If you just read the news on the cyber space (and related attacks) we are led to think that these problems are typical of the civilized world and have nothing to do with the weapon systems of the most advanced states. Addressing to more specific information structures in the world cyber, such as the SANS Institute, it turns out that even US weapons systems are vulnerable.
It is in the newsletter of the SANS institute I read about the US government report spelled out by the "Governmental Accountability Office" for the US Senate entitled "Weapon System Cybersecurity, DOD just beginning to grapple with scale of vulnerabilities".
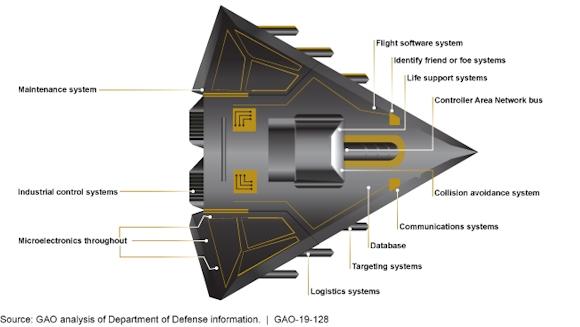
The report analyzes the critical aspects of the armaments sector and highlights the weaknesses of some systems, especially the older ones realized when there was still little evidence of the potential of a Cyber attack.
The fact that a system is newly designed and implemented does not protect against security problems. The complexity, the interdependence from other systems, the need to provide functional updates and sometimes the discovery of vulnerabilities related to basic software (the case of operating systems for example) forces the industry and the Defense to resume more and more times the systems to carry out the appropriate corrections.
The report is therefore an excellent document to understand the risks to which a modern weapon system is subject and how to proceed to avoid macroscopic errors starting from the fact that "cybersecurity is the process related to the protection of information and information systems through the prevention, detection and response to attacks. Cybersecurity aims to reduce the likelihood of an attacker gaining access to DoD systems and limiting the damage it could do if they could access it.".
The report reports some potential negative effects that can be exploited by opponents with capacity to Cyber attack, against weapon systems that are somewhat software-dependent, from the most trivial ones such as the possibility of turning on and off a weapon system or changing a missile target to more elaborate attacks such as changing the correct oxygen level of a fighter pilot.
The US plans to invest around 1.600 billion dollars in the coming years and the risks associated with new technologies and potential vulnerabilities cyber they are considered high. This led them to set up structures and control processes to limit economic damage and project failure but also allowed them to gather data on software and vulnerabilities in invaluable weapon systems.
One might wonder if something similar is put in place in other countries, for example in ours, where investments are naturally lower as they are tailored to the ambitions and objectives to be achieved but, precisely for this reason, they are much more likely to be in danger of failure. In the USA, if a project fails, it is very likely that there will be another with similar objectives that will come to fruition, but from us (or more generally in small and medium-sized European countries) the failure of a project of a weapon system would probably lead to the failure to achieve operational capacity with the consequences that can be imagined.
All this leads us to think that the only viable solution is to overcome the existing distances (and sometimes created artfully!) among European countries and implement common programs: the alternative is to remain linked to policies of the great powers and also to their "dictates" in the economic field and development of the military industry and new technologies.
To learn more:
- https://www.sans.org/
- https://www.gao.gov/assets/700/694913.pdf