Work often leads me to engage in conversations with clients on CyberSecurity, their programs, their understanding of what security means and how to implement it in their organizations.
Among the various themes, one particularly recurring is represented by the Cyber Threat Intelligence.
Having been on the market for seven to eight years now, they are often seen as the Holy Grail for identifying an interested attacker before he attacks or, at worst, as soon as signs of compromise appear. endpoint or networks.
Let's start from a simple definition of Intelligence - elaboration of predictive information based on certain evidences - to learn from the military world how to prevent investments in even important CTIs from having a zero return.
In the military environment, the information gathering phase is preceded by another one of crucial importance and too often underestimated: planning and management, in which the command bodies define the information objectives deemed necessary for their own decisions.
This is so that the collection is not an end in itself or a broad spectrum, but extremely targeted and focused; already 2500 years ago a famous Chinese military strategist - Sun Tzu - recommended to know your enemy and yourself, in that order!
Know yourself it means having a precise and complete visibility of how one's digital biodiversity is composed: where the resources are, what type they are (mobile elements, servers, cloud resources, application containers, web applications…).
Then define its observability: is it possible to fragment and reassemble, aggregate and detail, interrogate and abstract accessible information from the metadata on the digital environment, based on one's use cases?
And once you have inventoried your IT horizon, how easy is it to assign a criticality level to resources?
This means knowing yourself, and it is conditio sine qua non in order to proceed with the know your enemy that defines the way to consume CTI.
Which in the military field is divided into three phases: Processing, Production of Information, Dissemination. Three phases that have little or nothing to do with the CTI supplier, but which frequently see very promising projects failing both in terms of budget and quality of the feeds.
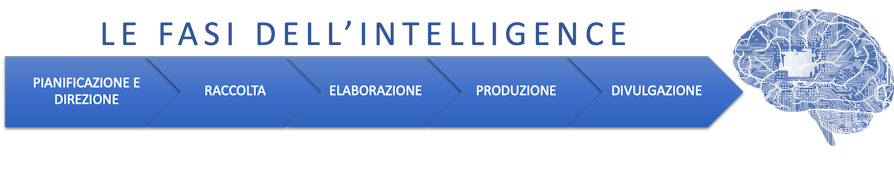
THEprocessing it concerns the ability to categorize the feed information, to correlate them with each other and with third party information, to evaluate its importance. This ability must be present and possibly exercised with own resources, since speed, agility and dynamism are important characteristics to generate value.
La information production further expands what was qualified in the previous phase, transforming inhomogeneous data into usable information thanks to the analysis of normalized metadata.
Complete the consumption cycle of cyber threat intelligence the stage of disclosure, which consists in the distribution of the re-elaborated information to support the greatest number of possible processes.
These last two phases require in-depth knowledge of the potential users of the information, as well as a technological platform that supports the transformation.
Finally, it helps to understand the three possible types of cyber threat intelligence that characterize the collection operation, in order to prefigure categorization and consumption models in the processes mentioned below - as well as determining the degree of obsolescence of the information.

The first type is the Strategic CTI: composed of analysis and information that have a typically multi-year duration, it focuses on the who and the why in relation to certain attackers.
Usually developed for a non-technical audience, it is based on the analysis of victimological demographics, on macroscopic attack campaigns and aims at the classification of attack groups and motivations (hacktivism, finance, politics, sponsored by states…). There are various categorisations, for example the one provided by Mandiant (part of the FireEye group) based on acronyms that contain the motivation and a progressive number: APT for Advanced Persistent Threat, FIN for Financial, etc.
The second type is the Operational CTI, focused on exposing the how and the where. Developed for both technical and non-technical users, it describes elements such as tools, techniques and procedures - or TTPs - used to conduct an attack.
It exhibits characterizing traits such as persistence, communication techniques used, description of methodologies and rules.
For example, it illustrates social engineering techniques or modus operandi of malware families.
The third type is the CTI tactics, which represents both the most digestible form and the one whose consumption requires less maturity. Aimed at a technical audience, it describes security events, examples of malware or phishing emails.
Includes signatures to recognize malware and indicators of attack or compromise (IoA, IoC) such as IPs, domains, file hashes, which can be easily implemented to raise perimeter, monitoring and response defenses to block attempts or mitigate situations of compromise.
If it is true that the complete use of the three forms is often a problem more of need than of budget, even when these two conditions are satisfied the question becomes another.
A virtuous process must lead to mutual coordination between the outcomes of the three different feed levels, which must not work as "silos": the feeds of the strategic level can be used to guide and refine the information search at the operational and tactical level; similarly, specific intelligence findings at the tactical level can aid in redefining the informational objectives of strategic level research.
This situation is sometimes aggravated by the lack of communication skills between the technical management level and the strategic level, with a direct impact on the planning and management phase which affects the definition of clear and shared objectives; thus polluting the entire value, in favor of expenses for redundant systems or technologies or only useful for the solution of a specific problem.
I conclude this brief analysis with three questions therefore, to help understand which type, feed, or supplier of CTI is right for you.
Are the objectives that the CTI collection supports clear, well defined in substance and perimeter?
What is the ability to consume the three types of CTI? Even over time, this response can evolve and expand
Are the resources and level of specialization to consume CTI in a tangible and value-producing way available in sufficient measure?
As in the military, so in the CyberSecurity the honest answer to these three questions will qualify the need and nature of CTI, so that - to paraphrase Sun Tzu - knowing yourself as the enemy, even in the midst of a hundred battles you are never in danger.












