.... |
|
[2] |
R. Alléaume, C. Branciard, J. Bouda, T. Debuisschert, M. Dianati, N. Gisin, M. Godfrey, P. Grangier, T. Länger, N. Lütkenhaus, C. Monyk, P. Painchault, M. Peev, A. Poppe, T. Pornin, J. Rarity, R. Renner, G. Ribordy, M. Riguidel, L. Salvail, A. Shields, H. Weinfurter and A. Zeilinger, “Using quantum key distribution for cryptographic purposes : A survey, " Theoretical Computer Science, vol. 560, pp. 62-81, 2014. |
|
[3] |
W. Diffie and M. Hellman, "New directions in cryptography," IEEE Transactions on Information Theory, vol. 22, pp. 644-654, 1976. |
|
[4] |
M. Herlihy, “Atomic Cross-Chain Swaps,” in ACM Symposium on Principles of Distributed Computing, 2018. |
|
[5] |
S. Micali, “Algorand's Forthcoming Technology,” 26 5 2019. [Online]. Available: https://medium.com/algorand/algorands-forthcoming-technology-bcd17989c874. |
|
[6] |
CORDIS, “Development of a Global Network for Secure Communication based on Quantum Cryptography,” 2008. [Online]. Available: https://cordis.europa.eu/project/id/506813. |
* The Atomic Swap service can be configured in two ways: hashlock or timelock. Hashlock is a function that limits the spending of funds until certain data is made public (as cryptographic proof. Timelock limits the spending of funds until a certain time in the future.
The Quantum-Secure Net Project (part 1/3): The quantum threat to modern cryptography
The Quantum-Secure Net project (part 2/3): European product of Quantum Key Distribution












