The technological impact on social and economic life is not the subject of choices, but it is inevitable, for better or for worse, to limit oneself only to undergoing this radical and inevitable process of transformation of society corresponds to the inability to fully grasp its advantageous aspects, which are many. In this sense, the choice between whether or not to be technology consumers is not free or optional. Those who do not invest in technological development choose a path not only of economic, but also social and cultural decline.
Man and his safety must be the first concern of any technological adventure.
Yesterday's geopolitics dealt with geography as a fundamental element for establishing the real possibilities of movement of armies and for the necessary supply lines, for the possibility of establishing commercial traffic by sea and by land, which can be defended in a simple and inexpensive way. In the digital age, geopolitics deals with telecommunication networks, submarine cables, hubs and landing points through which internet traffic passes, the possible manipulation of voters through the use of social and big data, attacks cybernetics to critical infrastructure that may be able to bring an entire country to its knees.
These are scenarios that can shift the center of gravity of the spheres of influence and, as is normal, also a lot of business. The understanding of all this cannot but pass from the necessity that everything that is cyber must be treated as a problem of risk management and not as a problem of the IT function only, as, unfortunately, still too often it happens.
Before getting to this, however, I would like to clarify once and for all the concept of cybersecurity and, in this regard, let's use the definition given by NIST:
"Prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation"
Starting from this definition and including the area in which we move, over the last decade, there has been a lot of talk, and often inappropriately, of cyber security and the paradigm for which cyber security constitutes the latest major global challenge involving individuals, companies, states and international organizations. Affirming this at the time of covid-19 makes you smile but that's it. Calling it a challenge, however, would presuppose an articulated plan of countermeasures which, if implemented, will be able to overcome the problem by leading the victim towards the final goal, free from any concern.
Cyber security is not a challenge nor is it the challenge of the XNUMXst century. Cyber security constitutes a journey, a road, probably, very articulated that foresees different intersections and, definitely, no finish line, rather, perhaps, of the "positive" stages which, if completed, will not completely reset the journey.
This image, although linked to the security strategy offered by Microsoft which is not the desire of the writer to advertise, gives a good idea of the journey that must be undertaken.
If cybersecurity isn't the XNUMXst century challenge, then what is it? We can say that what for society 4.0 constitutes a concrete and problematic threat are cyber attacks, identified in the ten most probable and highest impact risks by the Global Risks report made again this year by the World Economic Forumi.
Cyber risk is the real threat that individuals, companies, states and international organizations are called to face in the new era dominated by industry 4.0.
The need to create new business models to increase the productivity of industries has led to a general trend towards automation, computerization, virtualization, the cloud and towards all the functionalities present in the mobile world. The combination of these characteristics defines industry 4.0 to which the various social components are called to relate and on which the risk of cyber attacks operates.
In this scenario, think of associating cybersecurity with the world ofInformation Technology it makes you smile while, on the contrary, knowing that the area in which you operate is much wider, helps to understand the risks and, hopefully, to prevent them.
Probably many will remember the news of the annexation by Russia of the Ukrainian region of Crimea, which occurred in February and March 2014. That news shocked the whole world and represented a surprise also for many analysts and experts who monitored and are still observing the Russian activity. Some of those experts, however, understood in advance what the strategy was.
In particular, Volker Kozokii, lieutenant colonel and computer security expert of the German armed forces, was one of those and his role, still today, is to keep track of threats related to digital security by trying to develop the correct countermeasures. This has always allowed Kozok to have a privileged view of the current scenario that we could define as hybrid war, extremely complex, but which deserves great attention.
Many times we have heard this sentence: "Today's military conflicts rarely take place only on the battlefield with conventional weapons". Quite the contrary. When we talk about conflicts, among them we must always include cyber attacks on critical infrastructures as well as the various forms of so-called "weaponized information"iii”, Destined to sow confusion and insecurity in the population.
In the case of the invasion of Ukraine by Russia, what Kozok and his colleagues noticed in January 2014 was a kind of clandestine opening from Russia. They observed that Russia was installing what appeared to be a submarine cable across the Kerch Strait, a strait between the Black Sea and the Sea of Azov. While monitoring the progress of the laying of that 46 kilometer long cable, it became evident that the arrival point of that cable would be the Crimean peninsula.
The existence of the cable suggested that Russia was making a move to connect Ukraine's critical infrastructure with its own. In particular, it appeared that the Russian cable would bring high-speed internet communications that could bypass Ukrainian service providers.
Kozok team members managed to reinforce this deduction through the sophisticated use of geographic information systemsiv (GIS). They were able to examine cable construction through localization by showing submarine cables worldwide and connecting nodes to the Internet. From all this, the team was able to deduce that Russia aimed to control online communications. In the annals of the war, this represented a decisive moment.
"It was the first time that a country had organized a military attack while planning, in an extremely clever and intelligent way, the implementation of communication networks through a marine cable," explained Kozok during an interview. "Someone had to drive up to the Crimea as if he were a simple tourist, before the invasion, and precisely identify the cable entry point. They had to carry out those plans without actually still having control of the country.
Russia continued to employ hybrid warfare techniques in Ukraine. Russian hackers launched a cyber attack on the Ukrainian electricity grid in 2015, cutting electricity to 250.000 people. Almost exactly a year later, hackers caused another blackout.
It is now widely clear that cyber attacks pose a danger and go beyond the "computer" target. Cybersecurity concerns critical infrastructures, including utilities, which form the basis of communities.
The world's ability to promote collective action in the face of a growing series of serious challenges has reached significant levels of crisis with the worsening of international relations. In the meantime, a slowdown in the economic outlook, also caused by geopolitical tensions, seems destined to further reduce the potential for international cooperation.
Complex social, technological and work-related transformations are having a profound impact and among the global threats indicated in the fifteenth edition of the Global Risks Report, promoted by the World Economic Forum, cyber risk stands out.
The world is facing an increasing number of complex and interconnected challenges, from the slowdown in global growth, through persistent economic inequality to climate change, geopolitical tensions and the accelerated pace of the fourth industrial revolution.
Leading exponents of Marsh & McLennan, longtime strategic partners, have reiterated that persistent underfunding of critical infrastructure around the world is hindering progress, leaving businesses and communities more exposed to cyber attacks and natural disasters, failing to exploit the maximum defense capabilities.
Technology continues to play a profound role in shaping the global risk landscape for individuals, governments and businesses.
The new "instabilities" are caused by the deepening of the integration of digital technologies in every aspect of life.
An example of this is the revelation that the US government made about a July 2018 hacker attack through which the attackers managed to gain access to the control rooms of some public service companies. The potential vulnerability of critical technological infrastructures has increasingly become a national security problem, so much so that the second most frequently cited interconnection of risks in the 2020 report is the association of cyber-attacks with the possible sabotage of critical IT infrastructures.
This is why there has never been a more urgent need for a collaborative and multi-stakeholder approach to the global problems of "interconnected and globalized societies".
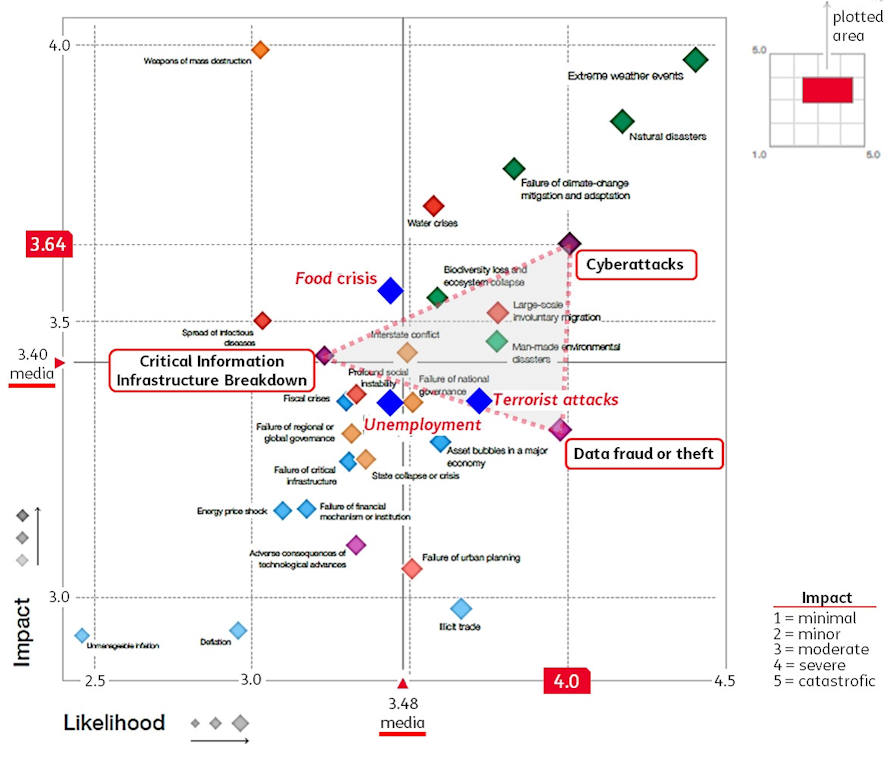
The cyber risk cluster creates a sort of triangle positioned in the upper right quadrant of the map (at the bottom of the article).
And here, the concept of computer risk comes into play, very well explained in the article "Macro Dynamics of Cyber Risk"v. IT risk is defined as the scalar product between the severity, understood as impact, of the consequences that a cybernetic event would determine and the probability that such a dangerous event, that is the threat, will occur and therefore: R = I x P
The risks are therefore assessed by determining the extent of the potential damages on the system that the threat could cause in the event of its occurrence, considering the probability that the threat always causes the greatest possible damage to its occurrence. The consequences of the same on the system also depend to a large extent on the value of the assets concerned and the examination of the consequences for each type of threat represents another aspect of the risk analysis. The cybernetic risk level must always be considered as a relationship between the risk itself and the enhancement of the associated IT asset.
As with many diseases, cyber risk is amplified, indeed, it "feeds" on other digital factors that are closely related to each other.
From 2017 to 2020, the global population will go from 7,7 to 7,8 billion people growing by 100 million units (+ 1%), while the "population" of IOT devices connected to the network will go from 8,4 billion to 20,4 billion with an increase of 12 billion objects (+ 242%) which, I believe, makes clear the measure of the enormous speed at which the digital world travels. Extreme speed is, therefore, the main feature that characterizes digital ecosystems and that significantly affects cyber risk. Everything is consumed in a hurry and consequently, the life cycle of technologies is drastically reduced.
After 2008 we witnessed the rapid growth in the number of constantly connected devices, an economy that increasingly depends on Artificial Intelligence algorithms, the growth of the power of social media and the risk of fake news, the growth in the exploitation of personal content due to the increasingly forward movement of the trade-off between privacy and service.
And in this context, undoubtedly, there are at least two factors, among others, that play a fundamental role in cyber risk:
- The human factor
- Complexity, obsolescence and patching
The human factor is certainly one of the main risks and is also a paradox. On the one hand, the digital revolution has in many ways strengthened our abilities: through social networks it has offered us the opportunity to entertain many relationships at the same time, to always have our say on issues that only two decades ago would have remained most relegated to the circle of closer friends.
On the other hand, on the other hand, it has given us negative aspects such as the polarization of opinions, haters, trolls, fake news, in short, an excellent context for "destroying" consensus but not able to "build" it at all. In this world that travels at the speed of light, these super individuals whose abilities are enhanced by the Internet and social networks, surprisingly, find themselves extremely vulnerable to social engineering, phishing, pretexing, etc. which are confirmed to be the most frequently used channels when triggering even complex attacks. Of all the cases that have occurred, I believe that the one that most of all had a huge echo, is certainly the Cambridge Analytica scandalvi.
The links between politics, technology, social impact and data manipulation are represented in what has been the history that best shows how the technological risk is enormous if not guided for good purposes. Regarding the scandal, I like to report from the complaint book “The dictatorship of datavii”, The words of Brittany Kaiserviii, the mole that helped to make the world known how user data in social networks are used to manipulate and threaten democracy:
- “And so, I had found myself part of the major operation conducted by Cambridge Analytica, which consisted of collecting as much data as possible about US citizens and exploiting them to influence American voting intentions. I could have realized how Facebook's inadequate privacy policies and the federal government's total lack of control over personal data made this possible. But above all, I understood that Cambridge had used his resources to get Donald Trump elected. "
- "They know what you buy. They know who your friends are. They know how to manipulate you. Seventy likes was enough to know more about that person than what his friends knew; one hundred and fifty likes more than what his parents knew; three hundred likes more than his. partner. Over three hundred people were able to know an individual better than they knew themselves. "
As for the second factor, the constant updating of the layers of the system software on which the applications base their functioning, is a fundamental condition to reduce vulnerabilities and, consequently, the surface exposed to a potential attacker. Updating a system software release is called patching. Very often, both for the hardware obsolescence that does not support the new system software releases and for the obsolescence of the applications that need interventions, often "important" to be able to work with the new releases, the activity patching cannot be performed. Therefore, a series of constraints are generated which considerably weaken the system as a whole. If then, as often happens, obsolescence is connected to a high complexity of the infrastructural scenario, then the solution of the problem becomes enormously more complex if not structurally not possible unless using cloud solutions that, at least, help to mitigate the problem .
In short, the context is complex and in many areas we find ourselves defenseless. We must prepare for the fact that a significant portion of cyber risk cannot be mitigated but must be managed with other strategies. If the mitigation option has become more difficult to implement, the concept of risk tolerance must also be redefined. We may be forced to coexist with a high level of risk even if our risk tolerance is relatively low and, therefore, by obligation and not by business choice. The boards of directors of companies must be aware of this situation in order to make the most appropriate decisions in relation to the priority business segments. We know that the fact of being subjected to a cyber attack is not a question of "if" but only of "when". We also know that "total security" is not an achievable category and that our opponents are unknown and enjoy many strategic advantages. By ourselves we can only move blindly with little chance of success. Together, however, we can recover many disadvantages and get to get the better of our opponents.
What is needed, therefore, is a solid global roadmap that is part of a global "call to action" addressed to institutions, businesses and specialized industry for a commitment to accept the challenge of cyber threats and, possibly, to overcome it. It is certainly not a simple challenge to win but, taking inspiration from the words of President JFKix, "A community accepts the challenges it faces precisely because they are not simple, because they give us the opportunity to capitalize on the best of our abilities and our commitment".
i http://www3.weforum.org/docs/WEF_Global_Risk_Report_2020.pdf
ii https://www.esri.com/about/newsroom/blog/german-cybersecurity-experts-us...
iii https://www.sciencedirect.com/science/article/pii/S0167404819301579
iv https://www.esri.com/en-us/what-is-gis/overview
v https://www.ictsecuritymagazine.com/articoli/macro-dinamiche-del-rischio...
vi https://it.wikipedia.org/wiki/Cambridge_Analytica
vii https://www.amazon.it/dittatura-dei-dati-Brittany-Kaiser/dp/8869056988
viii https://en.wikipedia.org/wiki/Brittany_Kaiser
ix https://it.wikipedia.org/wiki/John_Fitzgerald_Kennedy
Photo: web












